Looks like it should be straight forward. All you need now is a second network adapter in your Blue Iris PC.
And then what kind configuration either with the adapter , my router, or within Windows?
I guess am going to start looking for an adapter then
. Do you have any suggestions?
Looks like it should be straight forward. All you need now is a second network adapter in your Blue Iris PC.
I did a lot more searching and think I found what I was looking for. First I found this thread...
https://ipcamtalk.com/threads/how-do-you-setup-dual-lan.31085/
Then I found the info I needed in the Cliff Notes at the site there.
I need to determine what network card/adapter I should get now. Those Cliff Notes suggest this one...
https://www.amazon.com/dp/B001CY0P7G/?tag=snbforums-20
...Blue Iris Server with Dual LAN
Concept & Configuration
Similar to the way Dahua NVR’s use a separate subnet for the cameras, you can set up a Blue Iris computer the same way by using two network interfaces. If the motherboard on the computer does not have dual LAN interfaces, and there is a spare PCI-E slot, just get an additional Network Interface Card (NIC),
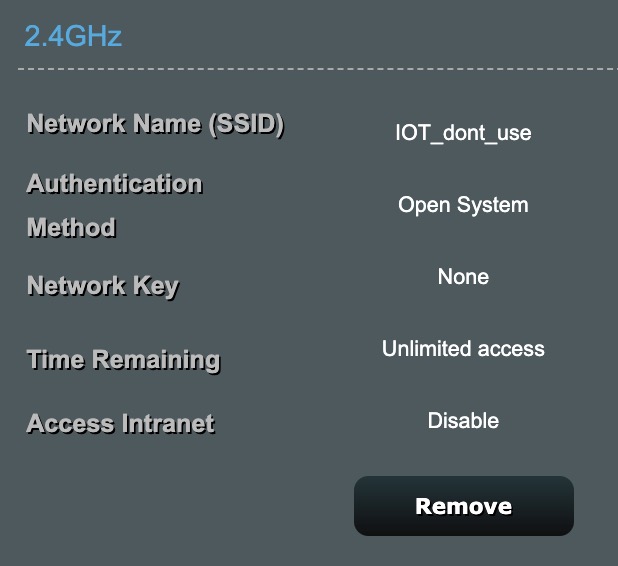
like this one. Use one of the network interfaces for your secure LAN, and the other one for the non-secure camera LAN. The Blue Iris PC needs to have access to Ethernet cables for both of the secure and non-secure networks, on different subnets; i.e. 192.168.1.X secure, and 192.168.0.X non-secure. Just make sure the two subnets share the same subnet mask, like 255.255.255.0.
The non-secure network would connect to the PoE switch w/all your cameras. The cameras should be configured with static IP addresses, and no gateway, so they cannot access the internet. Alternatively, establish firewall rules that prevent the cameras from directly accessing the internet and the secure LAN subnet. With this configuration, only the Blue Iris server will be able to access both the (secure) LAN and the (non-secure) camera network. Note the trick is to leave the gateway address blank for the non-secure LAN NIC settings in the Blue Iris server; only the secure LAN NIC will have a gateway address.
The Blue Iris computer acts as the time server for the cameras, and the cameras point to the server’s non-secure LAN IP address (i.e. 192.168.0.X secure). To allow the communication from the cameras to the time server IP address, set a rule on any firewall used on the Blue Iris server to allow port 123/UDP to pass through the firewall of the non-secure network. IPCamTalk user @DognamedTank recommends using the NTP server built into Windows 10;
see setup guide here.
Viewing Cameras Remotely
While a physically segmented network as described above is an excellent security practice, accessing the camera web interface is more challenging. You can use Google Remote Desktop to view the Blue Iris computer without having to forward port(s) in the router. The Blue Iris computer can be used to view individual cameras, as well as clips and videos saved. You can also use Google Remote Desktop to log into the cameras separately via the web interface, for configuration purposes. All this is possible because Google Remote Desktop is a connection to the desktop of the computer that has access to both the (secure) LAN and the (non-secure) camera network. Google Remote Desktop, TeamViewer, and similar software do NAT traversal by keeping a connection active to a remote server that can be used to connect to your computer, just like he P2P function on many cameras. Unfortunately, using a remote desktop application will significantly increase CPU utilization, so don’t leave it connected full-time.
Viewing Cameras at Home
If you want to log into the web interface of your camera without using Google Remote Desktop, use the Blue Iris computer that has access to both the (secure) LAN and the (non-secure) camera network. Alternatively, use the “Remote Desktop” apps native to both Windows and OSX. From a security perspective, it would not be a good idea to use a computer temporarily connected to the (non-secure) camera network, as it defeats the purpose of having separate networks.
Above info found in Cliff Notes here...
https://ipcamtalk.com/wiki/ip-cam-talk-cliff-notes/