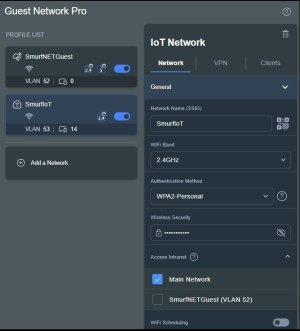
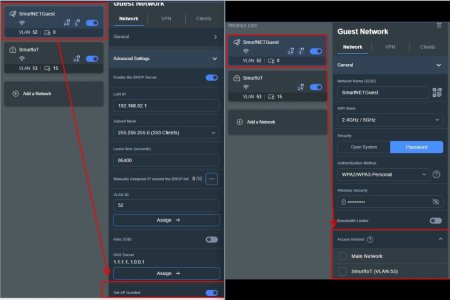
For what ever reason the Guest Network Pro on my RT-AX86U Pro gets wonky if I've added and removed a bunch of Guest Network Pro Profiles. Sometimes it doesn't show all the available settings or options in newly added Profiles. Typically what I've had to do is remove all the Profiles, reboot the router, then add each one back one at a time.
In any case here is
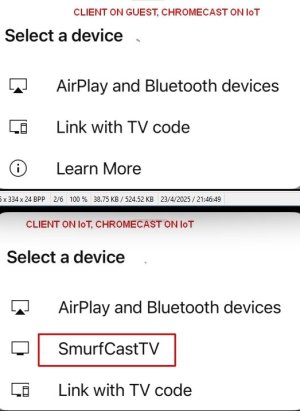
@visortgw, Just did a quick test and can successfully print to a HP Officejet printer connected to 2.4 GHz main LAN WiFi from a smartphone connected to a Guest Network IoT Profile (br53) 5 GHz network. Can ping and access the HP Officejet printer's administration GUI page as well from the Guest Network Pro IoT Profile (br53) 5 GHz network connected smartphone. I did have to access HP Printer app (on the smartphone) settings and toggle a WiFi 5 GHz option before the HP printer app would see the main LAN WiFi 2.4 GHz connected HP Officejet printer. Here are the
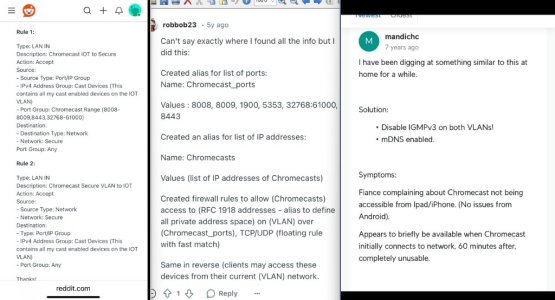
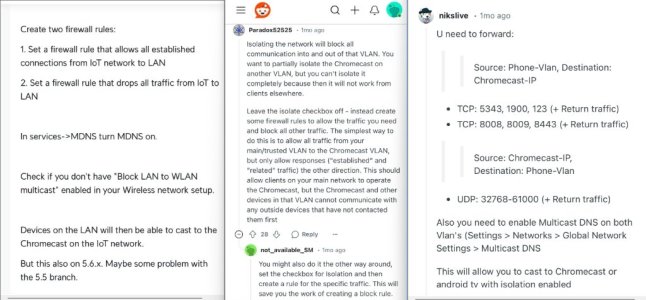
You may want to dump your IPTables to see if the firewall-start entries are getting input into the firewall's IPTables list.
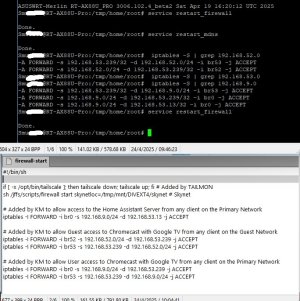
Example on my system showing the above script has input the two IPTables entries:
If the script isn't being injected into the IPTables then double check you have the firewall-start in the /jffs/scripts/ folder on the router and that it has the correct permissions (0755) so it can be executed. Then check the script itself for any errors or typo's.
In any case here is
brctl show for my setup. Redacted the bridge id device MAC address.
Code:
/jffs/scripts$ brctl show
bridge name bridge id STP enabled interfaces
br0 8000.xxxxxxxxxxc0 no eth1
eth2
eth3
eth4
eth5
eth6
eth7
br52 8000.xxxxxxxxxxc1 no eth1.52
eth2.52
eth3.52
eth4.52
eth5.52
eth6.52
eth7.52
wl0.1
br53 8000.xxxxxxxxxxc5 no eth1.53
eth2.53
eth3.53
eth4.53
eth5.53
eth6.53
eth7.53
wl1.1firewall-start script I used. 192.168.2.163 is the IP address for the HP Officejet printer, br53 192.168.53.0/24 is the Guest Network Pro IoT Profile (5 GHz).
Code:
#!/bin/sh
iptables -I FORWARD -i br53 -s 192.168.53.0/24 -d 192.168.2.163 -j ACCEPT
iptables -I FORWARD -i br0 -s 192.168.2.163 -d 192.168.53.0/24 -j ACCEPTExample on my system showing the above script has input the two IPTables entries:
Code:
/jffs/scripts$ iptables -nL | grep 192.168.2.163
ACCEPT all -- 192.168.2.163 192.168.53.0/24
ACCEPT all -- 192.168.53.0/24 192.168.2.163
Last edited: