PORTS EXPLAINED
(Difference between Local/Remote Ports + Everything Else)
Every connection has two set ports.
The REMOTE port on the (WAN) server.
The LOCAL port on your (LAN) device.
In TC/Iptables these are distinguished by source/destination tags.
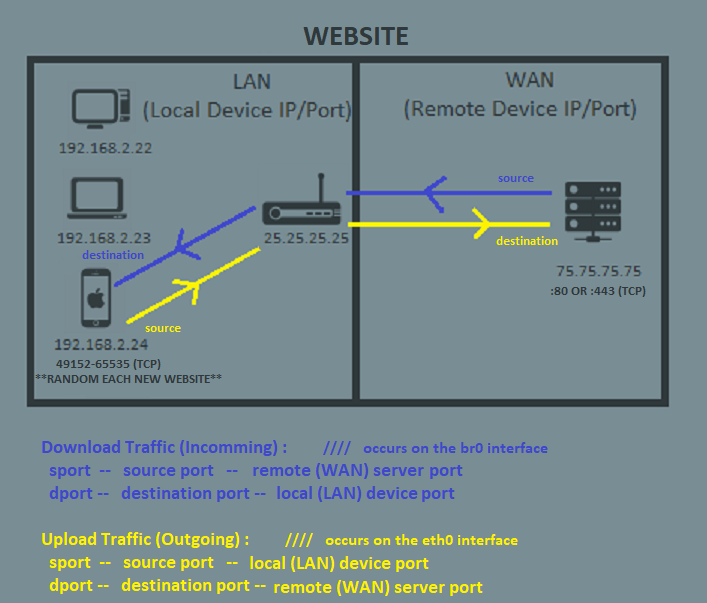
For Download traffic
sport = source port = port on the remote (WAN) server
dport = destination port = port of your local (LAN) device
(br0 interface is defined to catch only download traffic).
For Upload traffic
sport = source port = port of your local (LAN) device
dport = destination port = port on the remote (WAN) server
(eth0 interface is defined to catch only upload traffic).
The remote and local ports are generally
NOT the same.
---
Let's look at three examples.
A) VoIP
1) The (remote) VoIP server is typically hosted on port 4500
2) Your (local) device typically receives traffic on port 4500
**Android Wifi-Calling does NOT follow this pattern**
B) Website
1) The (remote) website server is typically hosted on port 80 or 443.
2) Your (local) device will receive traffic on a random port in the range between 49152 - 65535.
This is called the ephemeral/dynamic port range.
Websites and applications using ephemeral port range will be assigned a random port on on every visit.
I also hope this made it easy to see as to why you should NOT create QOS rules (or even port forwards) EVER for ports 80 / 443 OR the ephemeral 49152-65535 range.
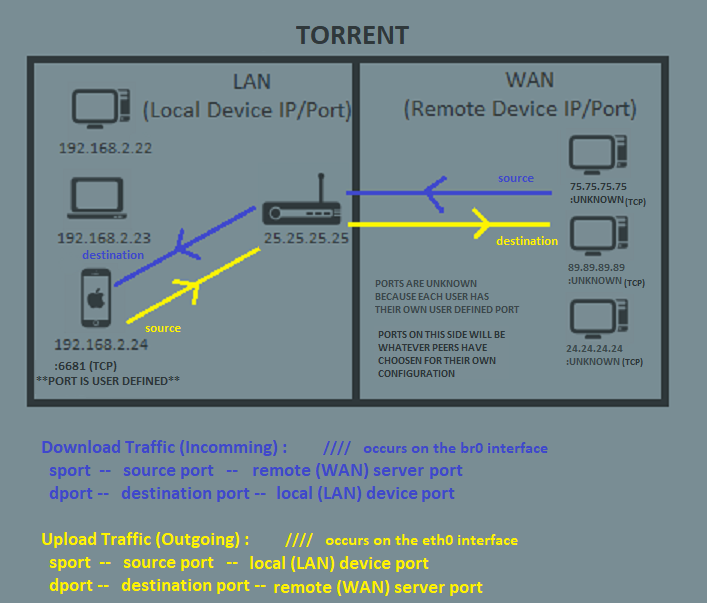
C) Torrent
1) The (remote) peer will receive/send data from a port they have defined. This is not known beforehand.
2) Your (local) device will receive/send data from a port you have defined.
With this in mind, your custom port rules can filter by either.
1) the remote port from the (WAN) server.
or
2) the local port on your (LAN) device.
If you mix up the designations, don't be surprised if the rule is not catching any traffic.
---
One last bit of important information, TCP vs UDP.
What is the difference?
TCP - used for to transfer information WITHOUT DATA LOSS (most used protocol)
eg. receiving device sends ACKnowledgement of received/uncorrupted data
UDP - used for REAL TIME TRANSFER of ping sensitive information (data corruption possible)
eg. when transferring VoIP/Gaming packets there is no time to wait for an ACKnowledgement
UDP skips the ACKnowledgement protocol and will keep sending new data as it occurs without re-transmitting missing or corrupted data
Why is this important?
TC rules filter on both UDP & TCP protocols without distinction.
Iptables need to have either the UDP or TCP protocol explicitly defined (a wrong choice will make rule not work).
Knowledge of UDP / TCP difference can help narrow down between integrity sensitive or ping sensitive data
---
Awesome, now that I am a port master,
how do I find out what ports are being used?
Method 1) On the local device itself
You can check all port usage via the following:
Go to Task Manager -> Performance -> Resource Monitor -> Network.
Look for your executable in both
-TCP Connections (Active TCP connections show up here)
&&
-Listening Ports (Active UDP connections show up here + opened TCP connections)
--Information under TCP connections.
Local & Remote TCP ports defined here per application.
--Information under Listening Ports
Listening Ports & that ports Protocol are defined here.
Note: Listening Port means LOCAL port
Method 2) On the router
Network Tools --> Netstat --> Netstat-nat --> By Source IP
Local IP/Ports are on the left
Remote IP/Ports are on the right
Method 3) Look it up online
--
No more port question will ever be answered.
It takes me 30 minutes to type out the same thing on EVERY question.
This is your one shot go to with pictures.
This information is also readily available online via search or even earlier in this thread.
The remote/local port designations are also explained in the comments of the template rules.