Dear @
ExtremeFiretop,
Thanks for trying. I checked the code before deploying, I saw what was changed, but in my case it wasn't enough.
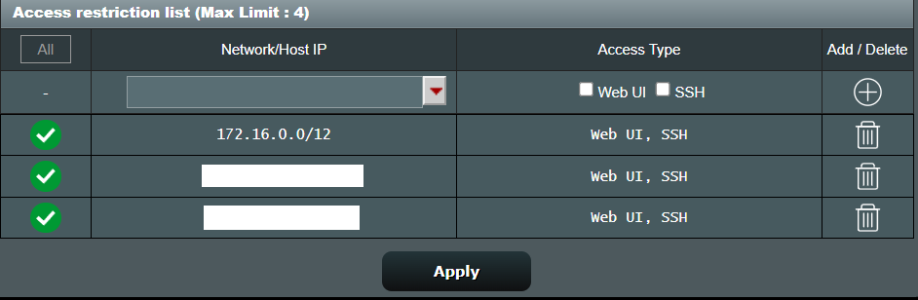
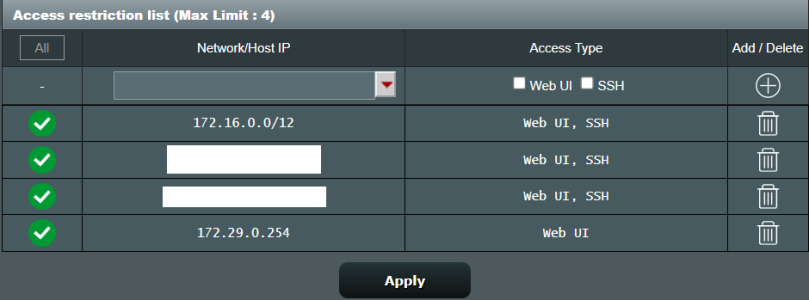
Unfortunatelly, this doesn't help with scenario (in my case): when one (can be overlapping?) concrete access exception CIDR range matches router IP range from mathematical (as seen from ASUS/Merlin firewall) POV, but from MerinAU script POV begins "lower" than (in principle <> 'not equal') router IP or subnet, to which this router IP belongs.
As far as I can interpret the code, and my extended grep knowledge is, validation code would finish at:
Bash:
cidrIPaddrEntry="$(echo "$restrictRuleList" | grep -oE "$lanIPaddrRegEx3")"
- with empty value, as only the last digit and mask suffix are allowed
valid digits from IP protocol possible ranges 0-255 & 0-32. But for validation code to be itself valid, it
mustn't use symbol/textual approach for isolated IP address octet. It must take mask and apply it to the network address, and to mathematically calculate in binary the start and the end of whole range. Then check if router's IP is within it.
I believe such a code snippet would be widely available if not in shell script, then other comparable PL/pseudo code.