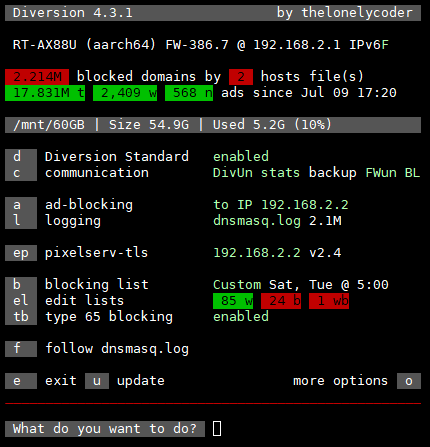
Diversion 4.3.1 is now available
What's new
- Adds option to block type 65 queries in
tb using iptables.
Thanks for all the contributors in these threads - and surely elsewhere:
I have what is pretty much a standard AMTM install of diversion, skynet, yazfi, and some others on my ac86u (all fw and scripts up to date). It's been working fine using DOT for a while. I decided to give unbound a try today. After following the first page instructions, it seems a bunch of...

www.snbforums.com
Hi, I'm running RT-AC88U and for the last few months or so (March time) I'm getting ads mostly on devices including in-app ads used to always be blocked and worked fine. Like Instagram sponsored posts (stories) or just apps that require to watch an "advert" to download or pop-up ads like Vellum...

www.snbforums.com
Hello, Very new here. Just installed Diversion lite. I can see it is working via ethernet but not blocking anything with Wifi? What am I doing wrong? My main upstream dns is Quad9 with forward DNS to upstream dns selected no

www.snbforums.com
iOS 14 and newer, as well as a growing number of apps or devices use the type 65 query.
Dnsmasq currently has no option to suppress or specifically handle these types of queries and therefore circumvent Diversion ad-blocking.
How to update Diversion
Use
u or the WebUI function to update to this latest version.