dugaduga
Senior Member
Using the latest RT-AC68U 384.7-beta1,
I had this issue with both Ab-solution and Diversion. Dnsmasq restarting over and over... logs: https://pastebin.com/PRd7jJXj
This started after the latest entware and Diversion update. Hitting "apply" under lan/dhcp server typically fixed this issue, so long as it reassigned an ip. Disabling samba, doing sig checks, and diversion list updates would often trigger this bug, occasionally persisting after a reboot. I reverted to Ab-solution, for a few days everything was fine, with the updated entware packages.
3-4 days later it started again and went on for hours. In troubleshooting I had initiated factory defaults, reinstalled the latest firmware, re-applied all settings manually; hit apply lan multiple times, rebooted over and over, started and stopped ab solution to no avail, turned on and off automatic dns... withdrawing trendmicro privacy agreement, you name it.
It seems the DNScrypt servers were not working. I could access cached domains. Skynet blocked incoming packets. I tried multiple DNScrypt servers, including cloudflare as they previously worked when others were down or possibly blocked. I managed to get one or two domains loaded via browser... but that was about it. I'm wondering if the ISP was blocking my DNScrypt servers, or this dnsmasq/absolution restarting didn't allow for a proper DNS connectivity. Dnscrypt always successfully reported the latency of the dnscrypt servers.
Will dnsmasq/absolution do this if dnscrypt packets are being blocked or throttled?
I successfully started an openvpn client on the router, no changes. Finally, once I had assigned an IP to openvpn client and started browsing through the VPN, the problem suddenly stopped!
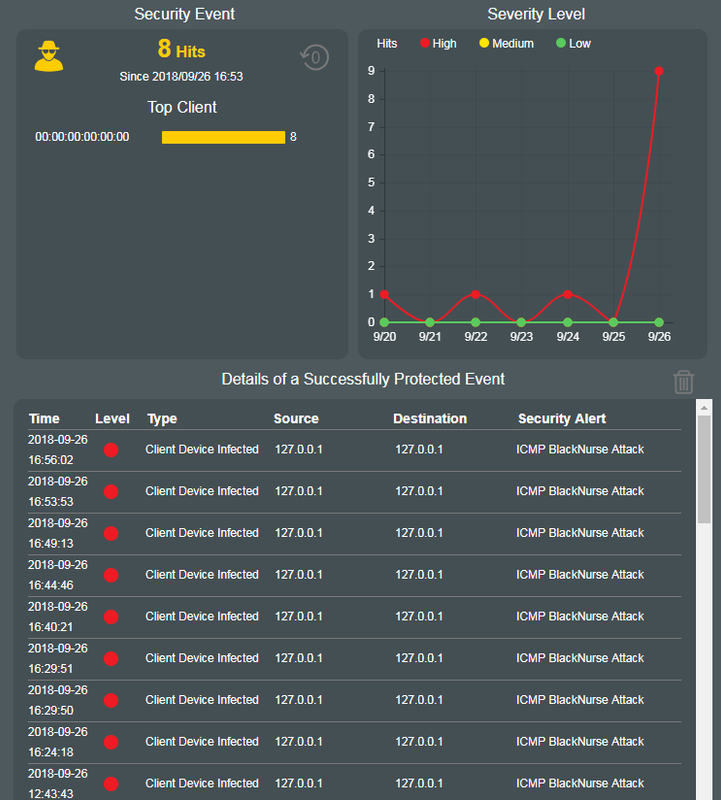
Summing up watchdog was restarting dnsmasq over and over again, ab-solution was doing the same, loading in and out of the ram. I was also getting icmp black nurse attacks from the loopback device while this was happening before, and immediately after factory default & firmware re-update; I had hardened all potential router vulnerabilities prior to plugging in wan and updated sigs immediately upon reboot. I suspect this was not an internal infection. Could this be a DNS ddos? Any Ideas?
@RMerlin, @thelonelycoder
I had this issue with both Ab-solution and Diversion. Dnsmasq restarting over and over... logs: https://pastebin.com/PRd7jJXj
This started after the latest entware and Diversion update. Hitting "apply" under lan/dhcp server typically fixed this issue, so long as it reassigned an ip. Disabling samba, doing sig checks, and diversion list updates would often trigger this bug, occasionally persisting after a reboot. I reverted to Ab-solution, for a few days everything was fine, with the updated entware packages.
3-4 days later it started again and went on for hours. In troubleshooting I had initiated factory defaults, reinstalled the latest firmware, re-applied all settings manually; hit apply lan multiple times, rebooted over and over, started and stopped ab solution to no avail, turned on and off automatic dns... withdrawing trendmicro privacy agreement, you name it.
It seems the DNScrypt servers were not working. I could access cached domains. Skynet blocked incoming packets. I tried multiple DNScrypt servers, including cloudflare as they previously worked when others were down or possibly blocked. I managed to get one or two domains loaded via browser... but that was about it. I'm wondering if the ISP was blocking my DNScrypt servers, or this dnsmasq/absolution restarting didn't allow for a proper DNS connectivity. Dnscrypt always successfully reported the latency of the dnscrypt servers.
Will dnsmasq/absolution do this if dnscrypt packets are being blocked or throttled?
I successfully started an openvpn client on the router, no changes. Finally, once I had assigned an IP to openvpn client and started browsing through the VPN, the problem suddenly stopped!
Summing up watchdog was restarting dnsmasq over and over again, ab-solution was doing the same, loading in and out of the ram. I was also getting icmp black nurse attacks from the loopback device while this was happening before, and immediately after factory default & firmware re-update; I had hardened all potential router vulnerabilities prior to plugging in wan and updated sigs immediately upon reboot. I suspect this was not an internal infection. Could this be a DNS ddos? Any Ideas?
@RMerlin, @thelonelycoder

Last edited:

