ZebMcKayhan
Very Senior Member
Great!Whoops!
In the Beta4.14b3 I took note of your suggestion to differentiate between the actual IPv6 configuration status and changed
toCode:[ "$(nvram get ipv6_service != "disabled")" ] && USE_IPV6="Y"; IPV6_TXT="(IPv6) "
I've pushed the patchCode:IPV6_SERVICE=$(nvram get ipv6_service) if [ "$IPV6_SERVICE" != "disabled" ];then ipv6pt|dhcp6) # ip -6 addr | grep "scope global" USE_IPV6="Y"; IPV6_TXT="(IPv6) " # 4.08 ;; 6to4|6in4|6rd) : ;; other) : ;; spoof|simulate) USE_IPV6="Y"; IPV6_TXT="(IPv6) Simulate " # v4.14 ;; esac fi
to Github Dev Branch.
- Doh!
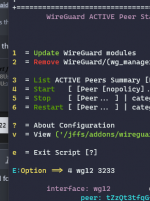
Altough while experimenting I'm keeping wgm to ipv4 only.
Still cant wrap my head around why its not accepting the default route other then for local packages. Perhaps I need to add the [scope: global] to it. Or perhaps I need to add a proper default route since my system is missing this:
Code:
ip -6 route add default dev wg11I will probably need to generate a proper ULA to use within my local network, but I guess a made-up one will do for the moment.
There is a chance that the wg server does not accept packages with a different ipv6 source adress than assigned and we might need to find out if asus/ @RMerlin has included some kind of NPTv6 and how to use it.
//Zeb