FreshJR
Very Senior Member
It is frustrating seeing my Xbox downloads being treated as game traffic
Any reason this out of the box script rule didn't take care of it?!? (doubt the download was UDP)
Code:
iptables -A POSTROUTING -t mangle -o br0 -m mark --mark 0x80080000/0xc03f0000 -p tcp --sport 80 -j MARK --set-mark ${Default_mark_down}
iptables -A POSTROUTING -t mangle -o br0 -m mark --mark 0x80080000/0xc03f0000 -p tcp --sport 443 -j MARK --set-mark ${Default_mark_down}Eg. If Gaming traffic && coming from ports 80/443 -->redirect into "Defaults" container which I repurposed for "Game Downloads"
Very curious as to why it that rule didn't hit.
I had a look at implementing per-device fairness and its very difficult to do alongside Adaptive QoS as requires a complete restructure of how the classes are implemented and becomes very fragile. It could be done with a completely custom script avoiding adaptive QoS, but would be hard to make generic and reusable (where FreshJR does a good job of hooking into Adaptive QoS).
We can implement a per-device equal bandwidth QOS system (with no traffic prioritization) easily if not wanting to use AdaptiveQOS at all.
You said combining both per-device and traffic prioritization made the system fragile.
Out of curiosity, did you try implementing fair-bandwidth allocation and then within each fair-bandwidth queue did you create an HTB to prioritize traffic by type?
(This is a pic of what I am explaining to make it easier to visualize).
EDIT:
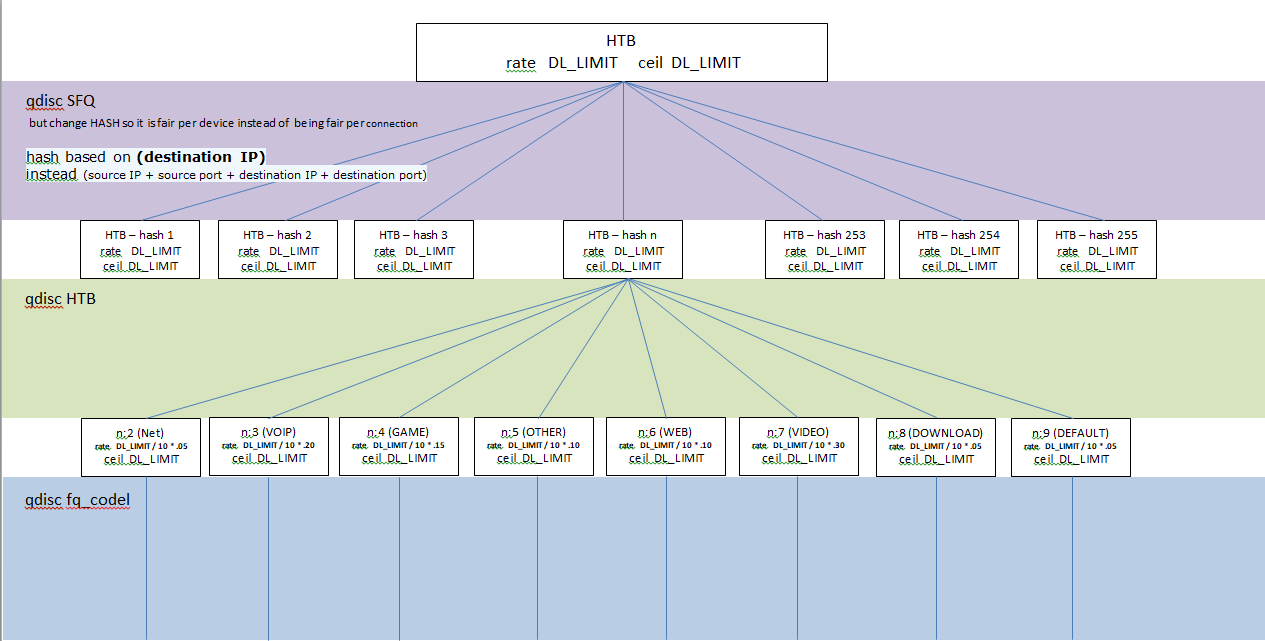
I just decided not to even try due to the sheer number of HTB's created. I was worried about performance. But that setup would allocate bandwidth evenly per connected device, and then each devices queue would then be filtered/prioritized based on traffic classification. I just felt like that structure is WAYY to big. ((Is that additional layer of traffic prioritization really necessary with equal per device bandwidth??))
---
The current structure is one where each device is shares a part of the traffic allotted within the 8 traffic categories. It's not bad except asus has glitched the device prioritization feature due to poorly assigned rates. These become a problem when one device has a higher priority than another. This was fixable with the fakeTC approach but I decided not to fight the AdaptiveQOS system any furthur. Fixing the first set of rates was sufficient for a giant improvement.
Last edited: