Hello
I had been running 384.18 on my 86U fine with no issues. Nothing "exotic" with my needs, apart from using a VPN client. The config for that client is generated successfully by AIRVPN, the online company I use for my VPN needs.
Noted the potential issues with the JFFS partition due to its reduction in size.
Backed up the JFFS partition(12mb or so) but then, router gone through many firmware revisions and settings, formatted the partition on reboot and so rebooted.
All went well with the newly created JFFS partition mounted, about 1.3mb in size of 48mb available.
Then backed up that JFFS partition again, just in case.
Downloaded and flashed successfully with the 384.19 firmware.
Rebooted and noted that the JFFS partition was not mounted.
Selected to reformat that partition and reboot.
Rebooted and all seemed well. 1.34mb of 47mb used on the JFFS partition.
Connected fine to the Internet, no issues so far.
The problem......
Created usual config from AIRVPN and uploaded it as usual into Client 1 for the VPN.
Rather than the usual immediate connection this time it does not connect and remains "connecting"
Errors noted in the system log.
Reset the Client 1 to defaults. Applied and the settings from the config then went empty but the Client 1 still changed to "connecting" even tho it was set to "off".
That would not change.
Reboot router would not change.
Reboot router and format JFFS and then it was fine with no remaining "connecting" issues
This time I repeated the above but tried VPN Client 2.
Errors within System log......
Aug 28 09:07:25 ovpn-client2[4083]: OpenVPN 2.4.9 arm-buildroot-linux-gnueabi [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Aug 14 2020
Aug 28 09:07:25 ovpn-client2[4083]: library versions: OpenSSL 1.1.1g 21 Apr 2020, LZO 2.08
Aug 28 09:07:25 ovpn-client2[4084]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Aug 28 09:07:25 ovpn-client2[4084]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Aug 28 09:07:25 ovpn-client2[4084]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Aug 28 09:07:28 ovpn-client2[4084]: TCP/UDP: Preserving recently used remote address: [AF_INET]89.238.150.42:443
Aug 28 09:07:28 ovpn-client2[4084]: Socket Buffers: R=[524288->524288] S=[524288->524288]
Aug 28 09:07:28 ovpn-client2[4084]: UDP link local: (not bound)
Aug 28 09:07:28 ovpn-client2[4084]: UDP link remote: [AF_INET]89.238.150.42:443
Aug 28 09:07:28 ovpn-client2[4084]: TLS: Initial packet from [AF_INET]89.238.150.42:443, sid=2e338ce1 b70ce898
Aug 28 09:07:28 ovpn-client2[4084]: VERIFY OK: depth=1, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=airvpn.org CA, emailAddress=
[email protected]
Aug 28 09:07:28 ovpn-client2[4084]: VERIFY KU OK
Aug 28 09:07:28 ovpn-client2[4084]: Validating certificate extended key usage
Aug 28 09:07:28 ovpn-client2[4084]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Aug 28 09:07:28 ovpn-client2[4084]: VERIFY EKU OK
Aug 28 09:07:28 ovpn-client2[4084]: VERIFY OK: depth=0, C=IT, ST=IT, L=Perugia, O=airvpn.org, CN=Arion, emailAddress=
[email protected]
Aug 28 09:07:28 ovpn-client2[4084]: Control Channel: TLSv1.2, cipher TLSv1.2 DHE-RSA-AES256-GCM-SHA384, 4096 bit RSA
Aug 28 09:07:28 ovpn-client2[4084]: [Arion] Peer Connection Initiated with [AF_INET]89.238.150.42:443
Aug 28 09:07:29 ovpn-client2[4084]: SENT CONTROL [Arion]: 'PUSH_REQUEST' (status=1)
Aug 28 09:07:29 ovpn-client2[4084]: PUSH: Received control message: 'PUSH_REPLY,comp-lzo no,redirect-gateway ipv6 def1 bypass-dhcp,dhcp-option DNS 10.17.244.1,dhcp-option DNS6 fde6:7a:7d20:df4::1,tun-ipv6,route-gateway 10.17.244.1,topology subnet,ping 10,ping-restart 60,ifconfig-ipv6 fde6:7a:7d20:df4::10f7/64 fde6:7a:7d20:df4::1,ifconfig 10.17.244.249 255.255.255.0,peer-id 1,cipher AES-256-GCM'
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: timers and/or timeouts modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: compression parms modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: --ifconfig/up options modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: route options modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: route-related options modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: peer-id set
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: adjusting link_mtu to 1625
Aug 28 09:07:29 ovpn-client2[4084]: OPTIONS IMPORT: data channel crypto options modified
Aug 28 09:07:29 ovpn-client2[4084]: Data Channel: using negotiated cipher 'AES-256-GCM'
Aug 28 09:07:29 ovpn-client2[4084]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Aug 28 09:07:29 ovpn-client2[4084]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Aug 28 09:07:29 ovpn-client2[4084]: GDG6: remote_host_ipv6=n/a
Aug 28 09:07:29 ovpn-client2[4084]: TUN/TAP device tun12 opened
Aug 28 09:07:29 ovpn-client2[4084]: TUN/TAP TX queue length set to 1000
Aug 28 09:07:29 ovpn-client2[4084]: /sbin/ifconfig tun12 10.17.244.249 netmask 255.255.255.0 mtu 1500 broadcast 10.17.244.255
Aug 28 09:07:29 lldpd[1368]: removal request for address of 10.17.244.249%22, but no knowledge of it
Aug 28 09:07:29 lldpd[1368]: removal request for address of 10.17.244.249%22, but no knowledge of it
Aug 28 09:07:29 ovpn-client2[4084]: /sbin/ifconfig tun12 add fde6:7a:7d20:df4::10f7/64
Aug 28 09:07:29 ovpn-client2[4084]: Linux ifconfig inet6 failed: external program exited with error status: 1
Aug 28 09:07:29 ovpn-client2[4084]: Exiting due to fatal error
Now what happens is that the Client 2 VPN will remain trying to connect even if I try and revert the settings to the default. The only way that I have found to stop that is the reformat the JFFS partition and then everything "stops" and no client is trying to connect, which fails.
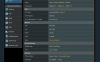
Screen shot 1 thumbnail shows the status of the VPN client
View attachment 25826
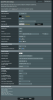
Screen Shot 2 thumbnail shows the Open VPN client settings and even though it is set to "off" it still tries to connect, but there are those errors noted in the system logs.
View attachment 25825
any advice please, keeping that advice "simple" if possible

EDIT: Tried to reset Client 2 VPN to the default settings. The logs show.....
Aug 28 09:36:04 rc_service: httpd 1267:notify_rc stop_vpnclient2;clearvpnclient2
Aug 28 09:36:04 openvpn: Resetting client (unit 2) to default settings
Aug 28 09:36:24 rc_service: httpd 1267:notify_rc restart_vpnclient2
Aug 28 09:36:24 ovpn-client2[14058]: Options error: You must define CA file (--ca) or CA path (--capath)
Aug 28 09:36:24 ovpn-client2[14058]: Use --help for more information.
Aug 28 09:36:24 openvpn: Starting OpenVPN client 2 failed!
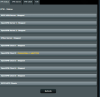
but the client now shows......
status.....
View attachment 25827
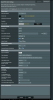
settings...
View attachment 25828
even though it is set to "off" and should not be trying to connect
To return a "clear" status to the VPN client I reset the JFFS partition and rebooted. Partition mounted fine and no "connection" issues noted with the VPN clients. But they will no longer connect as they did previously without generating the noted error in the system log

 www.snbforums.com
www.snbforums.com