I would like to move more of our data off our laptops and onto a NAS. This data might include PDF copies of utility bills and other data I would like to keep private. Right now, we just have MP3s online, but I'm concerned about putting "important" data onto an always-on device.
This concern brought me to SNB, which has been a fantastic resource. My questions are:
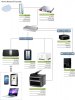
1) What VLANs should I create to segment traffic appropriately? I created a diagram with three VLANs. (See attached.)
Network - General access for laptops and tablets.
Video - Just for Roku. Don't know if a separate VLAN is needed, but this might help performance?
Data - The NAS with more important data. I would restrict access to this VLAN to certain MAC addresses.
2) What are some example IP addresses I could use? I'm assuming 192.168.1.1 for the cable modem gateway, 192.168.2.1 for the firewall, etc. I'm sure I'm missing something here.
3) What SOHO firewall product would you recommend for this scenario? I like the free anomaly detection from the ZyXEL USG20, but I would never sign up for services with renewal fees of hundreds of dollars. Perhaps I could combine ZyXEL's USG20 and add OpenDNS Home VIP for web filtering ($20/year).
TIA,
John
This concern brought me to SNB, which has been a fantastic resource. My questions are:
1) What VLANs should I create to segment traffic appropriately? I created a diagram with three VLANs. (See attached.)
Network - General access for laptops and tablets.
Video - Just for Roku. Don't know if a separate VLAN is needed, but this might help performance?
Data - The NAS with more important data. I would restrict access to this VLAN to certain MAC addresses.
2) What are some example IP addresses I could use? I'm assuming 192.168.1.1 for the cable modem gateway, 192.168.2.1 for the firewall, etc. I'm sure I'm missing something here.
3) What SOHO firewall product would you recommend for this scenario? I like the free anomaly detection from the ZyXEL USG20, but I would never sign up for services with renewal fees of hundreds of dollars. Perhaps I could combine ZyXEL's USG20 and add OpenDNS Home VIP for web filtering ($20/year).
TIA,
John