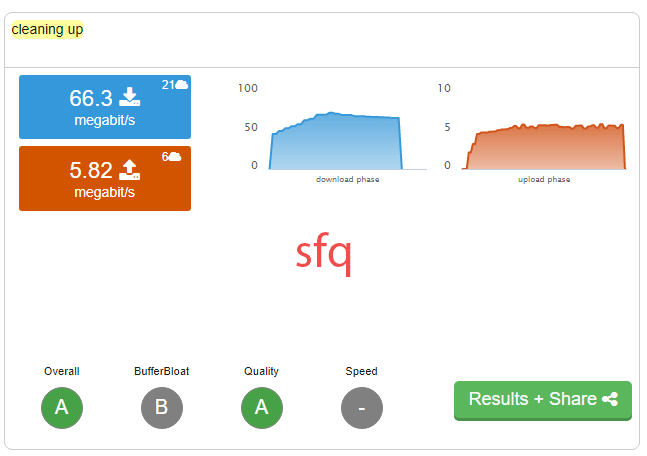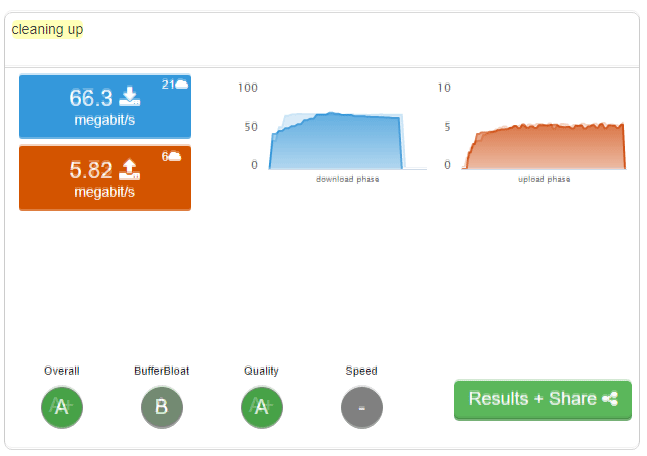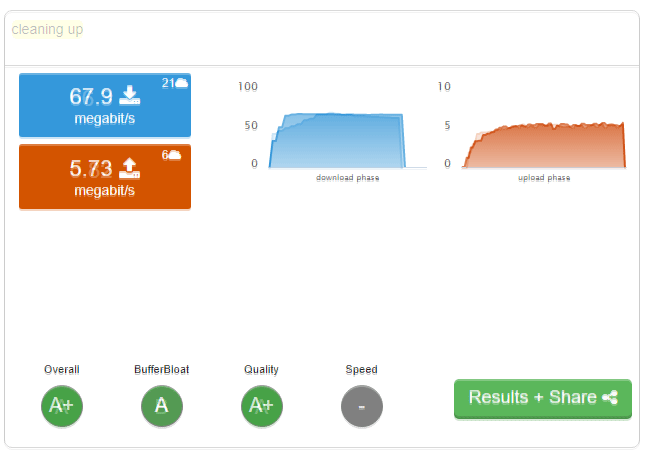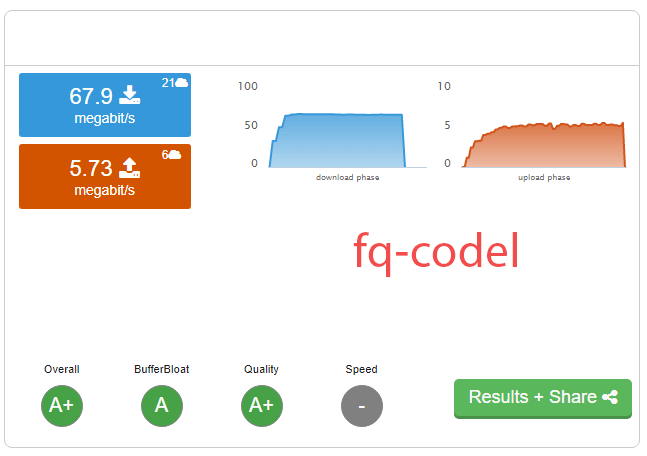
FreshJR
Very Senior Member
Welcome to FreshJR's Adaptive QOS modification script!
Issues with Adaptive QoS:
Adaptive QOS works amazing, but I have decided to tweak it as I have a few issues with its performance out of the box.
Some of the issues are as follows:
Issue 1:
Issue 2:
The script builds on-top of adaptive QoS and brings various improvements to the underlying parameters and logic.
Unidentified traffic priority is now adjustable in relation to other traffic groups.
(released 03/07/2019)
Issues with Adaptive QoS:
Adaptive QOS works amazing, but I have decided to tweak it as I have a few issues with its performance out of the box.
Some of the issues are as follows:
Issue 1:
The first issue is caused by the traffic groups. More specifically, the issue is caused by the existence of the default category. Unidentified traffic goes to the Default category. I would like it to go to Others instead.
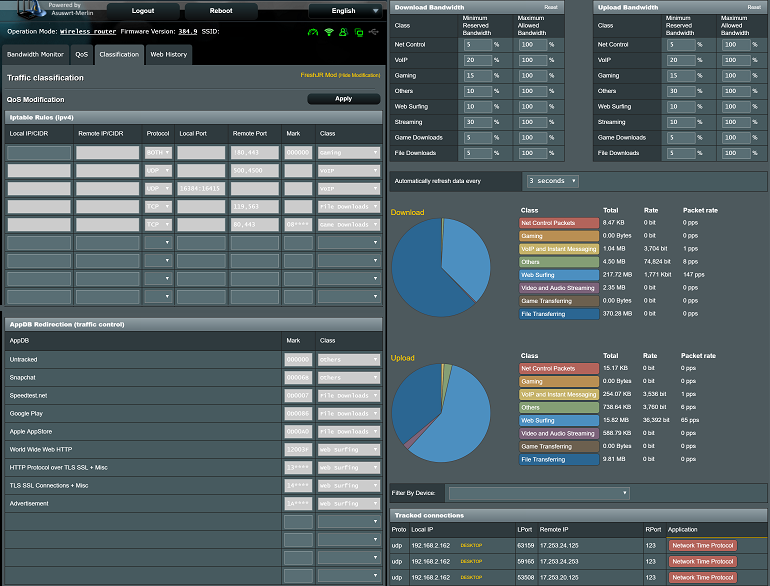
If you go to the QOS statistics, it shows you your traffic priorities and the last 3 seconds of each categories utilization. My setup is as follows.
Class Total Rate Packet rate
This will cause correctly identified traffic like neflix, youtube, filedownloads, torrents, and web surfing to ALL have greater priority than my poor old VOIP traffic. I wanted to have VOIP get first priority, but it seems to be getting the wrong end of the stick.
This negative effect extends to poor gaming performance as well. Many games are undetected and will also get the same wrong end of the stick.
It's a shame that the default category does not have adjustable priority. My scripts fixes that! A workaround I have performed is to route unidentified traffic into the rarely used, but webUI adjustable, Others category. With this you can punish known bandwidth hogs to give them worse priority than unknown traffic. Use as desired!
Class Total Rate Packet rate
- Net Control Packets
- VoIP and Instant Messaging
- Gaming
- Others
- Web Surfing
- Video and Audio Streaming
- File Transferring
- Default
This will cause correctly identified traffic like neflix, youtube, filedownloads, torrents, and web surfing to ALL have greater priority than my poor old VOIP traffic. I wanted to have VOIP get first priority, but it seems to be getting the wrong end of the stick.
This negative effect extends to poor gaming performance as well. Many games are undetected and will also get the same wrong end of the stick.
It's a shame that the default category does not have adjustable priority. My scripts fixes that! A workaround I have performed is to route unidentified traffic into the rarely used, but webUI adjustable, Others category. With this you can punish known bandwidth hogs to give them worse priority than unknown traffic. Use as desired!
Issue 2:
The largest issue with Asus's implementation of QOS is with their rate/ceil class values.
Issue 3:UPDATE: I am happy to say Asus partially addressed the poorly configured rates in v382 and up! This is a step in the right direction, but I still do not find their new configuration optimal.
The QOS categories each have an individual rate/ceil defined.
So what is this rate or ceil you may ask?
Rate = Minimum reserved bandwidth for a QOS container
Ceiling = Maximum bandwidth allowed for a QOS container
Note in this post: QOS container = QOS category = QOS Class. I will be using all terms interchangeably
To understand how this could be a problem you have to know how rate/ciel work in practice. Here's a summary.
Available bandwidth goes to container 1 until it hits rate. Then it will go to container 2 until rate, and so on up to container 7. At this point there will be a lot of unused bandwidth available. This bandwidth will go back to container 1 until it hits its ceil, then container 2 until ceil, and so on up to container 7. No bandwidth is wasted!
Lets look at some examples, with a 100 mbps connection for easy numbers.
In my script these rates are defined as percentages of total download bandwidth and are adjustable to your liking. This means no matter how much the network is constrained, various types of traffic should still flow.
There is one issue still outstanding that bugs me. Inside each container, that traffic has to go through the rate/ciel process again to divide up the available traffic per device requesting it. Once again, a certain manufacturer has setup guaranteed rates of 0.128 mbps per LAN client. This can lead to a situation where one user eats all the bandwidth within a container and starves everyone else if viewing a fast enough data source.
As a result, I only recommend "default" device priority so everyone get's a sane allotment of bandwidth.
The QOS categories each have an individual rate/ceil defined.
So what is this rate or ceil you may ask?
Rate = Minimum reserved bandwidth for a QOS container
Ceiling = Maximum bandwidth allowed for a QOS container
Note in this post: QOS container = QOS category = QOS Class. I will be using all terms interchangeably
Available bandwidth goes to container 1 until it hits rate. Then it will go to container 2 until rate, and so on up to container 7. At this point there will be a lot of unused bandwidth available. This bandwidth will go back to container 1 until it hits its ceil, then container 2 until ceil, and so on up to container 7. No bandwidth is wasted!
Lets look at some examples, with a 100 mbps connection for easy numbers.
Example Setup 1 (Okay):
Example Setup 2 (GOOD):
Example Setup 3 (TERRIBLE):
I will leave it up to your imagination as to who implemented a 0.128 mbps guaranteed rate per QOS container. They have the knobs to adjust these numbers but instead decided not to allow users to adjust them while themselves messing up the initial positions.
Code:
Downloads container 1 40 mbps rate / 100 mbps ciel 1000 mbps supplied by server.
Web Surfing container 2 10 mbps rate / 100 mbps ciel 5 mbps needed
Streaming container 3 20 mbps rate / 100 mbps ciel 30 mbps video stream
What would happen is as follows:
Downloads 75 mbps
Web Surfing 5 mbp
Streaming 20 mbps <--- Suffering because of download priority
Bad setup in my opinion because I do not agree in reducing streaming quality to speed up a file transfer.
This is a non issue since it is a preference setup by the user. They deem whats appropriate.Example Setup 2 (GOOD):
Code:
Same as above but with better container priorities
Web Surfing container 1 10 mbps rate / 100 mbps ciel 5mbps needed
Streaming container 2 20 mbps rate / 100 mbps ciel 30mbps video stream
Downloads container 3 40 mbps rate / 100 mbps ciel 1000 mbps supplied by server.
What would happen is as follows:
Web Surfing 5mbps used
Streaming 30mbps used
Downloads 65mbps used <-- Bandwidth taken from here if needed
Optimal setup in my opinion since every category has reasonable guaranteed bandwidth, same as the last setup.
The difference is that excess bandwidth is offered to categories in a logical order for my usage.Example Setup 3 (TERRIBLE):
Code:
Same as above but different is container rates (128 kbps each = 0.128 mbps)
Web Surfing container 1 0.128 mbps rate / 100 mbps ciel 5 mbps needed
Downloads container 2 0.128 mbps rate / 100 mbps ciel 1000 mbps supplied by server.
Streaming container 3 0.128 mbps rate / 100 mbps ciel 30 mbps video stream
VOIP container 4 0.128 mbps rate / 100 mbps ciel 2 mbps voice
Gaming container 5 0.128 mbps rate / 100 mbps ciel 1 mbps gaming
What would happen is as follows:
Web Surfing 5 mbps used
Downloads 94.6 mbps used
Streaming 0.128 mbps used <- DEAD
VOIP 0.128 mbps used <- DEAD
Gaming 0.128 mbps used <- DEAD
Terrible setup in my opinion.
I would never want traffic in any category to completely stall.
There are no user options to correct this.In my script these rates are defined as percentages of total download bandwidth and are adjustable to your liking. This means no matter how much the network is constrained, various types of traffic should still flow.
There is one issue still outstanding that bugs me. Inside each container, that traffic has to go through the rate/ciel process again to divide up the available traffic per device requesting it. Once again, a certain manufacturer has setup guaranteed rates of 0.128 mbps per LAN client. This can lead to a situation where one user eats all the bandwidth within a container and starves everyone else if viewing a fast enough data source.
As a result, I only recommend "default" device priority so everyone get's a sane allotment of bandwidth.
No lengthy write up here. The issue is that we cannot create custom rules to fit any additional needs or deficiencies with the traffic definitions database!
Overview of FreshJR QoS:
The script builds on-top of adaptive QoS and brings various improvements to the underlying parameters and logic.
Unidentified traffic priority is now adjustable in relation to other traffic groups.
Rates have been modified into more optimal defaults.
Identified traffic can have its destination adjusted
Identified traffic can have its destination adjusted
Custom rules can be created by filtering on a variety of elements.
Results of modifications can be seen in the tracked connections table.
Improvements for Gaming along with a gaming rule can be applied to user-specified devices.
Qos can be left alone and function great with improved defaults.
Qos can be extensively customized if you have specific needs.
FreshJR QOS v8.8Results of modifications can be seen in the tracked connections table.
Improvements for Gaming along with a gaming rule can be applied to user-specified devices.
Qos can be left alone and function great with improved defaults.
Qos can be extensively customized if you have specific needs.
(released 03/07/2019)

Script Changes Unidentified traffic destination away from "Defaults" into "Others"
Script Changes HTTPS traffic destination away from "Net Control" into "Web Surfing"
Script Changes Guaranteed Bandwidth per QOS category into logical percentages of upload and download.
Script Repurposes "Defaults" to contain "Game Downloads"
"Game Downloads" container moved into 6th position
"Lowest Defined" container moved into 7th position
Script includes misc hardcoded rules
(Wifi Calling) - UDP traffic on remote ports 500 & 4500 moved into VOIP
(Facetime) - UDP traffic on local ports 16384 - 16415 moved into VOIP
(Usenet) - TCP traffic on remote ports 119 & 563 moved into Downloads
(Gaming) - Gaming TCP traffic from remote ports 80 & 443 moved into Game Downloads.
(Snapchat) - Moved into Others
(Speedtest.net) - Moved into Downloads
(Google Play) - Moved into Downloads
(Apple AppStore)- Moved into Downloads
(Advertisement) - Moved into Downloads
(VPN Fix) - Router VPN Client upload traffic moved into Downloads instead of whitelisted
(VPN Fix) - Router VPN Client download traffic moved into Downloads instead of showing up in Uploads
(Gaming) - Unidentified traffic for specified devices, not originating from ports 80/443, moved into "Gaming"
Gaming Rule Note
Gaming traffic originating from ports 80 & 443 is primarily downloads & patches (some lobby/login protocols mixed within)
Manually configurable rule will take untracked traffic, not originating from 80/443, for specified devices and place it into Gaming
Use of this gaming rule REQUIRES devices to have a continous static ip assignment && this range needs to be defined in the script
Script Changes HTTPS traffic destination away from "Net Control" into "Web Surfing"
Script Changes Guaranteed Bandwidth per QOS category into logical percentages of upload and download.
Script Repurposes "Defaults" to contain "Game Downloads"
"Game Downloads" container moved into 6th position
"Lowest Defined" container moved into 7th position
Script includes misc hardcoded rules
(Wifi Calling) - UDP traffic on remote ports 500 & 4500 moved into VOIP
(Facetime) - UDP traffic on local ports 16384 - 16415 moved into VOIP
(Usenet) - TCP traffic on remote ports 119 & 563 moved into Downloads
(Gaming) - Gaming TCP traffic from remote ports 80 & 443 moved into Game Downloads.
(Snapchat) - Moved into Others
(Speedtest.net) - Moved into Downloads
(Google Play) - Moved into Downloads
(Apple AppStore)- Moved into Downloads
(Advertisement) - Moved into Downloads
(VPN Fix) - Router VPN Client upload traffic moved into Downloads instead of whitelisted
(VPN Fix) - Router VPN Client download traffic moved into Downloads instead of showing up in Uploads
(Gaming) - Unidentified traffic for specified devices, not originating from ports 80/443, moved into "Gaming"
Gaming Rule Note
Gaming traffic originating from ports 80 & 443 is primarily downloads & patches (some lobby/login protocols mixed within)
Manually configurable rule will take untracked traffic, not originating from 80/443, for specified devices and place it into Gaming
Use of this gaming rule REQUIRES devices to have a continous static ip assignment && this range needs to be defined in the script
Last edited: