Hello everyone.
First of all big thanks goes to
@GNUton for support of DSL-AC68U! I use it with pleasure and effectively.
I'm running 384.17_0-gnuton1 release and behind of CGNAT, I don't care to open any port to public usage. But port forwarding even does not work on LAN.
What I want to do?
I want to forward port 80 from 192.168.1.202 to 192.168.1.1:8080
Which steps I followed;
- Asus Firewall turned off.
- Windows Firewall turned off.
- Static IP assigned to LAN device.
- NAT activated on router and rule defined.
- Router restarted.
But no luck at all

Here is my iptables configuration;
Code:
****@ASUS-ROUTER:/tmp/home/root# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
TCPMSS tcp -- anywhere anywhere tcpflags: SYN,RST/SYN TCPMSS clamp to PMTU
logaccept all -- anywhere anywhere state RELATED,ESTABLISHED
other2wan all -- anywhere anywhere
logdrop all -- anywhere anywhere
logaccept all -- anywhere anywhere
logdrop all -- anywhere anywhere state INVALID
NSFW all -- anywhere anywhere
logaccept all -- anywhere anywhere ctstate DNAT
OVPN all -- anywhere anywhere state NEW
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain ACCESS_RESTRICTION (0 references)
target prot opt source destination
Chain DNSFILTER_DOT (0 references)
target prot opt source destination
Chain FUPNP (0 references)
target prot opt source destination
Chain INPUT_ICMP (0 references)
target prot opt source destination
Chain INPUT_PING (0 references)
target prot opt source destination
Chain NSFW (1 references)
target prot opt source destination
DROP ipv6-auth-- anywhere anywhere
DROP ipv6-crypt-- anywhere anywhere
DROP udp -- anywhere anywhere udp dpt:4500
DROP udp -- anywhere anywhere udp dpt:500
DROP udp -- anywhere anywhere udp dpt:1701
DROP gre -- anywhere anywhere
DROP tcp -- anywhere anywhere tcp dpt:1723
Chain OVPN (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
Chain PControls (0 references)
target prot opt source destination
logaccept all -- anywhere anywhere
Chain PTCSRVLAN (0 references)
target prot opt source destination
Chain PTCSRVWAN (0 references)
target prot opt source destination
Chain SECURITY (0 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN limit: avg 1/sec burst 5
logdrop tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/SYN
RETURN tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST limit: avg 1/sec burst 5
logdrop tcp -- anywhere anywhere tcpflags: FIN,SYN,RST,ACK/RST
RETURN icmp -- anywhere anywhere icmp echo-request limit: avg 1/sec burst 5
logdrop icmp -- anywhere anywhere icmp echo-request
RETURN all -- anywhere anywhere
Chain default_block (0 references)
target prot opt source destination
Chain logaccept (4 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "ACCEPT "
ACCEPT all -- anywhere anywhere
Chain logdrop (6 references)
target prot opt source destination
LOG all -- anywhere anywhere state NEW LOG level warning tcp-sequence tcp-options ip-options prefix "DROP "
DROP all -- anywhere anywhere
Chain other2wan (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
logdrop all -- anywhere anywhere
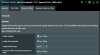
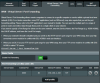
I shared screenshots of my other configurations on attachments. I don't know from where I have mistake. I was using exactly same configuration for years.
Thanks in advance for your help and support.