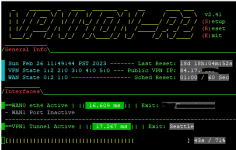
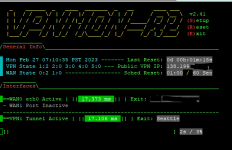
{
"public_name": "Acamar",
"country_name": "United States",
"country_code": "us",
"location": "Miami",
"continent": "America",
"bw": 84,
"bw_max": 1000,
"users": 56,
"currentload": 8,
"ip_v4_in1": "173.44.55.154",
"ip_v4_in2": "173.44.55.156",
"ip_v4_in3": "173.44.55.157",
"ip_v4_in4": "173.44.55.158",
"ip_v6_in1": "2607:ff48:aa81:200:fb8:68cd:5d60:f39d",
"ip_v6_in2": "2607:ff48:aa81:200:e636:daec:ff92:fb1c",
"ip_v6_in3": "2607:ff48:aa81:200:7624:912a:38e8:a606",
"ip_v6_in4": "2607:ff48:aa81:200:a3a7:a46c:8a8c:3a02",
"ip_entry": "173.44.55.154",
"ip_entry_alt": "173.44.55.156",
"health": "ok"
}