I've got an Asus RT-AX3000 (RT-AX58U) with firmware 3.0.0.4.388_25127 and Entware. I think I've got it so that Entware is enabled after a reboot only if I SSH in and run some ln and mount commands. My router joined the botnet starting yesterday morning, and I'm glad I found this thread.
The malware runs 4 processes in a parent/child chain, replaces the stat process names with "sshd", and removes the cmdline from the process tables. I can tell which process is doing the work by running top and seeing which one is using up CPU, and the timing lines up with my internet connection degrading severely. I tried finding out more about what this malware is doing using ps, pstree, and netstat, but didn't get very far. But then I tried tcpdump, and I was able to see in Wireshark that my router was part of a botnet sending a TCP ACK flood with 1360 bytes of junk payload to a hosting provider named HostSG out of Singapore (IP addresses 203.175.172.0 - 203.175.173.255).
I feel bad for the hosting provider. My ISP gives me 20 Mbps upstream bandwidth, but this malware was able to hit 650 Mbps as seen on the router's Traffic Monitor page. I think my ISP gives me bursting upload speed too, which the malware took advantage of by doing the flood for just 20 seconds or so and then waiting 2 or 3 minutes before flooding again.
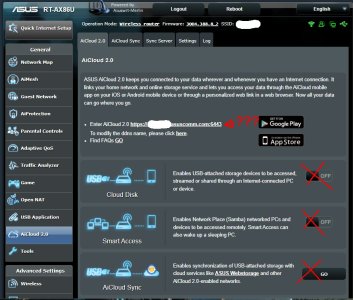
Anyways, I turned off Asus AiCloud 2.0 Cloud Disk and rebooted the router, but I got hacked again 3 hours later. I've now also turned off Asus AiCloud 2.0 Smart Access and rebooted, and so far I've gone the longest yet without any malware running. Fingers crossed that I'm free and clear now.
BTW, I've got the router log going to my Raspberry Pi through rsyslog, and I noticed in there that the weekly Let's Encrypt and dynamic DNS refresh ran just minutes before the very first time my internet connection degraded (I'm running SmokePing on my Pi). But that could be a coincidence. In the log, the refresh starts with "cmd service restart_letsencrypt" and ends with "Listening for NAT-PMP/PCP traffic".