Jauger
Occasional Visitor
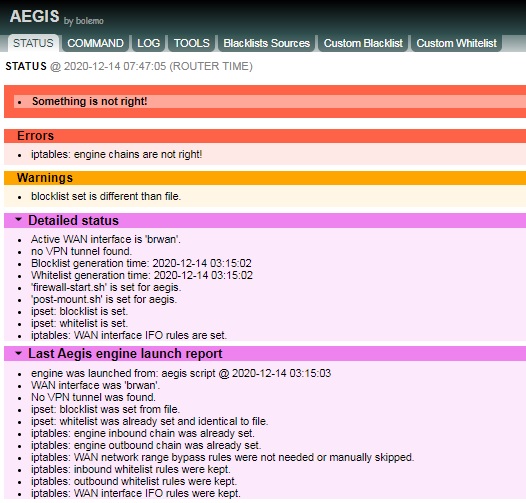
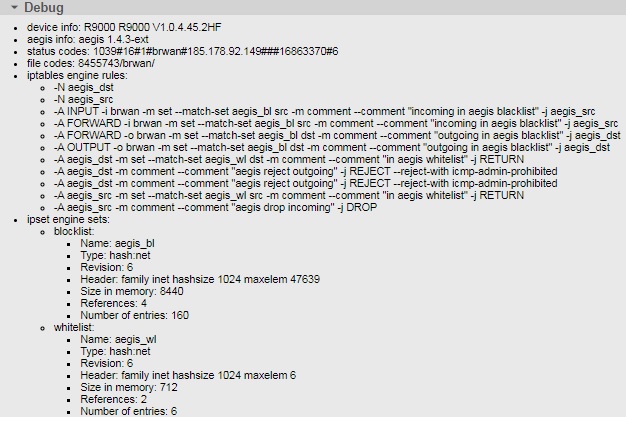
this is what I am getting
- Something is not right!
- iptables: engine chains are not right!
- iptables: whitelist rules are not right!