Hi All.
I am running a RT-N66U on Asus stock fw version 3.0.0.4.382_50702
The router LAN is running on subnet: 192.168.10.0/24
The router's IP address is 192.168.10.1
I'd like to set up a openvpn server, where I can access the LAN remotely, e.g. a NAS on IP 192.168.10.4
I have already done this running tomato fw, but I switched now back to stock, so I do have some experience with openvpn setup.
What is working, is that I can connect to the openvpn server, and I can access the router at address 192.168.10.1, but nothing else can be seen on the lan.
For testing purposes I did try it my win10 PC, and also another RT-N66U, which is being used as an openvpn client, both resulted in failure.
The local subnet, from where I'd like to reach the server is 192.168.17.0/24
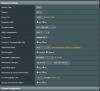
Here is a screenshot from my setup:

(Excuse the mismatch of the VPN subnet, the screenshot shows 10.9.0.0, because I experimented, what would happen if I change it.
It should show 10.8.0.0)
This is the generated config file via telnet:
This is the client config file:
This is the route table from the server after a connection was established:
This is the route table from the asus client after a connection was established:
I am thinking that some routing option might be still missing, so that the server does not really make it sure, that if a client wants to access 192.168.10.4 for example, that that has to go through the openvpn interface to the br0 where it can actually reach the destination.
But theoretically this line in the server config:
Should do the trick, as far I understood this howto correctly: https://openvpn.net/index.php/open-source/documentation/howto.html#scope
If someone could point me into the right direction, I would be really happy.
I am running a RT-N66U on Asus stock fw version 3.0.0.4.382_50702
The router LAN is running on subnet: 192.168.10.0/24
The router's IP address is 192.168.10.1
I'd like to set up a openvpn server, where I can access the LAN remotely, e.g. a NAS on IP 192.168.10.4
I have already done this running tomato fw, but I switched now back to stock, so I do have some experience with openvpn setup.
What is working, is that I can connect to the openvpn server, and I can access the router at address 192.168.10.1, but nothing else can be seen on the lan.
For testing purposes I did try it my win10 PC, and also another RT-N66U, which is being used as an openvpn client, both resulted in failure.
The local subnet, from where I'd like to reach the server is 192.168.17.0/24
Here is a screenshot from my setup:
(Excuse the mismatch of the VPN subnet, the screenshot shows 10.9.0.0, because I experimented, what would happen if I change it.
It should show 10.8.0.0)
This is the generated config file via telnet:
Code:
admin@RT-N66U:/tmp/etc/openvpn/server1# cat config.ovpn
# Automatically generated configuration
# Tunnel options
proto tcp-server
port 3153
dev tun21
sndbuf 0
rcvbuf 0
keepalive 15 60
daemon vpnserver1
verb 3
status-version 2
status status 10
comp-lzo adaptive
plugin /usr/lib/openvpn-plugin-auth-pam.so openvpn
# Server Mode
server 10.8.0.0 255.255.255.0
duplicate-cn
push "route 192.168.10.0 255.255.255.0 vpn_gateway 500"
push "dhcp-option DNS 192.168.10.1"
# Data Channel Encryption Options
auth SHA1
cipher AES-128-CBC
# TLS Mode Options
ca ca.crt
dh dh.pem
cert server.crt
key server.keyThis is the client config file:
Code:
admin@RT-N66U:/tmp/etc/openvpn/server1# cat client.ovpn
remote magic.asuscomm.com 3153
float
nobind
proto tcp-client
dev tun
sndbuf 0
rcvbuf 0
keepalive 15 60
comp-lzo adaptive
auth-user-pass
client
auth SHA1
cipher AES-128-CBC
ns-cert-type server
<ca>
-----BEGIN CERTIFICATE-----
removed
-----END CERTIFICATE-----
</ca>
<cert>
paste client certificate data here
</cert>
<key>
paste client key data here
</key>This is the route table from the server after a connection was established:
Code:
admin@RT-N66U:/tmp/etc/openvpn/server1# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.0.0.1 * 255.255.255.255 UH 0 0 0 ppp0
10.8.0.2 * 255.255.255.255 UH 0 0 0 tun21
10.8.0.0 10.8.0.2 255.255.255.0 UG 0 0 0 tun21
192.168.10.0 * 255.255.255.0 U 0 0 0 br0
169.254.0.0 * 255.255.0.0 U 0 0 0 eth0
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
default 10.0.0.1 0.0.0.0 UG 0 0 0 ppp0This is the route table from the asus client after a connection was established:
Code:
admin@RT-N66U:/tmp/home/root# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.8.0.5 * 255.255.255.255 UH 0 0 0 tun15
10.8.0.1 10.8.0.5 255.255.255.255 UGH 0 0 0 tun15
192.168.0.1 * 255.255.255.255 UH 0 0 0 eth0
192.168.17.0 * 255.255.255.0 U 0 0 0 br0
192.168.0.0 * 255.255.255.0 U 0 0 0 eth0
192.168.10.0 10.8.0.5 255.255.255.0 UG 500 0 0 tun15
127.0.0.0 * 255.0.0.0 U 0 0 0 lo
default compalhub.home 0.0.0.0 UG 0 0 0 eth0I am thinking that some routing option might be still missing, so that the server does not really make it sure, that if a client wants to access 192.168.10.4 for example, that that has to go through the openvpn interface to the br0 where it can actually reach the destination.
But theoretically this line in the server config:
Code:
push "route 192.168.10.0 255.255.255.0 vpn_gateway 500"If someone could point me into the right direction, I would be really happy.