Discy
Occasional Visitor
Hi all,
After some great buying advice I'm ready for the next step .
.
Question
Could you provide some information/link to guides on how to properly configure PfSense and other devices for this setup? (picture attached). Maybe some terms, highlevel view or best practices would suffice to find what I need in the Netgate docs.
Equipment
I'm kinda lost in the terms, available guides and opinions while my setup seems pretty basic.
I'd like to do it according to best practices and be flexible without overcomplicating but don't know how/where to find the right information.
For example - when I dealt with sending all traffic via a VPN gw-group I found 3 guides that all used different methods. Some used tagfilters for everything. This didn't feel right to me and I solved it without - but I honestly couldn't be sure if it was a good or bad guide.
Example questions/network requirements:
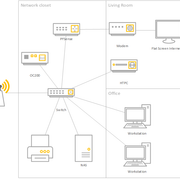
After some great buying advice I'm ready for the next step
Question
Could you provide some information/link to guides on how to properly configure PfSense and other devices for this setup? (picture attached). Maybe some terms, highlevel view or best practices would suffice to find what I need in the Netgate docs.
Equipment
- Switch: TL-SG108PE
- Cloud Controller: OC200
- AP: EAP245
- PFsense running on an x86 gateway
- Pretty broad consumer networking/all-in-one routers
- First glance of Pfsense
- As a programmer I seem to be a quick learner, but missing knowledge that might be considered as basics. For example, no idea about vlans or subnets.
I'm kinda lost in the terms, available guides and opinions while my setup seems pretty basic.
I'd like to do it according to best practices and be flexible without overcomplicating but don't know how/where to find the right information.
For example - when I dealt with sending all traffic via a VPN gw-group I found 3 guides that all used different methods. Some used tagfilters for everything. This didn't feel right to me and I solved it without - but I honestly couldn't be sure if it was a good or bad guide.
Example questions/network requirements:
- Where to enable/disable DHCP
- What IP's should be static?
> I guess shared devices like my NAS, CC, AP's, PFSense and any device I want to create rules for. Via DHCP MAC binding. - In what way (exact steps I can figure out) to set-up the NAT/Routing/Gateways/subnets(?)/vlans(?).
- Add the TV as part of main network to access the NAS via modem
- Use my modem as a second switch in the livingroom
- Set bandwidth limit per device (NAS eats upload on backup)
> trafficshaper? - Route some devices/ips around my VPN Gateway-group directly to WAN (OC200/Netflix TV)
> add fw-rule to LAN with IPs-alias in source seems clean?

Last edited:
