D
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
D
Deleted member 22229
Guest
Flashed this beta build and it seems to work fine. As always Netgears change log is very vague stating only (Fixes security issues).
Not sure if Voxel will be able to import these security issues in to his firmware as I don't think Netgear releases source code for beta builds. Hope I am wrong. Happy 4th of July..
Not sure if Voxel will be able to import these security issues in to his firmware as I don't think Netgear releases source code for beta builds. Hope I am wrong. Happy 4th of July..
I see improvement on ping, normally it's 1/2ms behind my AC86U on ping respond to my local DNS and www.facebook.com, tested on my PC with PingPlotter via direct LAN connection. I flashed between 62 and 63beta about 6 times to make it clear, 63beta always got me better result and on par with AC86U, due to my ISP gave me different IP each time I'm not sure the improvement came from the firmware or the IPs, maybe you guys can try it out as we need more samples to see if it's actually improved.
D
Deleted member 22229
Guest
Yep I have been using 63 since release and have had no issues. Lets hope the final release stays the same. 
e38BimmerFN
Very Senior Member
Ran fine on my R7800 in bridge mode. Fixed an odd issue with Voxels 65SF loaded FW and having one xbox wired to the back of it and a 2nd xbox console wired to the main host router with 160Mhz enabled. Both consoles would loose private xbox live chat while being on same time. If I disabled 160Mhz on the main host router, chat worked. I loaded the hot fix and both consoles started working on private chat with 160Mhz enabled.
I'm now loading up Voxels v67.1SF version to see if anything comes back or changes.
I'm now loading up Voxels v67.1SF version to see if anything comes back or changes.
Voxel
Part of the Furniture
Could this hotfix be about the TCP SACK in older kernels? "fixes security issues" is not very informative but they may not be willing to disclose to "minimize" possible exploitation
Try to check in telnet console:
Code:
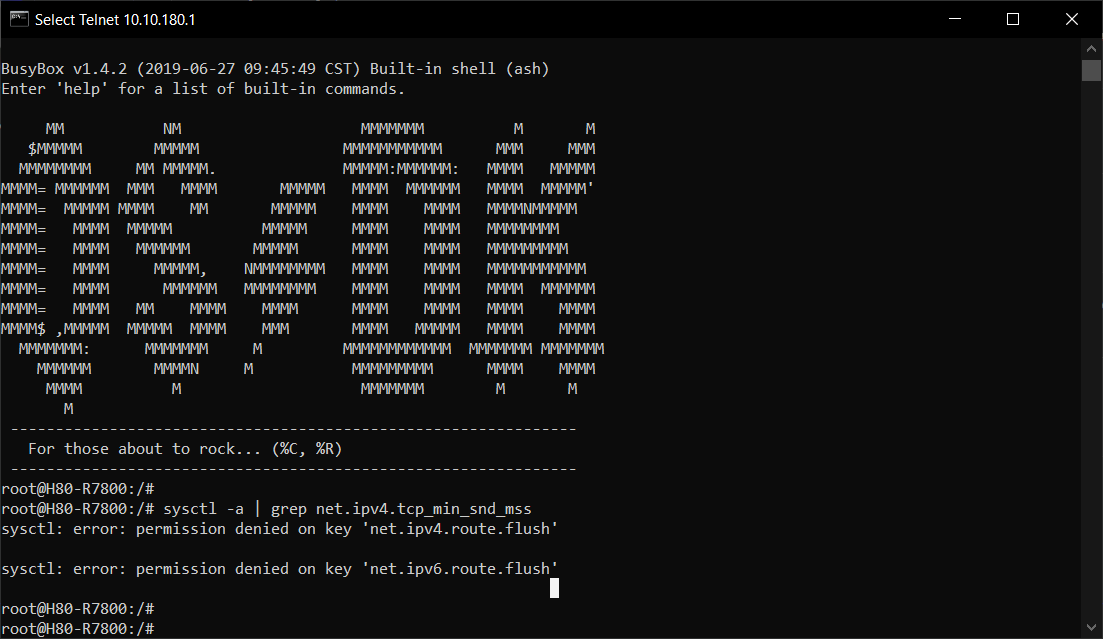
sysctl -a | grep net.ipv4.tcp_min_snd_mssif this command displays nothing then kernel vulnerability is rather not fixed (or at least fixed partially) . If you see:
Code:
net.ipv4.tcp_min_snd_mss = 48it means that CVEs are fixed.
Voxel.
Try to check in telnet console:
Code:sysctl -a | grep net.ipv4.tcp_min_snd_mss
if this command displays nothing then kernel vulnerability is rather not fixed (or at least fixed partially) . If you see:
Code:net.ipv4.tcp_min_snd_mss = 48
it means that CVEs are fixed.
Voxel.
Voxel
Part of the Furniture
So it means that at least CVE-2019-11479 patch was not used for this version.
Voxel.
Voxel
Part of the Furniture
Just FYI results of command:
R7800 1.0.2.68SF:
R9000 1.0.4.32HF:
Debian 9 (Stretch) x64 , PC, with all CVE fixed:
Voxel.
R7800 1.0.2.68SF:
Code:
sysctl: error: permission denied on key 'net.ipv4.route.flush'
net.ipv4.tcp_min_snd_mss = 48
sysctl: error: permission denied on key 'net.ipv6.route.flush'R9000 1.0.4.32HF:
Code:
sysctl: error: permission denied on key 'net.ipv4.route.flush'
net.ipv4.tcp_min_snd_mss = 48
sysctl: error: permission denied on key 'net.ipv6.route.flush'
sysctl: error: permission denied on key 'vm.compact_memory'Debian 9 (Stretch) x64 , PC, with all CVE fixed:
Code:
net.ipv4.tcp_min_snd_mss = 48
sysctl: reading key "net.ipv6.conf.all.stable_secret"
sysctl: reading key "net.ipv6.conf.default.stable_secret"
sysctl: reading key "net.ipv6.conf.eth0.stable_secret"
sysctl: reading key "net.ipv6.conf.lo.stable_secret"Voxel.
He hasn't applied the CVEs. Even on the latest .68SF, they're not patched, according to his post above.Voxel, if you are using the same base firmware as Netgear, and only adding to it, how are you able to apply CVE's to it?
Only when NG releases a new stable firmware with the CVEs patched, then Voxel will rebase and have the same patches.
Doesn't he state in https://www.snbforums.com/threads/custom-firmware-build-for-r7800-v-1-0-2-68sf.57646/ that CVE-2019-11479 is fixed in his latest version?
Yet above he says "So it means that at least CVE-2019-11479 patch was not used for this version". (latest Netgear beta)
Do I have it wrong?
Yet above he says "So it means that at least CVE-2019-11479 patch was not used for this version". (latest Netgear beta)
Do I have it wrong?
Voxel
Part of the Furniture
He hasn't applied the CVEs. Even on the latest .68SF, they're not patched, according to his post above.
Only when NG releases a new stable firmware with the CVEs patched, then Voxel will rebase and have the same patches.
Your assertion is absolutely wrong and abusive as well. First check this:
https://github.com/SVoxel/R7800/commit/d79ca654ef4a5f4297bd0b3e3434335592bd0d80
And this:
https://github.com/SVoxel/R7800/commit/4bbfd1f69fd6f8e70bd4f424a054da2f565849c1
Above are the patches for kernel to fix CVE-2019-11477, CVE-2019-11478 and CVE-2019-11479.
Second, both of you seems do not have a clear picture in your mind and do not realize the fact that I do not integrate my changes into release of the stock firmware. Vice versa: I do integrate their changes on the level of QCA drivers into my version because of my version is on 80 per cents different vs stock version from NG/DNI internally and it would be too hard work to apply my changes. The only advantage of the stock firmware is enclosed QCA drivers so only because of this I have to keep this old modified kernel v. 3.4.103 allowing to use QCA drivers prebulit in the stock firmware to have hardware acceleration in my version of firmware. And to keep obsolete WebGUI what controls these drivers.
These CVE patches above in my sources are created personally by me with a care because they (a) do not exist in ready-to-apply form for the kernel v. 3.4.103 (b) could be used by NG/DNI for their stock firmware. As I hope. And because of this I stressed them in my commit in Githib.
So answering your question:
Voxel, if you are using the same base firmware as Netgear, and only adding to it, how are you able to apply CVE's to it?
I have source codes of modified Linux kernel published by NG/DNI: they have to publish them according to GPL License. And I was able to apply created by me patches and to release my firmware with these patches if I publish my changes according to GPL license. And fixing these CVE is most important at the present time vs other fixes say in WebGUI security.
Voxel.
My apologies Voxel, didn't mean to cause any offence.Your assertion is absolutely wrong and abusive as well.
Thanks for the clarification.
Voxel
Part of the Furniture
I do not quite understand what for did you change these values like mac and serial. And I do not quite understand what you need. BTW it is related to R9000 as far as I understand and it has no relation to the theme (stock firmware for R7800).Can you please help me! I forgot to backup my Art partition and I recreated the values like the serial and lan/Mac addresses but I forgot the pattern scheme
sn: 123456789
ssid: Netgear
passphrase:snbforum
lan mac: 00:11:22:33:44:55:6a
wan mac: 00:11:22:33:44:55:6a
--------------------------
I was able to apply these values from the back of the router however I forgot how the pattern should go for the values here and when using the binary help menu the examples they use for the default values don't help to figure the pattern out for these values
--------------------------
wlan5g mac: ???????
bluetooth Mac: ???????
sfp+ Mac: ???????
11ad Mac: ???????
mtd blocks in R9000 (my version of fw):
Code:
cat /proc/mtd
dev: size erasesize name
mtd0: 001e0000 00020000 "u-boot"
mtd1: 00120000 00020000 "u-boot-env"
mtd2: 00140000 00020000 "ART"
mtd3: 00140000 00020000 "ART.bak"
mtd4: 00440000 00020000 "kernel"
mtd5: 02800000 00020000 "rootfs"
mtd6: 02c40000 00020000 "firmware"
mtd7: 04480000 00020000 "netgear"
mtd8: 12c00000 00020000 "plex"
mtd9: 05780000 00020000 "reserve"
mtd10: 00080000 00020000 "crashdump"
mtd11: 00380000 00020000 "language"
mtd12: 00120000 00020000 "config"
mtd13: 00120000 00020000 "pot"
mtd14: 0001f000 0001f000 "cert"
mtd15: 0005d000 0001f000 "pot.bak"
mtd16: 001b2000 0001f000 "traffic_meter"
mtd17: 001b2000 0001f000 "traffic_meter.bak"
mtd18: 001b2000 0001f000 "dongle"
mtd19: 037b4000 0001f000 "overlay_volume"
mtd20: 11874000 0001f000 "plexmediaserver"Voxel.
Similar threads
- Replies
- 12
- Views
- 831
- Replies
- 0
- Views
- 3K
- Replies
- 26
- Views
- 3K
- Replies
- 15
- Views
- 2K
Similar threads
Similar threads
-
Netgear x6 r7800 power light white brightness
- Started by shs9
- Replies: 3
-
Voxel Custom firmware build for R7800 v. 1.0.2.107SF
- Started by Voxel
- Replies: 12
-
Voxel Custom firmware build for R7800 v. 1.0.2.106SF
- Started by Voxel
- Replies: 26
-
-
Voxel Custom firmware build for R7800 v. 1.0.2.105SF
- Started by Voxel
- Replies: 15
-
Voxel Custom firmware build for R7800 v. 1.0.2.104SF
- Started by Voxel
- Replies: 25
-
-
Voxel [R7800] Way to route traffic using the subdomain used?
- Started by QuinTeknoLife
- Replies: 1
-
Voxel Custom firmware build for R7800 v. 1.0.2.103SF
- Started by Voxel
- Replies: 10
Latest threads
-
Hyperotpic router replacement - will it solve my problem with connection dropping!
- Started by ACME NoLiFe
- Replies: 2
-
-
-
LAN > DHCP List - Manually Assigned Name + Icon DONT SAVE
- Started by copperhead
- Replies: 4
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 904 (members: 15, guests: 889)

