Volkis
Occasional Visitor
After the latest upgrade of OpenVPN Connect (iOS) to version 3.4.0, connection fails.
When trying to connect you receive an error message; "You are using insecure hash algorithm in CA signature. Please regenerate CA with other hash algorithm".
There is a workaround by changing the advanced settings in the client software and enabling insecure authorisations.
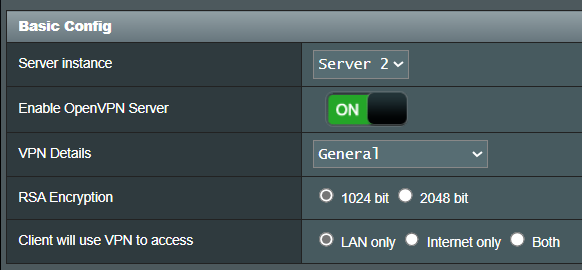
Is there anyone that knows how to reconfigure the server settings in the ASUS router or is there an update in the queue?
When trying to connect you receive an error message; "You are using insecure hash algorithm in CA signature. Please regenerate CA with other hash algorithm".
There is a workaround by changing the advanced settings in the client software and enabling insecure authorisations.
Is there anyone that knows how to reconfigure the server settings in the ASUS router or is there an update in the queue?