bayern1975
Very Senior Member
hello, i have tested about 10 different dnscrypt-proxy servers today but all shows IP of my DNS provider? i tested at dnsleaktest.com
what could be wrong? i have no errors in syslog my asus rt-ac68u.....is possible the dnsleaktest site do not shows properly? is there other solution to test if dnscrypt-proxy working ok or not?
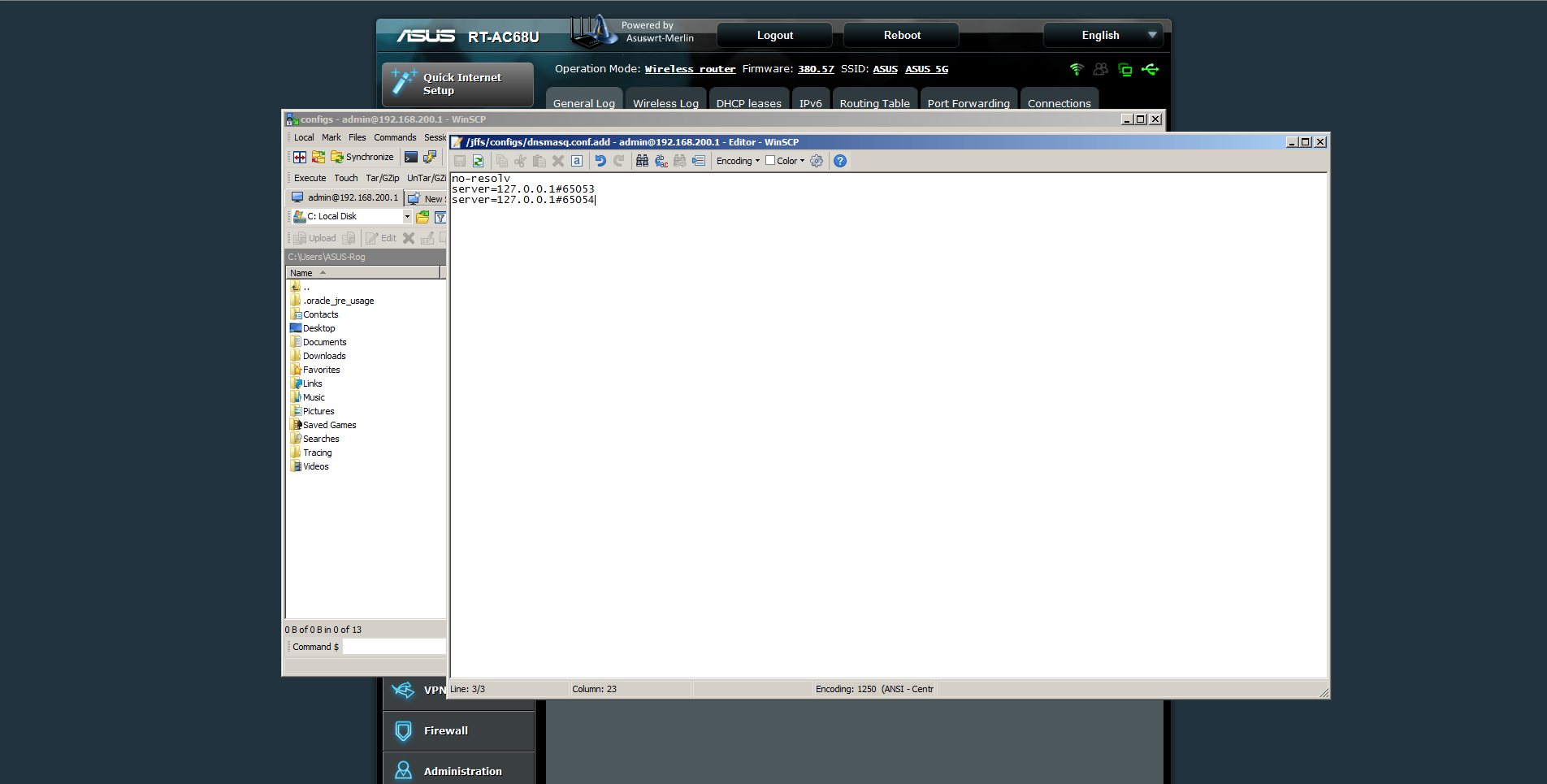
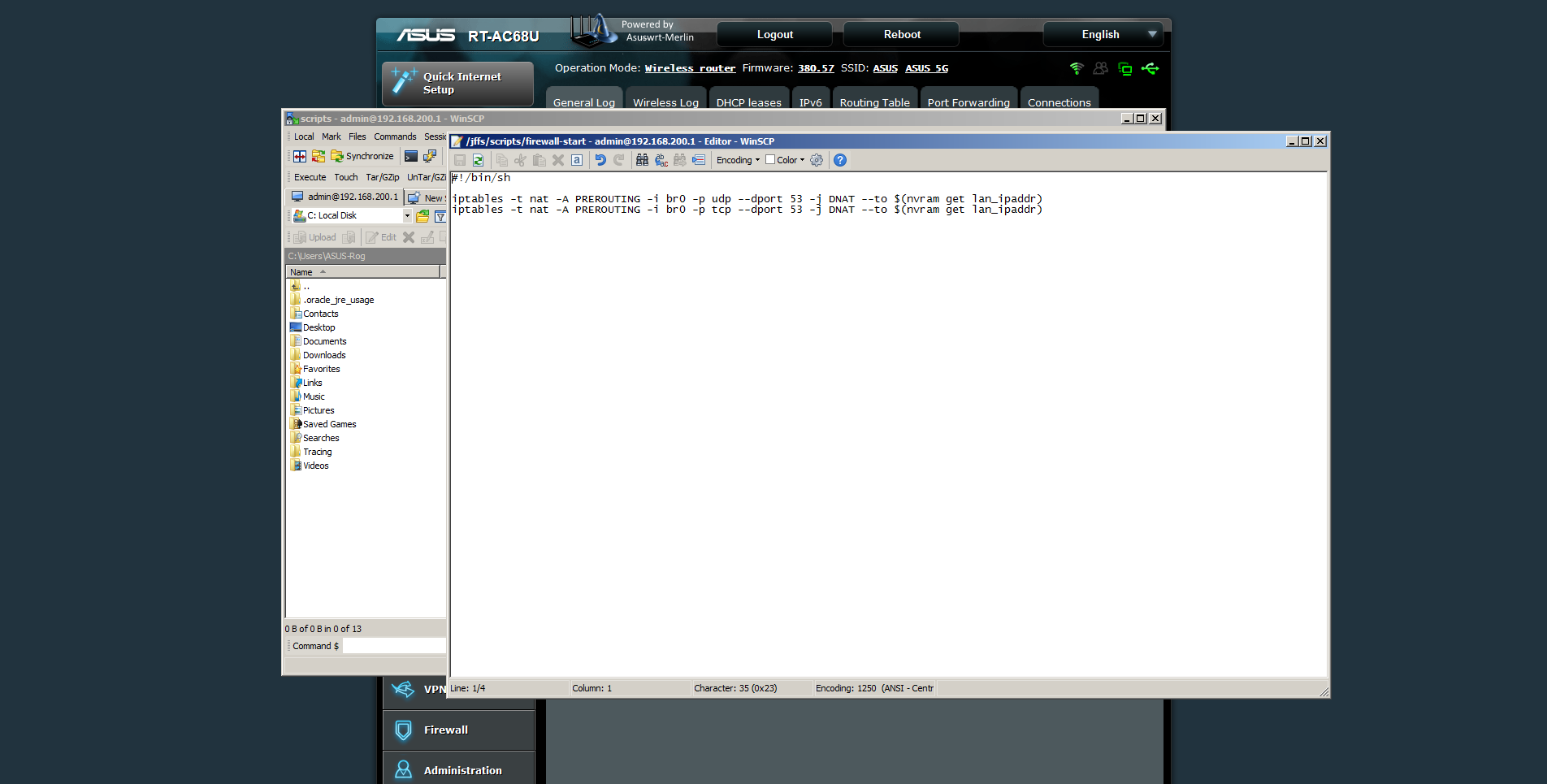
here is my syslog, maybe someone will tell me if something missing there?
what could be wrong? i have no errors in syslog my asus rt-ac68u.....is possible the dnsleaktest site do not shows properly? is there other solution to test if dnscrypt-proxy working ok or not?
here is my syslog, maybe someone will tell me if something missing there?
Code:
Feb 21 13:06:21 pppd[511]: System time change detected.
Feb 21 13:06:21 dnscrypt-proxy: + DNS Security Extensions are supported
Feb 21 13:06:21 dnscrypt-proxy: + Namecoin domains can be resolved
Feb 21 13:06:21 dnscrypt-proxy: + Provider supposedly doesn't keep logs
Feb 21 13:06:21 dnscrypt-proxy[783]: Starting dnscrypt-proxy 1.6.0
Feb 21 13:06:21 dnscrypt-proxy[783]: Generating a new session key pair
Feb 21 13:06:21 dnscrypt-proxy[783]: Done
Feb 21 13:06:21 admin: Started from .
Feb 21 13:06:21 rc_service: hotplug 669:notify_rc restart_nasapps
Feb 21 13:06:21 kernel: Adding 523940k swap on /opt/swap. Priority:-1 extents:86 across:706552k
Feb 21 13:06:22 rc_service: service 770:notify_rc restart_ntpc
Feb 21 13:06:22 rc_service: waitting "restart_nasapps" via hotplug ...
Feb 21 13:06:22 iTunes: daemon is stopped
Feb 21 13:06:22 FTP Server: daemon is stopped
Feb 21 13:06:23 Samba Server: smb daemon is stopped
Feb 21 13:06:23 kernel: gro disabled
Feb 21 13:06:23 Timemachine: daemon is stopped
Feb 21 13:06:23 kernel: gro enabled with interval 2
Feb 21 13:06:24 Samba Server: daemon is started
Feb 21 13:06:25 rc_service: zcip 809:notify_rc start_firewall
Feb 21 13:06:25 rc_service: waitting "restart_nasapps" via hotplug ...
Feb 21 13:06:26 rc_service: zcip 809:notify_rc stop_dnsmasq
Feb 21 13:06:26 rc_service: waitting "start_firewall" via zcip ...
Feb 21 13:06:27 start_nat_rules: apply the nat_rules(/tmp/nat_rules_ppp0_eth0)!
Feb 21 13:06:28 dnsmasq[440]: exiting on receipt of SIGTERM
Feb 21 13:06:29 rc_service: zcip 809:notify_rc start_dnsmasq
Feb 21 13:06:29 custom script: Running /jffs/scripts/dnsmasq.postconf (args: /etc/dnsmasq.conf)
Feb 21 13:06:30 zcip client: configured 169.254.175.49
Feb 21 13:06:30 udpxy[841]: udpxy 1.0-Chipmunk (build 19) standard is starting
Feb 21 13:06:30 admin: AB-Solution added entries via dnsmasq.postconf
Feb 21 13:06:31 dnsmasq[853]: started, version 2.76-g41a8d9e cachesize 1500
Feb 21 13:06:31 dnsmasq[853]: DNSSEC validation enabled
Feb 21 13:06:31 dnsmasq[853]: DNSSEC signature timestamps not checked until first cache reload
Feb 21 13:06:31 dnsmasq[853]: warning: interface tun21 does not currently exist
Feb 21 13:06:31 dnsmasq[853]: warning: interface ppp1* does not currently exist
Feb 21 13:06:31 dnsmasq[853]: asynchronous logging enabled, queue limit is 5 messages
Feb 21 13:06:31 dnsmasq-dhcp[853]: DHCP, IP range 192.168.200.2 -- 192.168.200.254, lease time 1d
Feb 21 13:06:31 dnsmasq[853]: read /etc/hosts - 5 addresses
Feb 21 13:06:32 dnsmasq[853]: read /tmp/mnt/sda1/adblocking/blacklist.txt - 2 addresses
Feb 21 13:06:32 rc_service: ip-up 674:notify_rc start_dnsmasq
Feb 21 13:06:32 rc_service: waitting "stop_dnsmasq" via ip-up ...
Feb 21 13:06:33 custom script: Running /jffs/scripts/dnsmasq.postconf (args: /etc/dnsmasq.conf)
Feb 21 13:06:34 admin: AB-Solution added entries via dnsmasq.postconf
Feb 21 13:06:34 wan: finish adding multi routes
Feb 21 13:06:34 rc_service: ip-up 674:notify_rc stop_upnp
Feb 21 13:06:34 rc_service: waitting "start_dnsmasq" via ip-up ...
Feb 21 13:06:34 ntp: start NTP update
Feb 21 13:06:34 dnsmasq[878]: started, version 2.76-g41a8d9e cachesize 1500
Feb 21 13:06:34 dnsmasq[878]: DNSSEC validation enabled
Feb 21 13:06:34 dnsmasq[878]: DNSSEC signature timestamps not checked until first cache reload
Feb 21 13:06:34 dnsmasq[878]: warning: interface tun21 does not currently exist
Feb 21 13:06:34 dnsmasq[878]: warning: interface ppp1* does not currently exist
Feb 21 13:06:34 dnsmasq[878]: asynchronous logging enabled, queue limit is 5 messages
Feb 21 13:06:34 dnsmasq-dhcp[878]: DHCP, IP range 192.168.200.2 -- 192.168.200.254, lease time 1d
Feb 21 13:06:34 dnsmasq[878]: read /etc/hosts - 5 addresses
Feb 21 13:06:34 dnsmasq[878]: read /tmp/mnt/sda1/adblocking/blacklist.txt - 2 addresses
Feb 21 13:06:35 WAN Connection: WAN was restored.
Feb 21 13:06:35 rc_service: ip-up 674:notify_rc start_upnp
Feb 21 13:06:35 rc_service: waitting "stop_upnp" via ip-up ...
Feb 21 13:06:36 dnscrypt-proxy[783]: Unable to retrieve server certificates
Feb 21 13:06:36 ddns update: ez-ipupdate: starting...
Feb 21 13:06:37 dnscrypt-proxy[783]: Refetching server certificates
Feb 21 13:06:37 dnscrypt-proxy[783]: Server certificate #808464433 received
Feb 21 13:06:37 dnscrypt-proxy[783]: This certificate looks valid
Feb 21 13:06:37 dnscrypt-proxy[783]: Chosen certificate #808464433 is valid from [2016-02-22] to [2016-02-23]
Feb 21 13:06:37 dnscrypt-proxy[783]: Server key fingerprint is B572:F662:407C:4B19:A0E1:36DC:CACC:E17D:C88E:EB33:C857:E5A6:C7EC:94DC:92EE:FE68
Feb 21 13:06:37 dnscrypt-proxy[783]: Proxying from 127.0.0.1:65053 to 212.47.228.136:443
Feb 21 13:06:39 dnsmasq[878]: read /tmp/mnt/sda1/adblocking/hosts-adblock - 385307 addresses
Feb 21 13:06:40 dnsmasq[878]: using nameserver 95.176.233.13#53
Feb 21 13:06:40 dnsmasq[878]: using nameserver 193.189.160.13#53
Feb 21 13:08:27 ddns update: connected to dynupdate.no-ip.com (8.23.224.120) on port 80.
Feb 21 13:08:28 rc_service: ntp 835:notify_rc restart_upnp
Feb 21 13:08:28 ddns update: request successful
Feb 21 13:08:28 ddns update: asusddns_update: 0
Feb 21 13:08:29 udpxy[841]: udpxy 1.0-Chipmunk (build 19) standard is exiting with rc=[0]
Feb 21 13:08:29 rc_service: ntp 835:notify_rc restart_diskmon
Feb 21 13:08:29 dnsmasq[878]: now checking DNSSEC signature timestamps
Feb 21 13:08:29 disk_monitor: Finish
Feb 21 13:08:29 udpxy[892]: udpxy 1.0-Chipmunk (build 19) standard is starting
Feb 21 13:08:29 dnsmasq[878]: read /etc/hosts - 5 addresses
Feb 21 13:08:29 dnsmasq[878]: read /tmp/mnt/sda1/adblocking/blacklist.txt - 2 addresses
Feb 21 13:08:30 hour monitor: daemon is starting
Feb 21 13:08:30 ddns: ddns update ok
Feb 21 13:08:30 rc_service: ip-up 674:notify_rc start_vpnserver1
Feb 21 13:08:32 openvpn-routing: Refreshing policy rules for client 1
Feb 21 13:08:32 kernel: tun: Universal TUN/TAP device driver, 1.6
Feb 21 13:08:32 kernel: tun: (C) 1999-2004 Max Krasnyansky <maxk@qualcomm.com>
Feb 21 13:08:32 openvpn-routing: Allow WAN access to all VPN clients
Feb 21 13:08:32 disk monitor: be idle
Feb 21 13:08:32 openvpn-routing: Refreshing policy rules for client 2
Feb 21 13:08:32 openvpn-routing: Allow WAN access to all VPN clients
Feb 21 13:08:32 openvpn-routing: Refreshing policy rules for client 3
Feb 21 13:08:32 openvpn-routing: Allow WAN access to all VPN clients
Feb 21 13:08:33 pppd[511]: System time change detected.
Feb 21 13:08:33 openvpn-routing: Refreshing policy rules for client 4
Feb 21 13:08:33 openvpn-routing: Allow WAN access to all VPN clients
Feb 21 13:08:33 openvpn-routing: Refreshing policy rules for client 5
Feb 21 13:08:33 openvpn-routing: Allow WAN access to all VPN clients
Feb 21 13:08:33 kernel: ADDRCONF(NETDEV_UP): tun21: link is not ready
Feb 21 13:08:33 kernel: device tun21 entered promiscuous mode
Feb 21 13:08:34 rc_service: service 1023:notify_rc restart_dnsmasq
Feb 21 13:08:34 rc_service: waitting "start_vpnserver1" via ...
Feb 21 13:08:34 dnsmasq[878]: read /tmp/mnt/sda1/adblocking/hosts-adblock - 385307 addresses
Feb 21 13:08:34 dnsmasq[878]: using nameserver 95.176.233.13#53
Feb 21 13:08:34 dnsmasq[878]: using nameserver 193.189.160.13#53
Last edited: