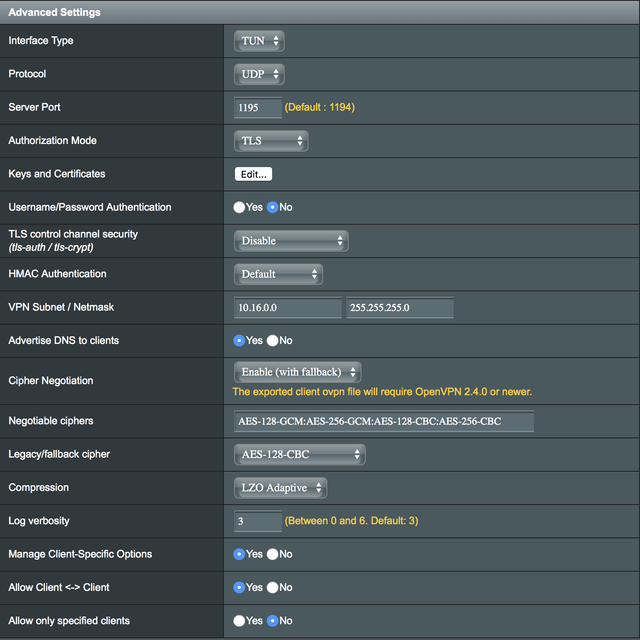
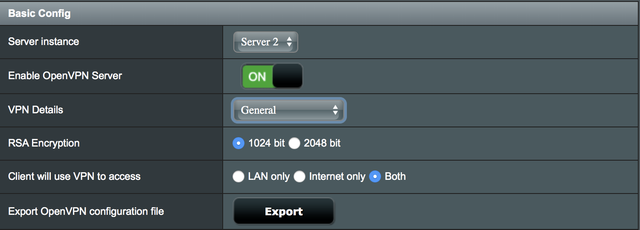
I've just upgraded from an Asus AC56 to an AC88. I've updated the AC88 to run the Merlin firmware and all is going swimmingly apart from my OpenVPN network.
On the AC56 I could VPN to the router and see my home network without any faffing about. The AC88 shows extra options that need to be activated specifically (I think) the client-to-client option in order to allow my home network to be viewable. Unfortunately, no matter what I activate, nor what options I manually type in, I'm not able to view my home network through the VPN. I seem to have tried everything I can so I'm wondering if anyone out there has managed to get this working or knows of a fix?
I'm aware of several threads relating to OpenVPN and Asus routers but despite following the instructions in them, I've not been able to get client to client over TUN to work.
PS I can access the home network by using the TAP protocol. However, I need to use TUN for my iPad to connect. As stated, this worked perfectly on the AC56.
On the AC56 I could VPN to the router and see my home network without any faffing about. The AC88 shows extra options that need to be activated specifically (I think) the client-to-client option in order to allow my home network to be viewable. Unfortunately, no matter what I activate, nor what options I manually type in, I'm not able to view my home network through the VPN. I seem to have tried everything I can so I'm wondering if anyone out there has managed to get this working or knows of a fix?
I'm aware of several threads relating to OpenVPN and Asus routers but despite following the instructions in them, I've not been able to get client to client over TUN to work.
PS I can access the home network by using the TAP protocol. However, I need to use TUN for my iPad to connect. As stated, this worked perfectly on the AC56.