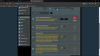
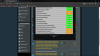
Jan 30 15:44:55 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting
Jan 30 15:45:15 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting
Jan 30 15:46:05 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting
Jan 30 15:46:25 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting
Jan 30 15:46:32 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting
Jan 30 15:47:10 ovpn-server1[2132]: rt-ac3200-ran/166.171.120.33 SIGTERM[soft,remote-exit] received, client-instance exiting