rgnldo
Very Senior Member
Just do not understand what will be the name resolution for unbound. If so /etc/resolv.conf?, the no-resolv igonora option.The servers-file points to the WAN DNS servers
Just do not understand what will be the name resolution for unbound. If so /etc/resolv.conf?, the no-resolv igonora option.The servers-file points to the WAN DNS servers
Very good. Will it give for use Diversion?yes so in practice, if port is configured properly and forward zones set right and private, DNSMASQ can be left to do it's own local thang, and Unbound can do its job.
Unbound (in my setup without forward-zone) resolves directly with the root DNS servers and any authoritative name server for the names requested by my devices. There is no single DNS server that will get my queries. This is what a recursive resolver does versus a forwarding resolver. You become your own Google DNS, Cloudflare DNS, Level 3 DNS.Just do not understand what will be the name resolution for unbound. If so /etc/resolv.conf?, the no-resolv igonora option.
Have you checked for this traffic? Just didn't understand why you chose to add dnssec to dnsmasq. The unbound-anchor is robust.There is no single DNS server that will get my queries. This is what a recursive resolver does versus a forwarding resolver. You become your own Google DNS, Cloudflare DNS, Level 3 DNS.
That has yet to be seen. I think the way dave is testing will tell us.Very good. Will it give for use Diversion?
Here's a log of a query to asuswrt.lostrealm.ca (since snbforums.com and asuswrt-merlin.net were already cached).Have you checked for this traffic? Just didn't understand why you chose to add dnssec to dnsmasq. The unbound-anchor is robust.
Add your full configuration here for me to do the tests?
I added proxy-dnssec to dnsmasq.conf so that Unbound's secure reply will be passed down to dnsmasq without it being ignored by dnsmasq.Have you checked for this traffic? Just didn't understand why you chose to add dnssec to dnsmasq. The unbound-anchor is robust.
Add your full configuration here for me to do the tests?
server:
# port to answer queries from
port: 53
verbosity: 2
logfile: "/opt/var/lib/unbound/unbound.log"
log-queries: yes
log-replies: yes
do-ip4: yes
do-ip6: no
do-udp: yes
do-tcp: yes
# don't be picky about interfaces but consider your firewall
interface: 127.0.1.1
access-control: 0.0.0.0/0 refuse
access-control: 127.0.0.0/8 allow
access-control: 10.0.0.0/24 allow
access-control: 192.168.1.0/24 allow
# private networks:
private-address: 127.0.0.0/8
private-address: 169.254.0.0/16
private-address: 10.0.0.0/8
private-address: 172.16.0.0/12
private-address: 192.168.0.0/16
# no threads and no memory slabs for threads
num-threads: 2
msg-cache-slabs: 4
rrset-cache-slabs: 4
infra-cache-slabs: 4
key-cache-slabs: 4
so-reuseport: yes
# tiny memory cache
key-cache-size: 16m
msg-cache-size: 8m
rrset-cache-size: 8m
cache-min-ttl: 3600
cache-max-ttl: 86400
cache-max-negative-ttl: 0
infra-host-ttl: 60
edns-buffer-size: 1472
# prefetch
prefetch: yes
prefetch-key: yes
minimal-responses: yes
# gentle on recursion
hide-identity: yes
hide-version: yes
do-not-query-localhost: no
qname-minimisation: yes
rrset-roundrobin: yes
harden-glue: yes
harden-referral-path: no
harden-below-nxdomain: yes
harden-algo-downgrade: yes
# Self jail Unbound with user "unbound" to /var/lib/unbound
username: "nobody"
directory: "/opt/var/lib/unbound"
chroot: "/opt/var/lib/unbound"
root-hints: "/opt/var/lib/unbound/root.hints"
# The pid file
pidfile: "/opt/var/run/unbound.pid"
# DNSSEC and DNS-over-TLS
tls-cert-bundle: /etc/ssl/certs/ca-certificates.crt
auto-trust-anchor-file: "/root.key"
remote-control:
control-enable: yes
control-interface: 127.0.0.1
control-port: 953
server-key-file: "/opt/var/lib/unbound/unbound_server.key"
server-cert-file: "/opt/var/lib/unbound/unbound_server.pem"
control-key-file: "/opt/var/lib/unbound/unbound_control.key"
control-cert-file: "/opt/var/lib/unbound/unbound_control.pem"Very good setup organization. I tested it here.I added proxy-dnssec to dnsmasq.conf so that Unbound's secure reply will be passed down to dnsmasq without it being ignored by dnsmasq.
Here's my unbound config at the moment:
Code:server: # port to answer queries from port: 53 verbosity: 2 logfile: "/opt/var/lib/unbound/unbound.log" log-queries: yes log-replies: yes do-ip4: yes do-ip6: no do-udp: yes do-tcp: yes # don't be picky about interfaces but consider your firewall interface: 127.0.1.1 access-control: 0.0.0.0/0 refuse access-control: 127.0.0.0/8 allow access-control: 10.0.0.0/24 allow access-control: 192.168.1.0/24 allow # private networks: private-address: 127.0.0.0/8 private-address: 169.254.0.0/16 private-address: 10.0.0.0/8 private-address: 172.16.0.0/12 private-address: 192.168.0.0/16 # no threads and no memory slabs for threads num-threads: 2 msg-cache-slabs: 4 rrset-cache-slabs: 4 infra-cache-slabs: 4 key-cache-slabs: 4 so-reuseport: yes # tiny memory cache key-cache-size: 16m msg-cache-size: 8m rrset-cache-size: 8m cache-min-ttl: 3600 cache-max-ttl: 86400 cache-max-negative-ttl: 0 infra-host-ttl: 60 edns-buffer-size: 1472 # prefetch prefetch: yes prefetch-key: yes minimal-responses: yes # gentle on recursion hide-identity: yes hide-version: yes do-not-query-localhost: no qname-minimisation: yes rrset-roundrobin: yes harden-glue: yes harden-referral-path: no harden-below-nxdomain: yes harden-algo-downgrade: yes # Self jail Unbound with user "unbound" to /var/lib/unbound username: "nobody" directory: "/opt/var/lib/unbound" chroot: "/opt/var/lib/unbound" root-hints: "/opt/var/lib/unbound/root.hints" # The pid file pidfile: "/opt/var/run/unbound.pid" # DNSSEC and DNS-over-TLS tls-cert-bundle: /etc/ssl/certs/ca-certificates.crt auto-trust-anchor-file: "/root.key" remote-control: control-enable: yes control-interface: 127.0.0.1 control-port: 953 server-key-file: "/opt/var/lib/unbound/unbound_server.key" server-cert-file: "/opt/var/lib/unbound/unbound_server.pem" control-key-file: "/opt/var/lib/unbound/unbound_control.key" control-cert-file: "/opt/var/lib/unbound/unbound_control.pem"
I’m taking small baby steps. I don’t use IPv6 today on my network. DoT is only useful if you have a forward-zone configured, which I do not. So all my recursive queries to authoritative servers are cleartext.Prefer not to enable IPV6? How about DNS-over-TLS on Unbound?
I did not understand. I need to adapt my reality. I have IPV6DoT is only useful if you have a forward-zone configured
I added proxy-dnssec to dnsmasq.conf so that Unbound's secure reply will be passed down to dnsmasq without it being ignored by dnsmasq.
Here's my unbound config at the moment:
Code:server: # port to answer queries from port: 53 verbosity: 2 logfile: "/opt/var/lib/unbound/unbound.log" log-queries: yes log-replies: yes do-ip4: yes do-ip6: no do-udp: yes do-tcp: yes # don't be picky about interfaces but consider your firewall interface: 127.0.1.1 access-control: 0.0.0.0/0 refuse access-control: 127.0.0.0/8 allow access-control: 10.0.0.0/24 allow access-control: 192.168.1.0/24 allow # private networks: private-address: 127.0.0.0/8 private-address: 169.254.0.0/16 private-address: 10.0.0.0/8 private-address: 172.16.0.0/12 private-address: 192.168.0.0/16 # no threads and no memory slabs for threads num-threads: 2 msg-cache-slabs: 4 rrset-cache-slabs: 4 infra-cache-slabs: 4 key-cache-slabs: 4 so-reuseport: yes # tiny memory cache key-cache-size: 16m msg-cache-size: 8m rrset-cache-size: 8m cache-min-ttl: 3600 cache-max-ttl: 86400 cache-max-negative-ttl: 0 infra-host-ttl: 60 edns-buffer-size: 1472 # prefetch prefetch: yes prefetch-key: yes minimal-responses: yes # gentle on recursion hide-identity: yes hide-version: yes do-not-query-localhost: no qname-minimisation: yes rrset-roundrobin: yes harden-glue: yes harden-referral-path: no harden-below-nxdomain: yes harden-algo-downgrade: yes # Self jail Unbound with user "unbound" to /var/lib/unbound username: "nobody" directory: "/opt/var/lib/unbound" chroot: "/opt/var/lib/unbound" root-hints: "/opt/var/lib/unbound/root.hints" # The pid file pidfile: "/opt/var/run/unbound.pid" # DNSSEC and DNS-over-TLS tls-cert-bundle: /etc/ssl/certs/ca-certificates.crt auto-trust-anchor-file: "/root.key" remote-control: control-enable: yes control-interface: 127.0.0.1 control-port: 953 server-key-file: "/opt/var/lib/unbound/unbound_server.key" server-cert-file: "/opt/var/lib/unbound/unbound_server.pem" control-key-file: "/opt/var/lib/unbound/unbound_control.key" control-cert-file: "/opt/var/lib/unbound/unbound_control.pem"
forward-zone:
name: "."
forward-tls-upstream: yes
forward-addr: 1.1.1.1@853#cloudflare-dns.com
forward-addr: 1.0.0.1@853#cloudflare-dns.comAny idea how to add DNS OVER TLS with this setup?
forward-zone:
name: "."
forward-tls-upstream: yes
forward-addr: 185.222.222.222@853#dns.sb
forward-addr: 2a09::@853#dns.sb
forward-addr: 185.184.222.222@853#dns.sb
forward-addr: 2a09::1@853#dns.sbOnly add forward-zone at the end of the configuration file. Note that recursive will no longer be via root server's, but on forward-zone servers.Code:forward-zone: name: "." forward-tls-upstream: yes forward-addr: 185.222.222.222@853#dns.sb forward-addr: 2a09::@853#dns.sb forward-addr: 185.184.222.222@853#dns.sb forward-addr: 2a09::1@853#dns.sb
unbound-control -c /opt/var/lib/unbound/unb
ound.conf stats_noreset | grep total.num
total.num.queries=674
total.num.queries_ip_ratelimited=0
total.num.cachehits=56
total.num.cachemiss=618
total.num.prefetch=0
total.num.zero_ttl=0
total.num.recursivereplies=618If there is a better way, I will try
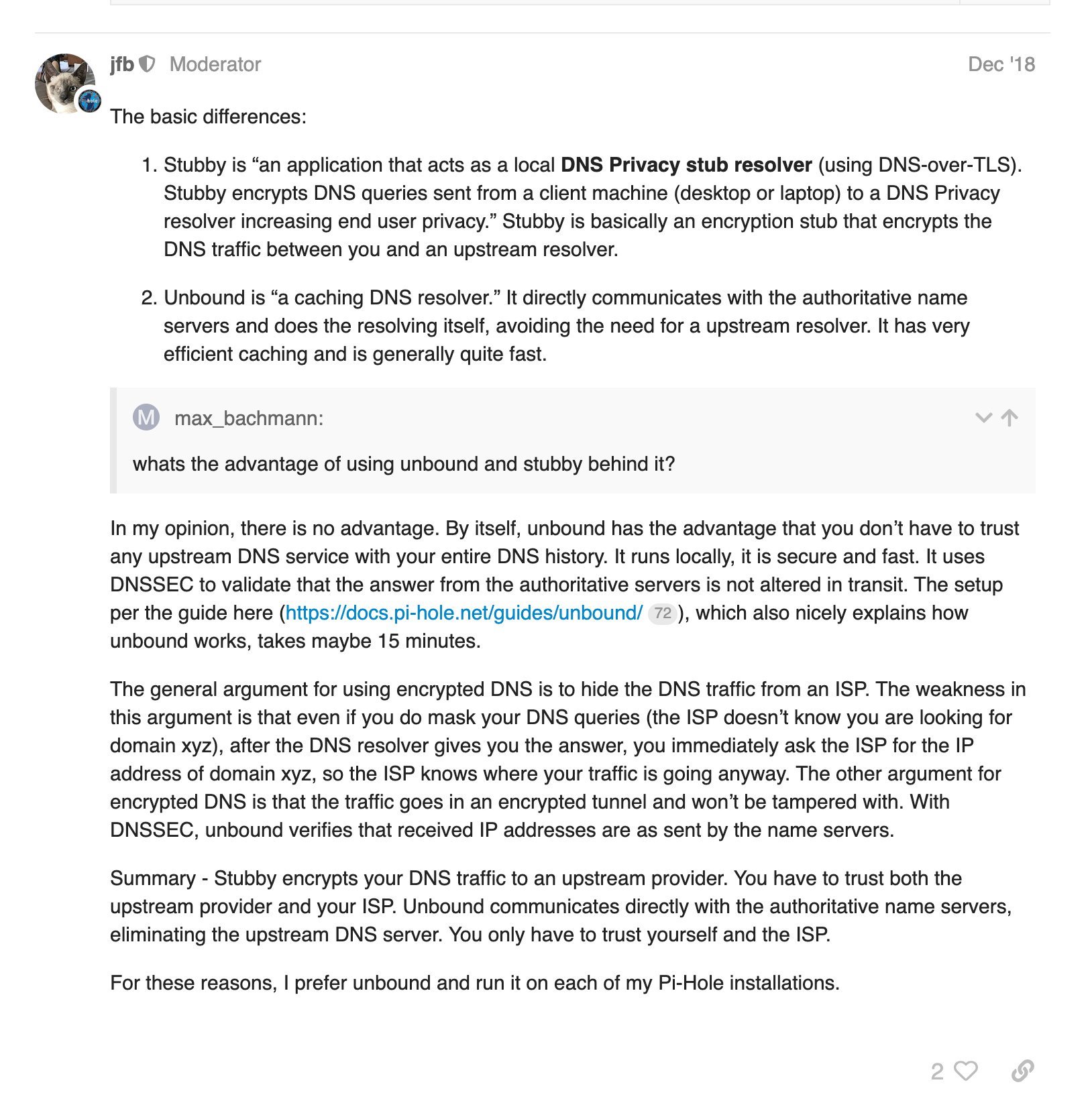
Not entirely sure, but the debate is interesting. Source: https://discourse.pi-hole.net/t/unbound-or-stubby/15432/2
(I know I need to add "include: blacklist_path.txt" but your script for some reason creates an empty blacklist.txt)
#!/bin/bash
destinationIP="0.0.0.0"
tempoutlist="/jffs/Adblock/adlist.tmp"
outlist='/jffs/Adblock/tmp.host'
finalist='/jffs/Adblock/tmp.finalhost'
permlist='/jffs/Adblock/adpermitidos.txt'
adlist='/jffs/Adblock/adservers.txt'
echo "Removing Possible Temporary Files.."
[ -f /jffs/Adblock/adlist.tmp ] && rm -f /jffs/Adblock/adlist.tmp
[ -f /jffs/Adblock/tmp.host ] && rm -f /jffs/Adblock/tmp.host
[ -f /jffs/Adblock/tmp.finalhost ] && rm -f /jffs/Adblock/tmp.finalhost
echo "Downloading StevenBlack ad list..."
curl --progress-bar https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts | grep -v "#" | grep -v "::1" | grep -v "0.0.0.0 0.0.0.0" | sed '/^$/d' | sed 's/\ /\\ /g' | awk '{print $2}' | grep -v '^\\' | grep -v '\\$'| sort >> $tempoutlist
echo "Removing Duplicate Domain list formats..."
cat $tempoutlist | sed -r -e 's/[[:space:]]+/\t/g' | sed -e 's/\t*#.*$//g' | sed -e 's/[^a-zA-Z0-9\.\_\t\-]//g' | sed -e 's/\t$//g' | sed -e '/^#/d' | sort -u | sed '/^$/d' | awk -v "IP=$destinationIP" '{sub(/\r$/,""); print IP" "$0}' > $outlist
numberOfAdsBlocked=$(cat $outlist | wc -l | sed 's/^[ \t]*//')
echo "$numberOfAdsBlocked suspicious and blocked domains"
echo "Edit list of allowed domains..."
fgrep -vf $permlist $outlist > $finalist
echo "Generating Unbound Adlist..."
cat $finalist | grep '^0\.0\.0\.0' | awk '{print "local-zone: \""$2"\" static"}' > $adlist
numberOfAdsBlocked=$(cat $adlist | wc -l | sed 's/^[ \t]*//')
echo "$numberOfAdsBlocked suspicious and blocked domains"
echo "Removing temporary files.."
[ -f /jffs/Adblock/adlist.tmp ] && rm -f /jffs/Adblock/adlist.tmp
[ -f /jffs/Adblock/tmp.host ] && rm -f /jffs/Adblock/tmp.host
[ -f /jffs/Adblock/tmp.finalhost ] && rm -f /jffs/Adblock/tmp.finalhost
echo "Restarting DNS servers..."
/opt/etc/init.d/S61unbound restartI edited the steps at the beginning of the post. See thereIt works.. my mistake
| Thread starter | Title | Forum | Replies | Date |
|---|---|---|---|---|
| H | AdGuard Home+Unbound in proxmox does not work properly with Asus AX88U Pro | Asuswrt-Merlin | 6 | |
| S | AdguardHome + Unbound on Pi4 Correct DNS settings | Asuswrt-Merlin | 6 |
We use essential cookies to make this site work, and optional cookies to enhance your experience.
