Hi
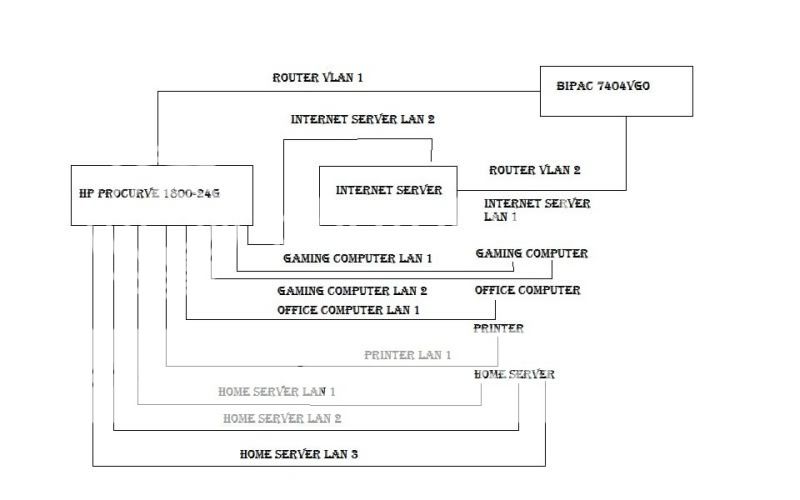
I'm rethinking to my home lan. Now it's Mixed cable/wi-fi lan that start with with an ADSL router USR9108 and two wifi extender. the goal is to isolate a computer which must make as internet server (p2p, wb ftp) so it must accessible from the internet. In the same time I need that rest of the internal lan can't be accesible if my internet server will be hacked. I think a these schema
ADSL modem ---> G108T ---> Vlan1 Internet server
|------> Vlan2
|------> HOME PC1
|------> HOME PC2 link1
|------> HOME PC2 link2
|------> HOME SERVER link1
|------> HOME SERVER link2
|------> WNDR3700 for Wi-fi support
Is this a good way to secure my computers?
I also need to link HOME PC1 to the internet server I need two lan card, two different ip address, right?
Is the 16 port swich (8 port could be a limit for the future) by netgear a valid product?
Is the MBR624GU adsl router a good router (for good router I intend a router which is capable to reconnect the ADSL line automatically (the usr 9108 isn't.....)
Which extender I need to use to extend the wi-fi signal?
Regards
Ugo
I'm rethinking to my home lan. Now it's Mixed cable/wi-fi lan that start with with an ADSL router USR9108 and two wifi extender. the goal is to isolate a computer which must make as internet server (p2p, wb ftp) so it must accessible from the internet. In the same time I need that rest of the internal lan can't be accesible if my internet server will be hacked. I think a these schema
ADSL modem ---> G108T ---> Vlan1 Internet server
|------> Vlan2
|------> HOME PC1
|------> HOME PC2 link1
|------> HOME PC2 link2
|------> HOME SERVER link1
|------> HOME SERVER link2
|------> WNDR3700 for Wi-fi support
Is this a good way to secure my computers?
I also need to link HOME PC1 to the internet server I need two lan card, two different ip address, right?
Is the 16 port swich (8 port could be a limit for the future) by netgear a valid product?
Is the MBR624GU adsl router a good router (for good router I intend a router which is capable to reconnect the ADSL line automatically (the usr 9108 isn't.....)
Which extender I need to use to extend the wi-fi signal?
Regards
Ugo