Thank you. That is not a problem. Might I suggest a note in the README to avoid doing what I did and what @js28194 suggested? It seems natural that people will attempt to bulk delete in this manner which will cause problems.There is currently no method of bulk deletion short of deleting the entire policy and creating a new one.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
DomainVPNRouting Domain VPN Routing v3.2.0 ***Release***
- Thread starter Ranger802004
- Start date
I haven't tested this yet, but after bulk delete in the file, I'm not sure what happens if completely delete the corresponding policy_yourpocliyname_domaintoip file. I think the script recreates it basically "cleaning up" the ip addresses albiet in a round about way.
ComputerSteve
Senior Member
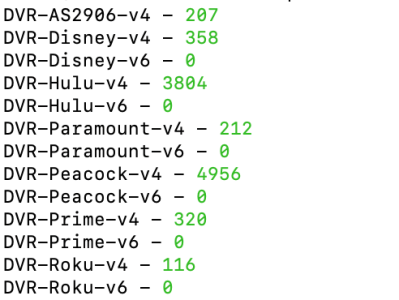
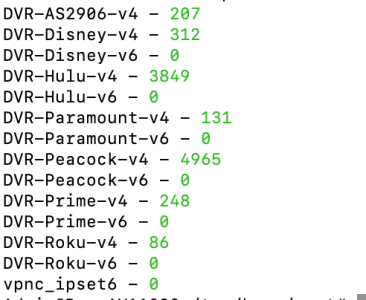
So question @Ranger802004 I'm noticing that my GT-AX11000 Pro running your latest beta script and running 3006 codebase firmware is displaying when I run the terminal command liststats -> vpnc_ipset6 ... I don't know what that is ? If I go to my GT-AX11000 running merlin 3004 codebase and your latest beta of the script I don't see vpnc_ipset6 listed when I run liststats in terminal... Is this normal ? Do I need this ?
Attachments
Ranger802004
Very Senior Member
I’m not sure what is creating this, please open a GitHub issue so we can investigate.So question @Ranger802004 I'm noticing that my GT-AX11000 Pro running your latest beta script and running 3006 codebase firmware is displaying when I run the terminal command liststats -> vpnc_ipset6 ... I don't know what that is ? If I go to my GT-AX11000 running merlin 3004 codebase and your latest beta of the script I don't see vpnc_ipset6 listed when I run liststats in terminal... Is this normal ? Do I need this ?
Ranger802004
Very Senior Member
***v3.1.1-beta4 has been released to the beta channel***
Review your policies to make sure your DNS servers have not been erroneously added to the policies Domain to IP lists. If they are added use the deleteip function to remove.
Release Notes:
v3.1.1-beta4 - 04/23/2025
Enhancements:
- If DNS-over-TLS is enabled and servers are configured on the system DNS-over-TLS DNS server list, dig will configure use for DNS-over-TLS by randomly selecting a DNS-over-TLS DNS server.
- Python3 and dig are required to be installed for this functionality.
- An existing DNS configuration for the interface in Domain VPN Routing will override this functionality.
- Added debug logging for DNS-over-TLS configuration during querypolicy function execution.
Fixes:
- Fixed an issue with IPv4 unreachable rules being created for VPN interfaces due to a missing default route for the VPN routing table.
- Fixed an issue where restoreasncache was executing when restoring an individual policy, this will still execute when restoring all policies.
- Fixed issues with erroneous data being ingested by dig.
- Fixed an issue with dig applying DNS Server configuration incorrectly and causing unreturned data from queries.
- Minor fixes and optimizations
Review your policies to make sure your DNS servers have not been erroneously added to the policies Domain to IP lists. If they are added use the deleteip function to remove.
Release Notes:
v3.1.1-beta4 - 04/23/2025
Enhancements:
- If DNS-over-TLS is enabled and servers are configured on the system DNS-over-TLS DNS server list, dig will configure use for DNS-over-TLS by randomly selecting a DNS-over-TLS DNS server.
- Python3 and dig are required to be installed for this functionality.
- An existing DNS configuration for the interface in Domain VPN Routing will override this functionality.
- Added debug logging for DNS-over-TLS configuration during querypolicy function execution.
Fixes:
- Fixed an issue with IPv4 unreachable rules being created for VPN interfaces due to a missing default route for the VPN routing table.
- Fixed an issue where restoreasncache was executing when restoring an individual policy, this will still execute when restoring all policies.
- Fixed issues with erroneous data being ingested by dig.
- Fixed an issue with dig applying DNS Server configuration incorrectly and causing unreturned data from queries.
- Minor fixes and optimizations
Ranger802004
Very Senior Member
***v3.1.1 has been released to production channel***
Release Notes:
Enhancements:
- If DNS-over-TLS is enabled and servers are configured on the system DNS-over-TLS DNS server list, dig will configure use for DNS-over-TLS by randomly selecting a DNS-over-TLS DNS server.
- Python3 and dig are required to be installed for this functionality.
- An existing DNS configuration for the interface in Domain VPN Routing will override this functionality.
- Added debug logging for DNS-over-TLS configuration during querypolicy function execution.
Fixes:
- Fixed an issue with IPv4 unreachable rules being created for VPN interfaces due to a missing default route for the VPN routing table.
- Fixed an issue where restoreasncache was executing when restoring an individual policy, this will still execute when restoring all policies.
- Fixed issues with erroneous data being ingested by dig.
- Fixed an issue with dig applying DNS Server configuration incorrectly and causing unreturned data from queries.
- Minor fixes and optimizations
Release Notes:
Enhancements:
- If DNS-over-TLS is enabled and servers are configured on the system DNS-over-TLS DNS server list, dig will configure use for DNS-over-TLS by randomly selecting a DNS-over-TLS DNS server.
- Python3 and dig are required to be installed for this functionality.
- An existing DNS configuration for the interface in Domain VPN Routing will override this functionality.
- Added debug logging for DNS-over-TLS configuration during querypolicy function execution.
Fixes:
- Fixed an issue with IPv4 unreachable rules being created for VPN interfaces due to a missing default route for the VPN routing table.
- Fixed an issue where restoreasncache was executing when restoring an individual policy, this will still execute when restoring all policies.
- Fixed issues with erroneous data being ingested by dig.
- Fixed an issue with dig applying DNS Server configuration incorrectly and causing unreturned data from queries.
- Minor fixes and optimizations
After updating to the latest firmware, I'm seeing this error:
Is there anything in particular I can do to fix this?
Code:
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS35995-v4 Interface: FWMark: 0x7000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS63179-v4 Interface: FWMark: 0x7000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS13414-v4 Interface: FWMark: 0x7000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS40027-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS2906-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS23286-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS22604-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS11251-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS398849-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS14618-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS16509-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
Query ASN: AS40027...
domain_vpn_routing: Query ASN - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS40027-v4 Interface: FWMark: 0xc000
domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3
domain_vpn_routing: Query ASN - Processing Time: 7 secondsIs there anything in particular I can do to fix this?
Ranger802004
Very Senior Member
Submit a GitHub issue.After updating to the latest firmware, I'm seeing this error:
Code:domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS35995-v4 Interface: FWMark: 0x7000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS63179-v4 Interface: FWMark: 0x7000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS13414-v4 Interface: FWMark: 0x7000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for ovpnc4 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS40027-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS2906-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS23286-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS22604-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS11251-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS398849-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS14618-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Restore ASN Cache - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS16509-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 Query ASN: AS40027... domain_vpn_routing: Query ASN - ***Error*** Failed to add IPTables POSTROUTING rule for IPSET: DVR-AS40027-v4 Interface: FWMark: 0xc000 domain_vpn_routing: Create IP Mark Rules - ***Error*** FWMark not set for wgc3 domain_vpn_routing: Query ASN - Processing Time: 7 seconds
Is there anything in particular I can do to fix this?
Ranger802004
Very Senior Member
***v3.2.0-beta1 has been published to the beta channel***
Release Notes:
Enhancements:
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Release Notes:
Enhancements:
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Now that large ASNs are fixed, I decided to write a script to find domains I previously added that I already have in the ASN list. This script will create a bash script you can copy to the router and use to delete domains that should be skipped since they are already handled by ASNs. It works very nicely with domain_vpn_routing. I run the script on my Mac using python.

 github.com
github.com
GitHub - dan-gill/DNS-to-ASN: Automates domain-to-ASN resolution and filters domains already routed via VPN policy. Designed for Asus-Merlin’s domain_vpn_routing.sh.
Automates domain-to-ASN resolution and filters domains already routed via VPN policy. Designed for Asus-Merlin’s domain_vpn_routing.sh. - dan-gill/DNS-to-ASN
Ranger802004
Very Senior Member
***v3.2.0-beta2 has been released to the beta channel to address some issues with v3.2.0-beta1 as well as another additional enhancement***
Release Notes:
v3.2.0-beta2 - 05/12/2025
Enhancements:
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Release Notes:
v3.2.0-beta2 - 05/12/2025
Enhancements:
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Ranger802004
Very Senior Member
***v3.2.0-beta3 is now available on the beta channel***
Release Notes:
v3.2.0-beta3 - 05/15/2025
Enhancements:
- Interface selection when creating or editing policies or adding ASNs will now allow easier selection by number list instead of manually typing the interface name.
- Enhanced deteection of WireGuard interface information.
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Release Notes:
v3.2.0-beta3 - 05/15/2025
Enhancements:
- Interface selection when creating or editing policies or adding ASNs will now allow easier selection by number list instead of manually typing the interface name.
- Enhanced deteection of WireGuard interface information.
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
Ranger802004
Very Senior Member
***v3.2.0 is now available to production channel***
Release Notes:
Enhancements:
- Interface selection when creating or editing policies or adding ASNs will now allow easier selection by number list instead of manually typing the interface name.
- Enhanced deteection of WireGuard interface information.
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
- Minor bug fixes
Release Notes:
Enhancements:
- Interface selection when creating or editing policies or adding ASNs will now allow easier selection by number list instead of manually typing the interface name.
- Enhanced deteection of WireGuard interface information.
- Added custom priority settings for interfaces that can be modified using the configuration menu.
- Enhance Query ASN logic to handle larger ASNs and optimize query time. This requires grep to be installed from Entware.
- Querying policies now can use grep from Entware to efficiently process new IP addresses.
- Enhanced interface state detection logic.
- Showing policies now displays the associated interfaces and the connected state status.
- Showing ASNs now displays the associated interfaces and the connected state status.
- Minor optimization and performance enhancements.
Fixes:
- Querying policies will now properly delete temporary files generated under /tmp.
- Fixed UI bugs not allowing return in certain menus.
- Fixed configuration menu bug that was not showing Dual WAN DNS Settings when router was configured for Dual WAN.
- Minor bug fixes
Similar threads
- Replies
- 12
- Views
- 1K
DomainVPNRouting
Domain VPN Routing
- Replies
- 96
- Views
- 11K
DomainVPNRouting
Domain VPN Routing help
- Replies
- 4
- Views
- 877
- Replies
- 22
- Views
- 2K
- Replies
- 243
- Views
- 28K
Similar threads
Similar threads
-
-
-
-
VPNMON Please VOTE for continued Proton VPN/VPNMON-R3 functionality!
- Started by Viktor Jaep
- Replies: 4
-
Does this look right for Nord VPN Unbound setup, the extra address worked
- Started by Jack-Sparr0w
- Replies: 22
-
Unbound Redirect Internet traffic through tunnel best setting for unbound dns and vpn
- Started by Jack-Sparr0w
- Replies: 3
-
Wireguard VPN Director for VPN - WireGuard® Manager© v1.04 by Martineau
- Started by unclebuk
- Replies: 3
-
Push notification script for admin, ssh, VPN events etc..
- Started by giosita
- Replies: 3
-
-
Latest threads
-
-
Asus XT8 Wireless Backhaul - router at 160MHz, nodes at 80MHz
- Started by delaveganz
- Replies: 2
-
AC-86u vulnerability tracking post-EoL (asuswrt-merlin 386.14_2)
- Started by JTnola
- Replies: 1
-
amtm Announcing AMTM-OSR, AMTM Orphaned Script Revival repository
- Started by thelonelycoder
- Replies: 4
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!