john9527
Part of the Furniture
A little late....but this guide helped me out...
https://nguvu.org/pfsense/pfsense-baseline-setup/
https://nguvu.org/pfsense/pfsense-baseline-setup/
A little late....but this guide helped me out...
https://nguvu.org/pfsense/pfsense-baseline-setup/
Just try and stay focused and helpful.

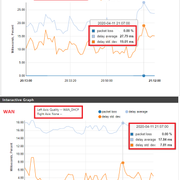
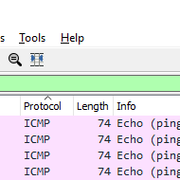
A little late....but this guide helped me out...
https://nguvu.org/pfsense/pfsense-baseline-setup/
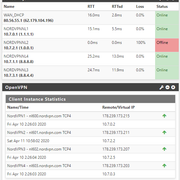

Interesting. I had a an issue where I picked up latency on DNS with my layer 3 switch. You have to setup routed gateways to use a layer 3 switch.
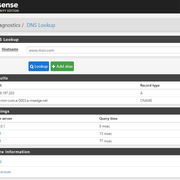
I was running a real Intel server motherboard with Xeons. Utilization was like 1% or 2%.
[USER=68359]
[USER=5292]@coxhaus you also basically verified this latency issue with pfSense.
I know I wasn't imagining it. If a resolution can be found for this issue, that is when I may be tempted to try pfSense once more.
Looking forward to the next few posts and hopefully a quick resolution too (are the defaults not correct, is there something I/we missed?)!
[/USER]
I know I wasn't imagining it. If a resolution can be found for this issue, that is when I may be tempted to try pfSense once more.
Looking forward to the next few posts and hopefully a quick resolution too (are the defaults not correct, is there something I/we missed?)!
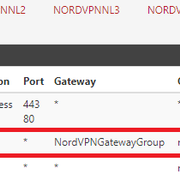
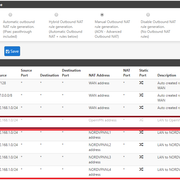
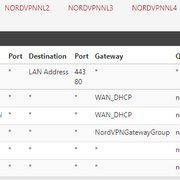
We use essential cookies to make this site work, and optional cookies to enhance your experience.
