You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Release Asuswrt-Merlin 3006.102.4 is now available
- Thread starter RMerlin
- Start date
- Status
- Not open for further replies.
Viktor Jaep
Part of the Furniture
Moving from 3004 to 3006 on the GT-AX6000, I noticed this curious thing... SSH is open on eth0, but thankfully not reachable from the public internet. It wasn't exhibiting this behavior on 3004. Just made my heart skip a beat.
Curious to see if others see the same thing doing an nmap on their public eth0 IP address?
In case someone asks to see these settings:

Code:
ViktorJp@GT-AX6000-3C88:/jffs/scripts# nmap 43.18.27.170
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 09:17 EDT
Nmap scan report for 43.18.27.170.some.isp.conglomerate.com (43.18.27.170)
Host is up (0.000032s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 0.32 secondsCurious to see if others see the same thing doing an nmap on their public eth0 IP address?
In case someone asks to see these settings:
Last edited:
maxbraketorque
Very Senior Member
Moving from 3004 to 3006 on the GT-AX6000, I noticed this curious thing... SSH is open on eth0, but thankfully not reachable from the public internet. It wasn't exhibiting this behavior on 3004. Just made my heart skip a beat.
Code:ViktorJp@GT-AX6000-3C88:/jffs/scripts# nmap 43.18.27.170 Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 09:17 EDT Nmap scan report for 43.18.27.170.some.isp.conglomerate.com (43.18.27.170) Host is up (0.000032s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh Nmap done: 1 IP address (1 host up) scanned in 0.32 seconds
Curious to see if others see the same thing doing an nmap on their public eth0 IP address?
In case someone asks to see these settings:
View attachment 66028
What would you see for 3004 with it set to "LAN only" or "LAN & WAN"? For 3004 set to "LAN only" is it open only on ports other than eth0? And for 3006 set to "LAN only", what's stopping it from being open to the internet? The built-in firewall?
dave14305
Part of the Furniture
Asus stopped binding ssh to the LAN IP in 3006 and 3004.388.9 GPLs (I assume it was Asus for GNP reasons).Moving from 3004 to 3006 on the GT-AX6000, I noticed this curious thing... SSH is open on eth0, but thankfully not reachable from the public internet. It wasn't exhibiting this behavior on 3004.
This line was commented out in the latest Merlin releases.
asuswrt-merlin.ng/release/src/router/rc/ssh.c at 0c35adea7e346e27c9921cf0ae54c87460a625be · RMerl/asuswrt-merlin.ng
Third party firmware for Asus routers (newer codebase) - RMerl/asuswrt-merlin.ng
Last edited:
Viktor Jaep
Part of the Furniture
Previously on 3004, "LAN only" would only show an ssh/open entry under the LAN side... nothing on the WAN side. You can also check by runningWhat would you see for 3004 with it set to "LAN only" or "LAN & WAN"? For 3004 set to "LAN only" is it open only on ports other than eth0? And for 3006 set to "LAN only", what's stopping it from being open to the internet? The built-in firewall?
nmap 192.168.50.1 (or whatever your local LAN IP is). Yeah, I'm guessing the firewall is blocking it at this point. Thank goodness. I immediately jumped to a breached or incorrectly configured router conclusion before testing it from the internet.Thanks for pointing us to the code, @dave14305!Asus stopped binding ssh to the LAN IP in 3006 and 3004.388.9 GPLs (I assume it was Asus for GNP reasons). But the SSH LAN/WAN setting has only influenced the firewall rules, not how the daemon runs.
dave14305
Part of the Furniture
That’s OK, I described the previous behavior incorrectly anyway. The LAN/WAN setting would also influence the IP binding in the older versions.Thanks for pointing us to the code, @dave14305!
CaptainSTX
Part of the Furniture
Here is what I get: It reports all scanned ports in ignored states. For SSH I use a non standard port in the range greater than 50,000.Moving from 3004 to 3006 on the GT-AX6000, I noticed this curious thing... SSH is open on eth0, but thankfully not reachable from the public internet. It wasn't exhibiting this behavior on 3004. Just made my heart skip a beat.
Code:ViktorJp@GT-AX6000-3C88:/jffs/scripts# nmap 43.18.27.170 Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 09:17 EDT Nmap scan report for 43.18.27.170.some.isp.conglomerate.com (43.18.27.170) Host is up (0.000032s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh Nmap done: 1 IP address (1 host up) scanned in 0.32 seconds
Curious to see if others see the same thing doing an nmap on their public eth0 IP address?
In case someone asks to see these settings:
View attachment 66028
ASUSWRT-Merlin RT-AX88U_PRO 3006.102.4_0 Sat May 10 15:59:43 UTC 2025
TheMan@RT-AX88U_Pro-68D0:/tmp/home/root# nmap 73.62.xxx.xx
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 12:15 EDT
Nmap scan report for c-73-62-xxx-xx.hsd1.fl.comcast.net (73.62.xxx.xx)
Host is up (0.000035s latency).
All 1000 scanned ports on c-73-62-xxx.xx.hsd1.fl.comcast.net (73.62.xxx.xx) arin ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
TheMan@RT-AX88U_Pro-68D0:/tmp/home/root#
Viktor Jaep
Part of the Furniture
Hum. How to explain that. Assuming you have the same setup as mine for SSH right?Here is what I get: It reports all scanned ports in ignored states. For SSH I use a non standard port in the range greater than 50,000.
ASUSWRT-Merlin RT-AX88U_PRO 3006.102.4_0 Sat May 10 15:59:43 UTC 2025
TheMan@RT-AX88U_Pro-68D0:/tmp/home/root# nmap 73.62.xxx.xx
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-31 12:15 EDT
Nmap scan report for c-73-62-xxx-xx.hsd1.fl.comcast.net (73.62.xxx.xx)
Host is up (0.000035s latency).
All 1000 scanned ports on c-73-62-xxx.xx.hsd1.fl.comcast.net (73.62.xxx.xx) arin ignored states.
Not shown: 1000 closed tcp ports (reset)
Nmap done: 1 IP address (1 host up) scanned in 0.37 seconds
TheMan@RT-AX88U_Pro-68D0:/tmp/home/root#
dave14305
Part of the Furniture
He said his SSH port was above 50000. The default nmap scan wouldn’t check that high.Hum. How to explain that.
CaptainSTX
Part of the Furniture
Exact same settings except as I said originally I use a port other than 22 and greater than 50,000. Could be in my case since this command only scans 1000 ports the port I use is above the range scanned. Not that it should make any difference I have disabled idle timeout.Hum. How to explain that. Assuming you have the same setup as mine for SSH right?
View attachment 66031
Weblee2407
Senior Member
Well…this update gave me a lot of procedure problems I thought were behind me because of my "experience". I had problems resetting back to 004.388.8_4 too. I have NEVER had the hard reset fail to clear settings. Not only that, but I had to back out of the update because of the nuances of the guest network/IOT network. Maybe I can get my lab router back from my daughter (lol) and test, but as is, there was too much "interference" (for lack of a better word) in the video from the security cameras for the wifey. She has learned how to use the cameras for her "neighborhood watch (lol) activities. Also, I could not install SCRIBE because Entware was out of rev - that's a pretty old issue and I can't understand why it is suddenly back.
Updated my GT-AX11000 Pro from 3004.388.8_4 to 3006.104.2_0 and noticed that the Asus Device Discovery utility no longer finds the router. It has no problem finding the 2 XT8 Ver. 2 (latest stock firmware) AIMesh nodes in my my system. Before the firmware update Device Discovery found the router and both nodes with no problem. Anyone else notice this or know why it's happening?
Viktor Jaep
Part of the Furniture
Yeah, would be nice if it showed everything.Exact same settings except as I said originally I use a port other than 22 and greater than 50,000. Could be in my case since this command only scans 1000 ports the port I use is above the range scanned. Not that it should make any difference I have disabled idle timeout.
Mesh Nodes - Range Extenders
I'm running a BE96U with Merlin 3006.102.4 final. I recently tried to link a new RP-BE58 Wifi 7 extender and could only get it to link up with my main router using the wired option. Then, selecting 5G preferred link in the node management menu, restarting without wire, the node would not link up. I tried to go back to 102.4_Beta3 and was able to link with wire, then move away and link via wireless, but it was very iffy. I did not try Asus 3006.102 release because I didn't want to go through the hassle of wipe and manual reinstall.
For kicks, I pulled out a RP-AX58 Wifi 6 extender and it readily linked with the BE96U wirelessly on Merlin 3006.102.4 final. I'll try this exercise again once the BE58 has a firmware update. I'm guessing there's a firmware catch up needed for the BE58.
I'm running a BE96U with Merlin 3006.102.4 final. I recently tried to link a new RP-BE58 Wifi 7 extender and could only get it to link up with my main router using the wired option. Then, selecting 5G preferred link in the node management menu, restarting without wire, the node would not link up. I tried to go back to 102.4_Beta3 and was able to link with wire, then move away and link via wireless, but it was very iffy. I did not try Asus 3006.102 release because I didn't want to go through the hassle of wipe and manual reinstall.
For kicks, I pulled out a RP-AX58 Wifi 6 extender and it readily linked with the BE96U wirelessly on Merlin 3006.102.4 final. I'll try this exercise again once the BE58 has a firmware update. I'm guessing there's a firmware catch up needed for the BE58.
MDM
Very Senior Member
For me the same test is Passed.RT-AX-86U Pro 3006.102.4
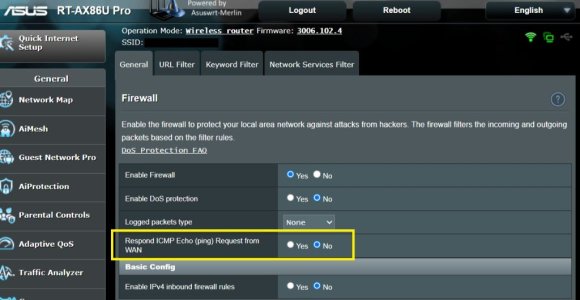
The ShieldsUP scan of Common Ports says FAILED because a a Ping (IMCP Echo) reply was received. The Firewall setting, Respond IMCP Echo (ping) Request from WAN, is NO. Any issue with this behavior?
Even the All service ports option, and any other test....
Not seeing the same on a RT-AX86U Pro. All common ports report stealth. Respond ICMP Echo (ping) Request from WAN is set to No.RT-AX-86U Pro 3006.102.4
The ShieldsUP scan of Common Ports says FAILED because a a Ping (IMCP Echo) reply was received. The Firewall setting, Respond IMCP Echo (ping) Request from WAN, is NO. Any issue with this behavior?
Code:
GRC Port Authority Report created on UTC: 2025-06-01 at 22:xx:xx
Results from scan of ports: 0, 21-23, 25, 79, 80, 110, 113,
119, 135, 139, 143, 389, 443, 445,
1002, 1024-1030, 1720, 5000
0 Ports Open
0 Ports Closed
26 Ports Stealth
---------------------
26 Ports Tested
ALL PORTS tested were found to be: STEALTH.
TruStealth: PASSED - ALL tested ports were STEALTH,
- NO unsolicited packets were received,
- NO Ping reply (ICMP Echo) was received.Edit to add: Are you running any addon scripts or have made any changes to the router or it's firewall (etables or IPtables) rules? Or is the upstream ISP provided hardware the router is connected to maybe responding somehow to the GRC test? Maybe the router log will show something?
Attachments
Last edited:
Treadler
Very Senior Member
No issue seen here, passes with flying colours.RT-AX-86U Pro 3006.102.4
The ShieldsUP scan of Common Ports says FAILED because a a Ping (IMCP Echo) reply was received. The Firewall setting, Respond IMCP Echo (ping) Request from WAN, is NO. Any issue with this behavior?
(Using “all service ports” selection.)
Are you perchance testing through a VPN?RT-AX-86U Pro 3006.102.4
The ShieldsUP scan of Common Ports says FAILED because a a Ping (IMCP Echo) reply was received. The Firewall setting, Respond IMCP Echo (ping) Request from WAN, is NO. Any issue with this behavior?
I ran ShieldsUp through my VPN (wireguard, running on the router) and it detected the VPN endpoint IP, not my actual IP, and gave passing grade on all service ports, but also indicated PING fail due to response. My Firewall settings are set to Not Respond.
- Status
- Not open for further replies.
Similar threads
- Replies
- 324
- Views
- 48K
- Replies
- 702
- Views
- 90K
- Replies
- 268
- Views
- 46K
- Replies
- 67
- Views
- 14K
- Replies
- 71
- Views
- 13K
Similar threads
Similar threads
-
-
-
Does minidlna get installed by default (asuswrt-merlin 3006.102.5)
- Started by chrisisbd
- Replies: 2
-
-
-
-
Homekit help request on Asuswrt-Merlin 3006.102.4 Beta 2
- Started by Alfie J
- Replies: 2
-
-
-
Asuswrt-Merlin 3004.288.8_4 /jffs Partition Nuked on Random Reboot
- Started by garycnew
- Replies: 6
Latest threads
-
-
-
Release ASUS ZenWiFi BT8 Firmware version 3.0.0.6.102_58394 (2026/02/04)
- Started by fruitcornbread
- Replies: 0
-
Does Unifi ever update their OpenVPN server software?
- Started by HarryH3
- Replies: 12
-
Support SNBForums w/ Amazon
If you'd like to support SNBForums, just use this link and buy anything on Amazon. Thanks!
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!
Members online
Total: 5,118 (members: 14, guests: 5,104)