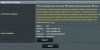
Yesterday my certificate expired, The date said 2019/10/6, but it did not autoupdate, I tried to restart my router but It still said 2019/10/6. Then i tried to disable lets encrypt in the gui, and re enable it again, then it got a certificate that says it's expire on 2029/10/7 ?? But if i try to reach my host it still says certificate not valid.
If i Restart the router again, it's back to 2019/10/6. Very weird behaviour, I'm upgraded some weeks ago to 384.13_1 I have a RT-AC87U.
After i Enable/reenable I see nothing confusing in the log
Oct 7 10:04:25 rich710: DDNS Request URL: https://www.duckdns.org/update?domains=rich71&token=xxxxx
Oct 7 10:04:26 rich710: DDNS Request result: OK
But after a reboot this is showing up:
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: SSL_read return 5: Success
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: https://acme-v01.api.letsencrypt.org/acme/new-reg: bad comm
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: transfer buffer: [{ "VYQGeYcCZuM": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417", "key-change": "https://acme-v01.api.letsencrypt.org/acme/key-change", "meta": { "caaIdentities": [ "letsencrypt.org" ], "terms-of-service": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf", "website": "https://letsencrypt.org" }, "new-authz": "https://acme-v01.api.letsencrypt.org/acme/new-authz", "new-cert": "https://acme
Oct 7 10:19:10 kernel: /usr/sbin/acme-client: SSL_read return 5: Success
Oct 7 10:19:10 kernel: /usr/sbin/acme-client: https://acme-v01.api.letsencrypt.org/acme/new-authz: bad comm
Any ideas what's wrong?
Regards
//Richard

If i Restart the router again, it's back to 2019/10/6. Very weird behaviour, I'm upgraded some weeks ago to 384.13_1 I have a RT-AC87U.
After i Enable/reenable I see nothing confusing in the log
Oct 7 10:04:25 rich710: DDNS Request URL: https://www.duckdns.org/update?domains=rich71&token=xxxxx
Oct 7 10:04:26 rich710: DDNS Request result: OK
But after a reboot this is showing up:
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: SSL_read return 5: Success
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: https://acme-v01.api.letsencrypt.org/acme/new-reg: bad comm
Oct 7 10:19:08 kernel: /usr/sbin/acme-client: transfer buffer: [{ "VYQGeYcCZuM": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417", "key-change": "https://acme-v01.api.letsencrypt.org/acme/key-change", "meta": { "caaIdentities": [ "letsencrypt.org" ], "terms-of-service": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf", "website": "https://letsencrypt.org" }, "new-authz": "https://acme-v01.api.letsencrypt.org/acme/new-authz", "new-cert": "https://acme
Oct 7 10:19:10 kernel: /usr/sbin/acme-client: SSL_read return 5: Success
Oct 7 10:19:10 kernel: /usr/sbin/acme-client: https://acme-v01.api.letsencrypt.org/acme/new-authz: bad comm
Any ideas what's wrong?
Regards
//Richard
Attachments
Last edited: