Viktor Jaep
Part of the Furniture
Hey everyone... I thought it would be fun to give Unbound a try today, and see how this worked compared to using my standard DoT setup with Quad9 under the WAN configuration... This setup has worked great for years, so lets break it and try something new! 
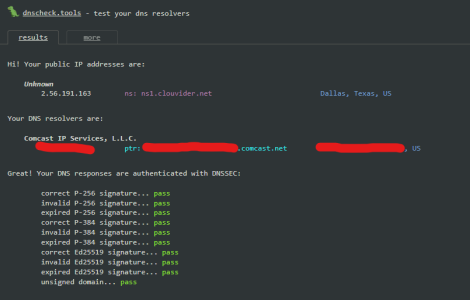
After getting Unbound installed and running, I hit the https://dnscheck.tools site, and it apparently is doing everything right by design... that is, my WAN IP is now considered my DNS resolver...

I ran the DNSMON tool that Eibgrad created, and it shows this:

So there's a TON of plaintext DNS query traffic happening on port 53 that could easily be intercepted by the ISP (or others).
What's the best practice to ensure that your DNS queries to the root servers are also encrypted? I noticed that Unbound also has a DoT function, but starts getting confusing as it still somehow uses your WAN DNS configuration somehow that then uses Quad9... so then what's the purpose of running Unbound?
I thought perhaps it would be a good idea to obfuscate root DNS lookups by using the Unbound feature to "Bind Unbound to VPN"... but will need to build some automation in VPNMON-R2 to make this happen when VPN slots change up, and would need to catch Unbound up after the switch. Is this a good way to go?
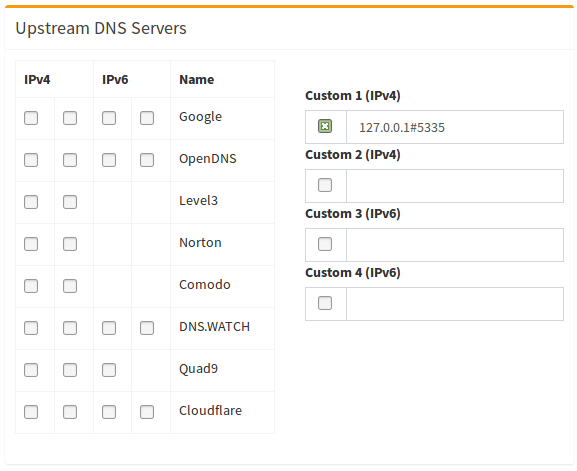
After installing Unbound, my WAN DNS setup never really changed... and I'm guessing even though everything is still filled out, Unbound doesn't really use this... right? So I'm wondering if there's a good easy way to check if Unbound is actually doing its job and making connections with the root servers?

After getting Unbound installed and running, I hit the https://dnscheck.tools site, and it apparently is doing everything right by design... that is, my WAN IP is now considered my DNS resolver...
I ran the DNSMON tool that Eibgrad created, and it shows this:
So there's a TON of plaintext DNS query traffic happening on port 53 that could easily be intercepted by the ISP (or others).
What's the best practice to ensure that your DNS queries to the root servers are also encrypted? I noticed that Unbound also has a DoT function, but starts getting confusing as it still somehow uses your WAN DNS configuration somehow that then uses Quad9... so then what's the purpose of running Unbound?
I thought perhaps it would be a good idea to obfuscate root DNS lookups by using the Unbound feature to "Bind Unbound to VPN"... but will need to build some automation in VPNMON-R2 to make this happen when VPN slots change up, and would need to catch Unbound up after the switch. Is this a good way to go?
After installing Unbound, my WAN DNS setup never really changed... and I'm guessing even though everything is still filled out, Unbound doesn't really use this... right? So I'm wondering if there's a good easy way to check if Unbound is actually doing its job and making connections with the root servers?
Attachments
Last edited: