systematic
Regular Contributor
Hi All,
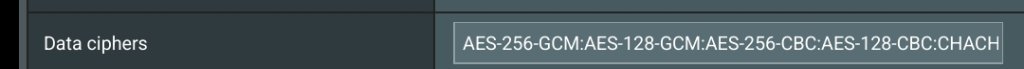
I have an ASUS Router AC86U flashed with Firmware version 386.11 and I have enabled the OpenVPN Server in the router settings as follows:

I have downloaded the latest version of the OpenVPN Connect and loaded the tried connect to the router from a remote location and get the following error message:

Here are the logs in OpenVPN Connect:

Now I read in a previous thread to add a line to the OVPN config file as follows:

This still gave the same error message. Any idea what I can do please to get it working?
ive used OpenVPN connect AND Tunnel Blink and both do not connect.
I have an ASUS Router AC86U flashed with Firmware version 386.11 and I have enabled the OpenVPN Server in the router settings as follows:
I have downloaded the latest version of the OpenVPN Connect and loaded the tried connect to the router from a remote location and get the following error message:
Here are the logs in OpenVPN Connect:
Now I read in a previous thread to add a line to the OVPN config file as follows:
This still gave the same error message. Any idea what I can do please to get it working?
ive used OpenVPN connect AND Tunnel Blink and both do not connect.