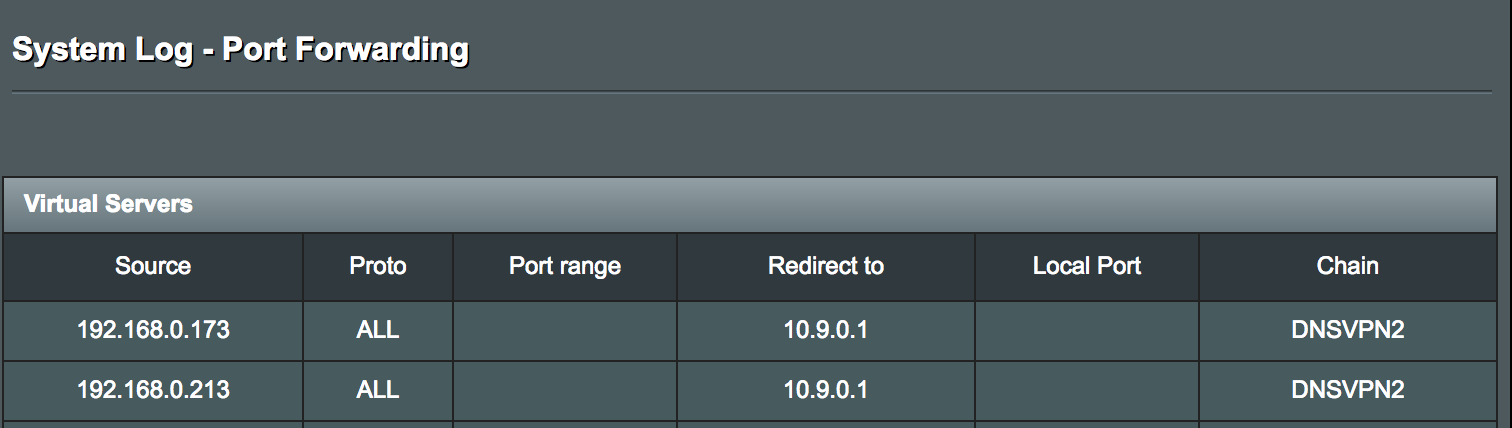
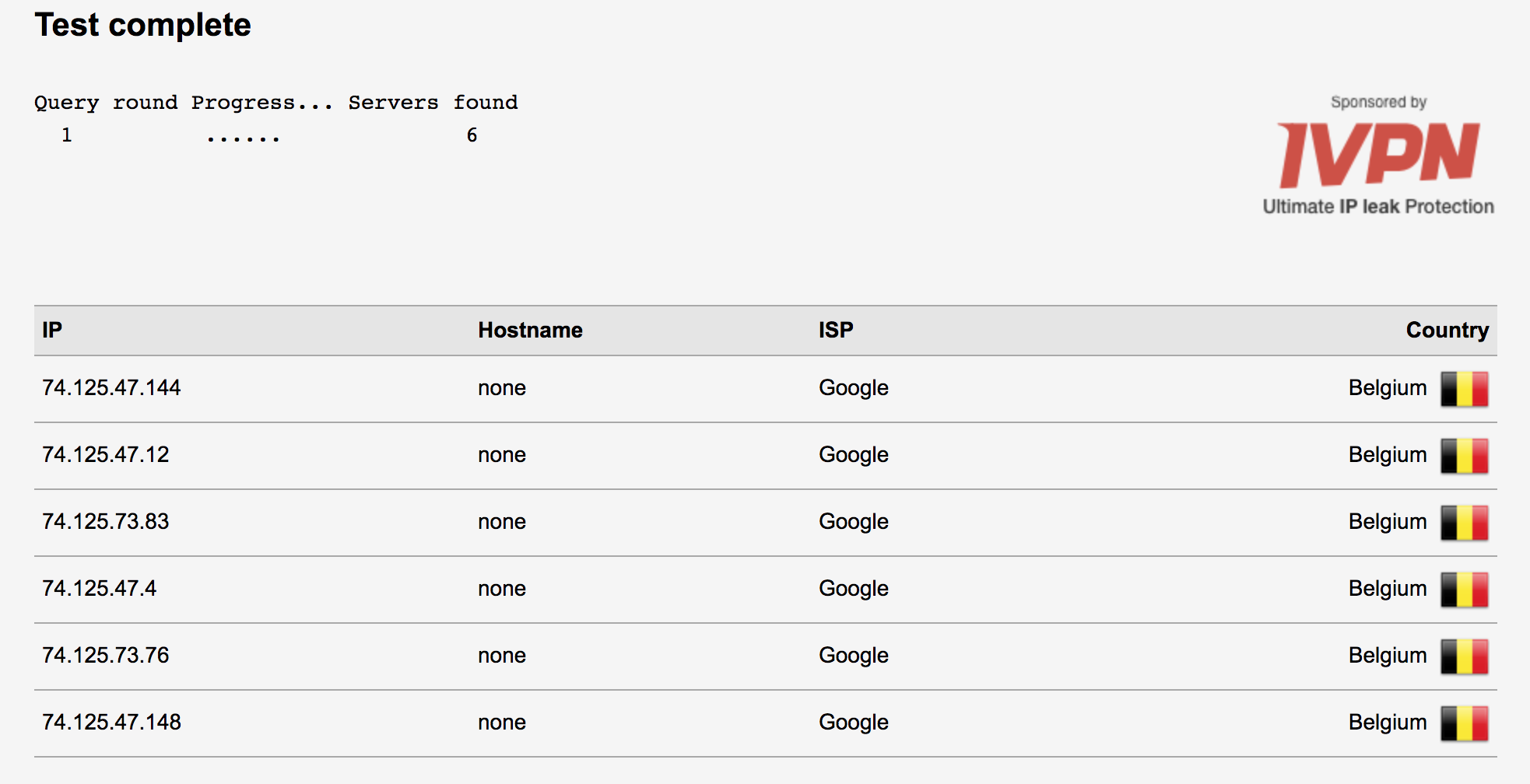
Quick questions, who is your vpn provider and do you pay for the service or is it free?
Service is provided by Private Tunnel, and yes I have paid for it. Interesting thing I noticed from log file below. Not sure if it's relevant but I like clean log files so assistance on this matter is appreciated.
Sep 23 09:34:57 openvpn[2479]: OpenVPN 2.4.3 arm-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Oct 4 2017
Sep 23 09:34:57 openvpn[2479]: library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.08
Sep 23 09:34:57 openvpn[2480]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sep 23 09:34:57 openvpn[2480]: Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sep 23 09:34:57 openvpn[2480]: Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sep 23 09:34:57 openvpn[2480]: TCP/UDP: Preserving recently used remote address: [AF_INET]50.7.148.122:1194
Sep 23 09:34:57 openvpn[2480]: Socket Buffers: R=[122880->122880] S=[122880->122880]
Sep 23 09:34:57 openvpn[2480]: NOTE: setsockopt TCP_NODELAY=1 failed
Sep 23 09:34:57 openvpn[2480]: UDP link local: (not bound)
Sep 23 09:34:57 openvpn[2480]: UDP link remote: [AF_INET]50.7.148.122:1194
Sep 23 09:34:57 openvpn[2480]: TLS: Initial packet from [AF_INET]50.7.148.122:1194, sid=db1e66d0 ad774826
Sep 23 09:34:57 openvpn[2480]: VERIFY OK: depth=2, CN=OpenVPN CA
Sep 23 09:34:57 openvpn[2480]: VERIFY OK: depth=1, CN=PT Transitional 20150615
Sep 23 09:34:57 openvpn[2480]: VERIFY KU OK
Sep 23 09:34:57 openvpn[2480]: Validating certificate extended key usage
Sep 23 09:34:57 openvpn[2480]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Sep 23 09:34:57 openvpn[2480]: VERIFY EKU OK
Sep 23 09:34:57 openvpn[2480]: VERIFY OK: depth=0, CN=par1.privatetunnel.com
Sep 23 09:34:57 openvpn[2480]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Sep 23 09:34:57 openvpn[2480]: [par1.privatetunnel.com] Peer Connection Initiated with [AF_INET]50.7.148.122:1194
Sep 23 09:34:59 openvpn[2480]: SENT CONTROL [par1.privatetunnel.com]: 'PUSH_REQUEST' (status=1)
Sep 23 09:34:59 openvpn[2480]: PUSH: Received control message: 'PUSH_REPLY,route-gateway 10.9.0.1,ifconfig 10.9.214.100 255.255.0.0,client-ip 94.9.197.34,ping 8,ping-restart 40,reneg-sec 3600,cipher AES-128-GCM,compress lz4-v2,peer-id 83546,topology subnet,explicit-exit-notify,redirect-gateway def1,dhcp-option DNS 10.9.0.1,sndbuf 0,rcvbuf 0,socket-flags TCP_NODELAY,block-ipv6'
Sep 23 09:34:59 openvpn[2480]: Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:3: client-ip (2.4.3)
Sep 23 09:34:59 openvpn[2480]: Options error: option 'reneg-sec' cannot be used in this context ([PUSH-OPTIONS])
Sep 23 09:34:59 openvpn[2480]: Option 'explicit-exit-notify' in [PUSH-OPTIONS]:11 is ignored by previous <connection> blocks
Sep 23 09:34:59 openvpn[2480]: Options error: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:17: block-ipv6 (2.4.3)
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: timers and/or timeouts modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: explicit notify parm(s) modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: compression parms modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: --sndbuf/--rcvbuf options modified
Sep 23 09:34:59 openvpn[2480]: Socket Buffers: R=[122880->122880] S=[122880->122880]
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: --socket-flags option modified
Sep 23 09:34:59 openvpn[2480]: NOTE: setsockopt TCP_NODELAY=1 failed
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: --ifconfig/up options modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: route options modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: route-related options modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: peer-id set
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: adjusting link_mtu to 1625
Sep 23 09:34:59 openvpn[2480]: OPTIONS IMPORT: data channel crypto options modified
Sep 23 09:34:59 openvpn[2480]: Data Channel: using negotiated cipher 'AES-128-GCM'
Sep 23 09:34:59 openvpn[2480]: Data Channel Encrypt: Cipher 'AES-128-GCM' initialized with 128 bit key
Sep 23 09:34:59 openvpn[2480]: Data Channel Decrypt: Cipher 'AES-128-GCM' initialized with 128 bit key
Sep 23 09:34:59 openvpn[2480]: TUN/TAP device tun12 opened
Sep 23 09:34:59 openvpn[2480]: TUN/TAP TX queue length set to 100
Sep 23 09:34:59 openvpn[2480]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Sep 23 09:34:59 openvpn[2480]: /usr/sbin/ip link set dev tun12 up mtu 1500
Sep 23 09:34:59 openvpn[2480]: /usr/sbin/ip addr add dev tun12 10.9.214.100/16 broadcast 10.9.255.255
Sep 23 09:34:59 openvpn[2480]: updown.sh tun12 1500 1553 10.9.214.100 255.255.0.0 init
Sep 23 09:34:59 openvpn-updown: Forcing 192.168.0.173 to use DNS server 10.9.0.1
Sep 23 09:35:00 openvpn[2480]: Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #8 / time = (1537695298) Sun Sep 23 09:34:58 2018 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Sep 23 09:35:00 openvpn[2480]: TLS Error: incoming packet authentication failed from [AF_INET]50.7.148.122:1194
Sep 23 09:35:02 openvpn[2480]: /usr/sbin/ip route add 50.7.148.122/32 via 94.9.196.1
Sep 23 09:35:02 openvpn[2480]: /usr/sbin/ip route add 0.0.0.0/1 via 10.9.0.1
Sep 23 09:35:02 openvpn[2480]: /usr/sbin/ip route add 128.0.0.0/1 via 10.9.0.1
Sep 23 09:35:02 openvpn-routing: Configuring policy rules for client 2
Sep 23 09:35:03 openvpn[2480]: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Sep 23 09:35:03 openvpn[2480]: Initialization Sequence Completed