Packets is lost when trying to ARP spoof my Asus RT-AC86U (asuswrt-merlin Firmware Version:384.14_2). I can see the ARP table is updated. I doing this on my own home network so have full access to router and the target mac.
I call: arpspoof -i wlan0 -t 192.168.1.1 -r 192.168.1.101
I found -r in the manual (Since most tutorial suggestion to run this separate):
flag -r Poison both hosts (host and target) to capture traffic in both directions. (only valid in conjuntion with -t)
I can see the ARP tables is updated in both mac and router with the attackers MAC address.
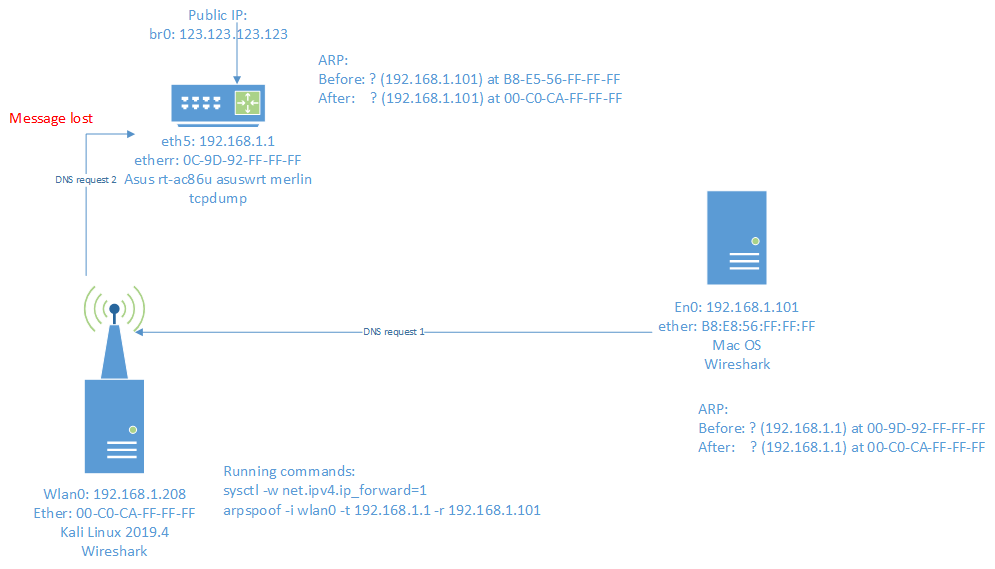
Here is a map of the network(I have removed the 6 last digits):
I run the command: dig @ns-604.awsdns-11.net forums.hak5.org
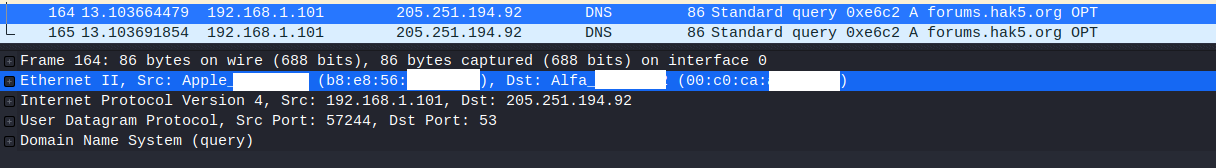
Here is DNS request 1 in wireshark running on kali (src: mac, dst: kali ) Note that this first line is highlighted.
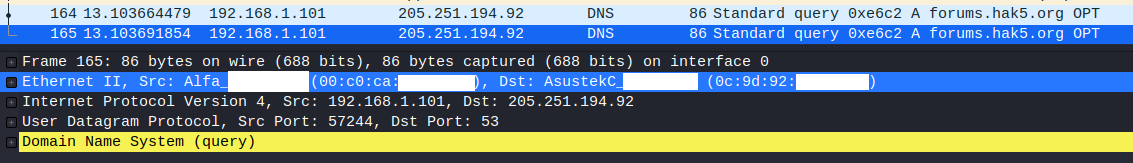
Here is DNS request 2 in wireshark running on kali (src: kali, dst: router ). Note that this second line is highlighted.
The last message that is sent to 0C:9D:92 is never seen when I do tcpdump on the router.
I have to little knowledge about tcpdump but guess it monitors packets that goes across the interface. So if the DNS request was discarded directly could explain why I didn't see it when running tcpdump -i eth5 port 53 on router. However can't explain why it should been discarded since it works when I do the request when I run dig directly on kali-pc.
Any suggestion what could cause this? I will see if I can find any logs where I can see discarded messages or if I can find any other logs to see where the message disappear.
Just as info eth5 (wifi 2.4) and eth6 (5Ghz) and eth1-4 is the ports on the router. I didn't know about this before I thought it was only one interface br0, but br0 is the interface for the public wifi.
I think it might be something with the iptables. However I don't understand them so include them here incase someone else can see something wrong with them:
admin@RT-AC86U-D368:/tmp/home/root# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
INPUT_PING icmp -- anywhere anywhere icmp echo-request
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
DROP all -- anywhere anywhere state INVALID
PTCSRVWAN all -- anywhere anywhere
PTCSRVLAN all -- anywhere anywhere
ACCEPT all -- anywhere anywhere state NEW
ACCEPT all -- anywhere anywhere state NEW
OVPN all -- anywhere anywhere state NEW
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
INPUT_ICMP icmp -- anywhere anywhere
DROP all -- anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
other2wan all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere state INVALID
NSFW all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate DNAT
OVPN all -- anywhere anywhere state NEW
DROP all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain ACCESS_RESTRICTION (0 references)
target prot opt source destination
Chain DNSFILTER_DOT (0 references)
target prot opt source destination
Chain FUPNP (0 references)
target prot opt source destination
Chain INPUT_ICMP (1 references)
target prot opt source destination
RETURN icmp -- anywhere anywhere icmp echo-request
RETURN icmp -- anywhere anywhere icmp timestamp-request
ACCEPT icmp -- anywhere anywhere
Chain INPUT_PING (1 references)
target prot opt source destination
DROP icmp -- anywhere anywhere
Chain NSFW (1 references)
target prot opt source destination
Chain OVPN (2 references)
target prot opt source destination
DROP all -- anywhere anywhere
Chain PControls (0 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
Chain PTCSRVLAN (1 references)
target prot opt source destination
Chain PTCSRVWAN (1 references)
target prot opt source destination
Chain SECURITY (0 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST
RETURN icmp -- anywhere anywhere icmp echo-request limit: avg 1/sec burst 5
DROP icmp -- anywhere anywhere icmp echo-request
RETURN all -- anywhere anywhere
Chain default_block (0 references)
target prot opt source destination
Chain logaccept (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "ACCEPT "
ACCEPT all -- anywhere anywhere
Chain logdrop (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "DROP "
DROP all -- anywhere anywhere
Chain other2wan (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
DROP all -- anywhere anywhere
I call: arpspoof -i wlan0 -t 192.168.1.1 -r 192.168.1.101
I found -r in the manual (Since most tutorial suggestion to run this separate):
flag -r Poison both hosts (host and target) to capture traffic in both directions. (only valid in conjuntion with -t)
I can see the ARP tables is updated in both mac and router with the attackers MAC address.
Here is a map of the network(I have removed the 6 last digits):
I run the command: dig @ns-604.awsdns-11.net forums.hak5.org

Here is DNS request 1 in wireshark running on kali (src: mac, dst: kali ) Note that this first line is highlighted.

Here is DNS request 2 in wireshark running on kali (src: kali, dst: router ). Note that this second line is highlighted.

The last message that is sent to 0C:9D:92 is never seen when I do tcpdump on the router.
I have to little knowledge about tcpdump but guess it monitors packets that goes across the interface. So if the DNS request was discarded directly could explain why I didn't see it when running tcpdump -i eth5 port 53 on router. However can't explain why it should been discarded since it works when I do the request when I run dig directly on kali-pc.
Any suggestion what could cause this? I will see if I can find any logs where I can see discarded messages or if I can find any other logs to see where the message disappear.
Just as info eth5 (wifi 2.4) and eth6 (5Ghz) and eth1-4 is the ports on the router. I didn't know about this before I thought it was only one interface br0, but br0 is the interface for the public wifi.
I think it might be something with the iptables. However I don't understand them so include them here incase someone else can see something wrong with them:
admin@RT-AC86U-D368:/tmp/home/root# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
INPUT_PING icmp -- anywhere anywhere icmp echo-request
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
DROP all -- anywhere anywhere state INVALID
PTCSRVWAN all -- anywhere anywhere
PTCSRVLAN all -- anywhere anywhere
ACCEPT all -- anywhere anywhere state NEW
ACCEPT all -- anywhere anywhere state NEW
OVPN all -- anywhere anywhere state NEW
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
INPUT_ICMP icmp -- anywhere anywhere
DROP all -- anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
other2wan all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere state INVALID
NSFW all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate DNAT
OVPN all -- anywhere anywhere state NEW
DROP all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain ACCESS_RESTRICTION (0 references)
target prot opt source destination
Chain DNSFILTER_DOT (0 references)
target prot opt source destination
Chain FUPNP (0 references)
target prot opt source destination
Chain INPUT_ICMP (1 references)
target prot opt source destination
RETURN icmp -- anywhere anywhere icmp echo-request
RETURN icmp -- anywhere anywhere icmp timestamp-request
ACCEPT icmp -- anywhere anywhere
Chain INPUT_PING (1 references)
target prot opt source destination
DROP icmp -- anywhere anywhere
Chain NSFW (1 references)
target prot opt source destination
Chain OVPN (2 references)
target prot opt source destination
DROP all -- anywhere anywhere
Chain PControls (0 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
Chain PTCSRVLAN (1 references)
target prot opt source destination
Chain PTCSRVWAN (1 references)
target prot opt source destination
Chain SECURITY (0 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST limit: avg 1/sec burst 5
DROP tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST
RETURN icmp -- anywhere anywhere icmp echo-request limit: avg 1/sec burst 5
DROP icmp -- anywhere anywhere icmp echo-request
RETURN all -- anywhere anywhere
Chain default_block (0 references)
target prot opt source destination
Chain logaccept (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "ACCEPT "
ACCEPT all -- anywhere anywhere
Chain logdrop (0 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "DROP "
DROP all -- anywhere anywhere
Chain other2wan (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
DROP all -- anywhere anywhere
Last edited:

