@thelonelycoder ... would it be trivial to add a breakdown of stats by client? (Mainly to figure out TLS errors) Or is that more challenging to log than it seems on the surface?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Diversion Diversion - the Router Ad-Blocker
- Thread starter thelonelycoder
- Start date
PeterR
Senior Member
Yes, I did all that. Should I re-create the CA cert?
That's not required. You state that you imported the certificate into the Firefox certificate store, but did you also import the certificate into the Windows certificate store (I assume you're using Windows)?
That's not required. You state that you imported the certificate into the Firefox certificate store, but did you also import the certificate into the Windows certificate store (I assume you're using Windows)?
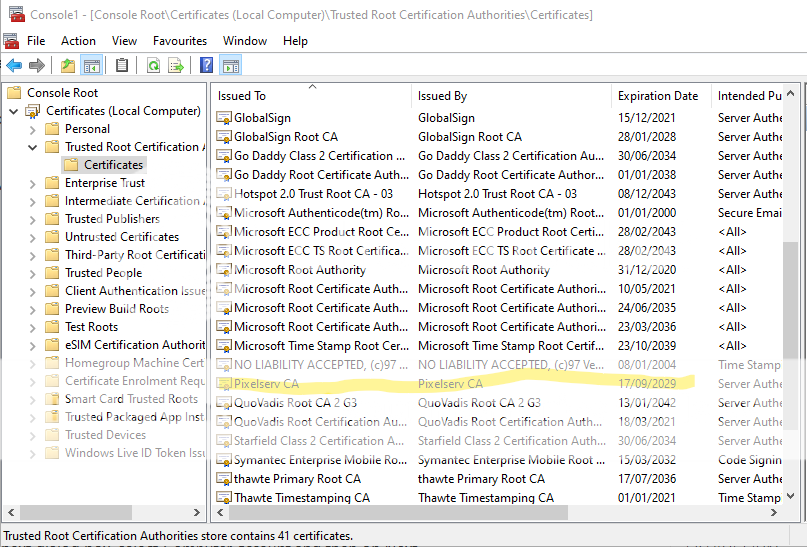
Hmm. It doesn't appear so based on my certificates. I also did a search from the top level for anything that contains "pixel" and it returned nothing.

I followed the steps as outlined below:
Windows: Chrome/Edge/IE
The follow procedure will import your CA cert and trust it system wide.
- Open your browser. Visit http://pixelserv ip/ca.crt. Make sure you replace pixelserv ip with the actual IP address of pixelserv.
- Find the downloaded file, ca.crt.
- Double click on `ca.crt' to view the certificate.
- Click "Install Certificate.." and select "Local Machine".
- Click "Place all certificate in the following store" on next screen.
- Click "Browse..." and select "Trusted Root Certification Authorities".
- Click "Next" and then "Finish" on next screen.
-------------------------------------------
I also just tried to manually import using MMC using this Windows guide. I must have taken a wrong step somewhere.
dave14305
Part of the Furniture
Did dnsmasq restart successfully?i just buy RT-AC68U and install asus merlin ng, amtm, skynet and diversion
i enable diversion, use pixelserv-tls and standard+ blocking
then once i turn on ad-blocking, my internet is gone
am i missing something here?
Check output of command:
Code:
tail /opt/var/log/dnsmasq.logZastoff
Very Senior Member
I just did an M&M reset on RMerlin's 384.13 firmware and added Jack Yaz's uiDivStats so I can see blocked domains in the routers GUI.
I've been using Diversion and uiDivStats for a long time and never seen the entry that keeps popping up and growing. It's DHCPREQUEST(br0).
I don't believe it's supposed to be there as I have never seen it before. Anyone have any ideas what it is and how to stop it from being in my top 10 requested domains list?
attached a photo:
Test with changing (a guess)LAN/DHCP-Server/Hide DHCP/RA queries=yes
thelonelycoder
Part of the Furniture
I just did an M&M reset on RMerlin's 384.13 firmware and added Jack Yaz's uiDivStats so I can see blocked domains in the routers GUI.
I've been using Diversion and uiDivStats for a long time and never seen the entry that keeps popping up and growing. It's DHCPREQUEST(br0).
I don't believe it's supposed to be there as I have never seen it before. Anyone have any ideas what it is and how to stop it from being in my top 10 requested domains list?
That's the reason, set Hide DHCP/RA queries to Yes.Test with changing (a guess)LAN/DHCP-Server/Hide DHCP/RA queries=yes
thelonelycoder
Part of the Furniture
It would complicate the stats function considerably if it would need to gather these additional data points.@thelonelycoder ... would it be trivial to add a breakdown of stats by client? (Mainly to figure out TLS errors) Or is that more challenging to log than it seems on the surface?
SomeWhereOverTheRainBow
Part of the Furniture
I see someone else found away to make dnsmasq logs to grow infinitely large in a short period of time.That's the reason, set Hide DHCP/RA queries to Yes.
dave14305
Part of the Furniture
This struck me as odd, since I log my DHCP queries and haven't seen this problem in regular Diversion stats reports. So I went poking and it seems this particular stats compilation can be broken by DHCP requests in the log as well as dnsmasq log-extra being enabled since the client LAN IP appears in every line. Would it work for @thelonelycoder and @Jack Yaz to grep for only query lines?That's the reason, set Hide DHCP/RA queries to Yes.
Code:
/opt/bin/grep -a " query.* from $i$" $dnsmasqLog | awk '{print $(NF-2)}' |After a reboot I get these lines over and over again:
avahi-daemon[2700]: Withdrawing address record for 192.168.1.253 on br0.
avahi-daemon[2700]: Withdrawing address record for 127.0.1.1 on lo.
avahi-daemon[2700]: Withdrawing address record for 127.0.0.1 on lo.
avahi-daemon[2700]: Host name conflict, retrying with RT-AX88U-2197
avahi-daemon[2700]: Registering new address record for 192.168.1.253 on br0.IPv4.
avahi-daemon[2700]: Registering new address record for 192.168.1.1 on br0.IPv4.
avahi-daemon[2700]: Registering new address record for 127.0.1.1 on lo.IPv4.
avahi-daemon[2700]: Registering new address record for 127.0.0.1 on lo.IPv4.
Pixel serve is set to 192.168.1.253, and the DHCP addresses are limited to 192.168.1.2 through 245. What is happening here?
avahi-daemon[2700]: Withdrawing address record for 192.168.1.253 on br0.
avahi-daemon[2700]: Withdrawing address record for 127.0.1.1 on lo.
avahi-daemon[2700]: Withdrawing address record for 127.0.0.1 on lo.
avahi-daemon[2700]: Host name conflict, retrying with RT-AX88U-2197
avahi-daemon[2700]: Registering new address record for 192.168.1.253 on br0.IPv4.
avahi-daemon[2700]: Registering new address record for 192.168.1.1 on br0.IPv4.
avahi-daemon[2700]: Registering new address record for 127.0.1.1 on lo.IPv4.
avahi-daemon[2700]: Registering new address record for 127.0.0.1 on lo.IPv4.
Pixel serve is set to 192.168.1.253, and the DHCP addresses are limited to 192.168.1.2 through 245. What is happening here?
ColinTaylor
Part of the Furniture
I don't think this is anything to do with Diversion.Hmmm, it doesn't happen when I do a power off/on cycle. I only have three things plugged into the router: a switch (with loop back protection), my desk-top computer, and a hardlink to an AImesh unit. Could the AImesh be causing this?
In the other thread the messages appeared to be caused by connecting a Media Bridge. An AiMesh node works in a similar manner so could well be the cause.
Are you saying that after power cycling the router you no longer have the problem?
ColinTaylor
Part of the Furniture
Probably best to open a separate thread about this as there's no particular reason to think it's related to Diversion."Are you saying that after power cycling the router you no longer have the problem?"
That is correct. If I do a power off/on cycle it boots up beautifully. I even see the lines that sets pixel server. On the other hand, reboot is a nightmare.
Hmm. It doesn't appear so based on my certificates. I also did a search from the top level for anything that contains "pixel" and it returned nothing.

I followed the steps as outlined below:
Windows: Chrome/Edge/IE
The follow procedure will import your CA cert and trust it system wide.
Restart browser to take effect.
- Open your browser. Visit http://pixelserv ip/ca.crt. Make sure you replace pixelserv ip with the actual IP address of pixelserv.
- Find the downloaded file, ca.crt.
- Double click on `ca.crt' to view the certificate.
- Click "Install Certificate.." and select "Local Machine".
- Click "Place all certificate in the following store" on next screen.
- Click "Browse..." and select "Trusted Root Certification Authorities".
- Click "Next" and then "Finish" on next screen.
-------------------------------------------
I also just tried to manually import using MMC using this Windows guide. I must have taken a wrong step somewhere.
I'm still struggling with this. I re-created the cert and re-imported. Yet it still doesn't appear on any of my computers within the Certificate Manager. I'm about to reset my router and wipe my JFFS so I can start fresh. Before I do though, I'd love to know if there might be something else less nuclear.
@thelonelycoder Are you intending to replace the ep update to include the pixelserv 2.3.1 instead of Yaz's 2.3.0? Just curious about how I should approach this.
dave14305
Part of the Furniture
When I imported the Pixelserv CA into Windows, I chose Current User (since it was on a work computer I didn't want to mess with the Local Machine). It shows up in Control Panel / Internet Options / Content / Certificates / Trusted Root Certificates.I'm still struggling with this. I re-created the cert and re-imported. Yet it still doesn't appear on any of my computers within the Certificate Manager. I'm about to reset my router and wipe my JFFS so I can start fresh. Before I do though, I'd love to know if there might be something else less nuclear.
When I imported the Pixelserv CA into Windows, I chose Current User (since it was on a work computer I didn't want to mess with the Local Machine). It shows up in Control Panel / Internet Options / Content / Certificates / Trusted Root Certificates.
Ok, so I believe I figured out part of the issue. It appears that the certificate is named "US" instead of Pixelserv. The date 7/27 is also when I originally created the certificate. Why is not showing with the name Pixelserv and should it be re-created? Or else why do I seem to be having the odd issues that others don't seem to?

Similar threads
- Replies
- 4
- Views
- 1K
- Replies
- 695
- Views
- 121K
- Replies
- 29
- Views
- 3K
- Replies
- 326
- Views
- 72K
- Replies
- 499
- Views
- 127K
Similar threads
Similar threads
-
Skynet Unable to refresh Skynet to whitelist domains in Shared-Diversion
- Started by sentinelvdx
- Replies: 2
-
-
Diversion Need help - Diversion - Skynet - LAN - Server Settings
- Started by cc666
- Replies: 3
-
Diversion Which IP is Diversion using in my AIMesh system?
- Started by rkalinka
- Replies: 4
-
-
Diversion Diversion ad blocking works with secure DNS disabled only
- Started by texnote
- Replies: 17
-
Ad blocker question. Diversion or pi-hole? Or both?
- Started by chewy74
- Replies: 21
-
Diversion Diversion - Ads Not Getting Blocked
- Started by SashaSolitaire
- Replies: 4
-
If Skynet Blocks Diversion website look below
- Started by Jack-Sparr0w
- Replies: 4
-
Diversion Diversion Question- Configuring the Cache TTL
- Started by jrichard326
- Replies: 34
Latest threads
-
Kamoj Kamoj Addon 5.5 b47 for Netgear R7800/R8900/R9000 with Voxel FW
- Started by kamoj
- Replies: 0
-
Release ASUS GT-BE19000 Firmware version 3.0.0.6.102_39244 (2026/02/04)
- Started by oxide
- Replies: 0
-
Trying to install DD-WRT on Asus RT-ACRH13
- Started by Miaowminx
- Replies: 1
-
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 3,927 (members: 14, guests: 3,913)
