learning_curve
Senior Member
I have an Asus RT-AC86U C1 router running Merlin v386.5_0. It's running very well indeed.
I have an IVPN account, so I can run the IVPN App if / when needed on any suitable device (desktop / laptop / smartphone) on the LAN without any issues at all e.g. I have no big connection speed penalties / No DNS Leaks etc & the IPVN App works very well indeed. It allows the choice of using either Open VPN and/or WireGuard protocol, but with many additional config options on these protocols too (including IPv6 over IPv4 with Wireguard). IF... I was only wanting to use these types of devices, I wouldn't need to ask the question in the thread title. I am asking said question, because... other other devices e.g. Samsung UHD TV etc run software & software apps but App choices are far more limited than the normal computing devices and this limitation includes, loading any VPN Apps and allowing them to function properly. Thus, Geo-Location say, can sometimes become an unnecessary annoyance on these devices. My 'solution' is to use any of these devices, on VPN that's been provided by my router via my LAN, using a suitable set of VPN Director Rules, specific for that device (fixed IP address).
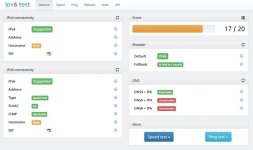
However, because I use IPv6 everywhere else, all of the time, all of the test attempts of my "solution" that I have made so far on a MacBook Device, using OpenVPN Client 1, always fail. That's fail in terms of the IPv4 connection via OpenVPN Client 1 to the chosen IVPN server working fine, but... The same VPN connection also provides an IPv6 connection which is exactly the same as any Non-VPN connection via my router. Lots of tests confirm this, but ironically, I can still score 20/20 with ipv6-test.com despite the IPv4 being an IVNP server and the IPv6 being by own router! DNS4 + IP6 and DNS6 + IP4 and DNS6 + IP6 all being fully reachable...
That obviously means I do have a mis-config somewhere in my VPN OpenVPN Client (in order to exclude the IPv6 data) or, it's just not possible to do this? (Yet)
The option to simply switch of IPv6 on the router itself is there and would definitely fix this, but I do use IPv6 a lot elsewhere, so I've already discounted this option.
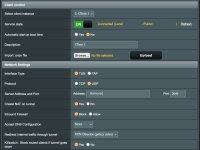
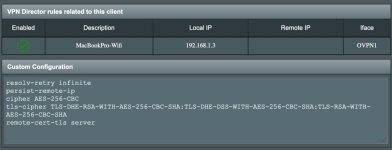
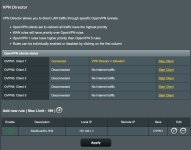
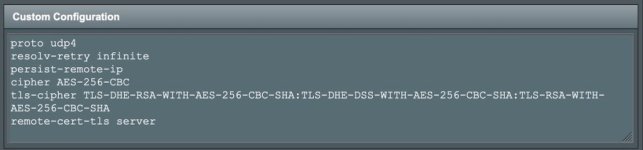
All of the current configuration that I use, that (I think) is relevant to this, is as follows:
I don't use any plug-ins, except those shown in my forum signature and I don't have anything on a USB that's also used for the router's operation. I have IPv4 DDNS with Asus and IPv4 & IPv6 DDNS with No IP, but full, effective DDNS IPv6 functionality is still a TBA from Asus (then Merlin in due course). The router on this firmware is the best it's ever been and I have no other issues or problems with anything else, anywhere. #GoodTimes! I haven't - yet - seen that is a simple setting with IPv6 Data - ON or OFF, but I didn't expect to either in fairness. I'd really like to resolve this one (if I can) so if somebody can spot the "obvious" that I have missed, great!
I have an IVPN account, so I can run the IVPN App if / when needed on any suitable device (desktop / laptop / smartphone) on the LAN without any issues at all e.g. I have no big connection speed penalties / No DNS Leaks etc & the IPVN App works very well indeed. It allows the choice of using either Open VPN and/or WireGuard protocol, but with many additional config options on these protocols too (including IPv6 over IPv4 with Wireguard). IF... I was only wanting to use these types of devices, I wouldn't need to ask the question in the thread title. I am asking said question, because... other other devices e.g. Samsung UHD TV etc run software & software apps but App choices are far more limited than the normal computing devices and this limitation includes, loading any VPN Apps and allowing them to function properly. Thus, Geo-Location say, can sometimes become an unnecessary annoyance on these devices. My 'solution' is to use any of these devices, on VPN that's been provided by my router via my LAN, using a suitable set of VPN Director Rules, specific for that device (fixed IP address).
However, because I use IPv6 everywhere else, all of the time, all of the test attempts of my "solution" that I have made so far on a MacBook Device, using OpenVPN Client 1, always fail. That's fail in terms of the IPv4 connection via OpenVPN Client 1 to the chosen IVPN server working fine, but... The same VPN connection also provides an IPv6 connection which is exactly the same as any Non-VPN connection via my router. Lots of tests confirm this, but ironically, I can still score 20/20 with ipv6-test.com despite the IPv4 being an IVNP server and the IPv6 being by own router! DNS4 + IP6 and DNS6 + IP4 and DNS6 + IP6 all being fully reachable...
That obviously means I do have a mis-config somewhere in my VPN OpenVPN Client (in order to exclude the IPv6 data) or, it's just not possible to do this? (Yet)
The option to simply switch of IPv6 on the router itself is there and would definitely fix this, but I do use IPv6 a lot elsewhere, so I've already discounted this option.
All of the current configuration that I use, that (I think) is relevant to this, is as follows:
- LAN -> DNS Server 1 -> Blank
- LAN -> DNS Server 2 -> Blank
- LAN -> Advertise router's IP in addition to user-specified DNS -> No
- LAN -> DHCP Server - Enhanced by YazDHCP - Manually Assigned IP Addresses -> Yes (For All)
- WAN -> Connect to DNS Server automatically -> No
- WAN -> DNS Server 1 -> 1.1.1.1
- WAN -> DNS Server 2 -> 1.0.0.1
- WAN -> Forward local domain queries to upstream DNS -> No
- WAN -> Enable DNS Rebind protection -> Yes
- WAN -> Enable DNSSEC support -> Yes
- WAN -> Validate unsigned DNSSEC replies -> Yes
- WAN -> Prevent client auto DoH -> Yes
- WAN -> DNS Privacy Protocol -> DNS-over-TLS(DOT)
- DNS Filter is enabled -> Global Filter Mode -> Router
- WAN -> DNS-over-TLS Profile Strict -> Strict
- WAN -> DNS-over-TLS Server List (1.1.1.1 1.0.0.1 2606:4700:4700::1111 2606:4700:4700::1001)
- Administration - System -> Network Monitoring -> DNS Query
- Administration - System -> Resolve Hostname -> localhost
- Administration - System -> Resolved IP Addresses -> 127.0.0.1
- IPv6 -> Auto Configuration Setting -> Stateless
- IPv6 -> Connect to DNS Server automatically -> Disable
- IPv6 -> IPv6 DNS Server 1 -> LAN IPv6 Link-Local Address
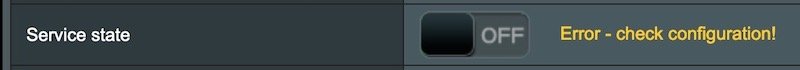
- VPN Client -> See attached images
- VPN Director rule -> See attached image
I don't use any plug-ins, except those shown in my forum signature and I don't have anything on a USB that's also used for the router's operation. I have IPv4 DDNS with Asus and IPv4 & IPv6 DDNS with No IP, but full, effective DDNS IPv6 functionality is still a TBA from Asus (then Merlin in due course). The router on this firmware is the best it's ever been and I have no other issues or problems with anything else, anywhere. #GoodTimes! I haven't - yet - seen that is a simple setting with IPv6 Data - ON or OFF, but I didn't expect to either in fairness. I'd really like to resolve this one (if I can) so if somebody can spot the "obvious" that I have missed, great!
Attachments
Last edited: