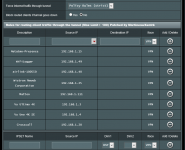
I didn't have x3mRouting on the 384 and then upgraded to the 386. I started with the 386, added AMTM, Entware, flexqos, skynet, diversion and then unbound. I use all my devices in VPN with ExpressVPN. I created the tunnel rules so that the flexqos can recognize the traffic and optimize it. Everything was fine but I found that unbound exposes DNS. At this point following a tutorial here on the site I installed x3mRouting and made it pass DNS requests directly into the VPN Everything works. As you can see below I created the tunnel and the rules in Merlin. When I installed x3mRouting I installed all its functions and I realized that if I install point 2 then I can no longer make any changes to the VPN configuration page. Even simply deactivating the VPN server creates a configuration error and it is no longer possible to activate it. To reactivate it or to change the settings, I have to uninstall point 2 of x3mRouting, make the changes, reinstall point 2 and restart the router. I also tried to do a master reset of client 1 vpn and reconfigure everything from scratch, if point 2 is installed you can't do anything, if it is uninstalled, you can configure.
My idea was to put my devices in the tunnel but to remove all the rules in Merlin and put them in x3mRouting, unfortunately if point 2 is installed it is not possible. Below you see my current configuration. Everything works, x3mRuoting does its duty like the other addons but you can't touch anything if point 2 is installed