Stoonhea020
Occasional Visitor
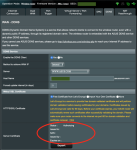
I have the same problem that two others reported as well. Since the upgrade from alpha4 to beta1 I am no longer able to retrieve a LE free certificate. It hangs in an Authorization status, even after a couple of reboots.
I also factory reset my router (RT-AX86U) several times via the UI and formatted jffs partition but no success. As test I disabled the Firewall and enabled WAN access but the status remain the same.
Dec 6 11:35:03 Mastiff: Got AAE_SIG_REMOTE_CONNECTION_TURNED_ON
Dec 6 11:35:03 rc_service: httpd 5672:notify_rc restart_ddns_le
Dec 6 11:35:03 start_ddns: update WWW.ASUS.COM [email protected], wan_unit 0
Dec 6 11:35:03 inadyn[11420]: In-a-dyn version 2.7 -- Dynamic DNS update client.
Dec 6 11:35:03 inadyn[11420]: Update forced for alias ***********.asuscomm.com, new IP# XXX.XXX.XXX.XXX
Dec 6 11:35:04 inadyn[11420]: Updating cache for ***********.asuscomm.com
Dec 6 11:35:10 kernel: [Sun Dec 6 11:35:10 MEZ 2020]
Dec 6 11:35:10 kernel: Registering account
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: Already registered
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: ACCOUNT_THUMBPRINT='***************************************'
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: Creating domain key
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: The domain key is here: /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.key
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: Single domain='***********.asuscomm.com'
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: Getting domain auth token for each domain
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Getting webroot for domain='***********.asuscomm.com'
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: ***********.asuscomm.com is already verified, skip dns-01.
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Verify finished, start to sign.
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/**************/*****************
Dec 6 11:35:20 kernel: [Sun Dec 6 11:35:20 MEZ 2020]
Dec 6 11:35:20 kernel: Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/*****************************************
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Cert success.
Dec 6 11:35:22 kernel: cat: write error: Invalid argument
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Your cert is in /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Your cert key is in /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.key
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: The intermediate CA cert is in /jffs/.le/***********.asuscomm.com/ca.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: And the full chain certs is there: /jffs/.le/***********.asuscomm.com/fullchain.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Installing key to:/jffs/.le/***********.asuscomm.com/domain.key
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Installing full chain to:/jffs/.le/***********.asuscomm.com/fullchain.pem
Dec 6 11:36:00 rc_service: service 14384:notify_rc restart_letsencrypt
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Domains not changed.
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Skip, Next renewal time is: Thu Feb 4 10:35:22 UTC 2021
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Add '--force' to force to renew.
I also factory reset my router (RT-AX86U) several times via the UI and formatted jffs partition but no success. As test I disabled the Firewall and enabled WAN access but the status remain the same.
Dec 6 11:35:03 Mastiff: Got AAE_SIG_REMOTE_CONNECTION_TURNED_ON
Dec 6 11:35:03 rc_service: httpd 5672:notify_rc restart_ddns_le
Dec 6 11:35:03 start_ddns: update WWW.ASUS.COM [email protected], wan_unit 0
Dec 6 11:35:03 inadyn[11420]: In-a-dyn version 2.7 -- Dynamic DNS update client.
Dec 6 11:35:03 inadyn[11420]: Update forced for alias ***********.asuscomm.com, new IP# XXX.XXX.XXX.XXX
Dec 6 11:35:04 inadyn[11420]: Updating cache for ***********.asuscomm.com
Dec 6 11:35:10 kernel: [Sun Dec 6 11:35:10 MEZ 2020]
Dec 6 11:35:10 kernel: Registering account
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: Already registered
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: ACCOUNT_THUMBPRINT='***************************************'
Dec 6 11:35:12 kernel: [Sun Dec 6 11:35:12 MEZ 2020]
Dec 6 11:35:12 kernel: Creating domain key
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: The domain key is here: /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.key
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: Single domain='***********.asuscomm.com'
Dec 6 11:35:16 kernel: [Sun Dec 6 11:35:16 MEZ 2020]
Dec 6 11:35:16 kernel: Getting domain auth token for each domain
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Getting webroot for domain='***********.asuscomm.com'
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: ***********.asuscomm.com is already verified, skip dns-01.
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Verify finished, start to sign.
Dec 6 11:35:19 kernel: [Sun Dec 6 11:35:19 MEZ 2020]
Dec 6 11:35:19 kernel: Lets finalize the order, Le_OrderFinalize: https://acme-v02.api.letsencrypt.org/acme/finalize/**************/*****************
Dec 6 11:35:20 kernel: [Sun Dec 6 11:35:20 MEZ 2020]
Dec 6 11:35:20 kernel: Download cert, Le_LinkCert: https://acme-v02.api.letsencrypt.org/acme/cert/*****************************************
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Cert success.
Dec 6 11:35:22 kernel: cat: write error: Invalid argument
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Your cert is in /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Your cert key is in /jffs/.le/***********.asuscomm.com/***********.asuscomm.com.key
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: The intermediate CA cert is in /jffs/.le/***********.asuscomm.com/ca.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: And the full chain certs is there: /jffs/.le/***********.asuscomm.com/fullchain.cer
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Installing key to:/jffs/.le/***********.asuscomm.com/domain.key
Dec 6 11:35:22 kernel: [Sun Dec 6 11:35:22 MEZ 2020]
Dec 6 11:35:22 kernel: Installing full chain to:/jffs/.le/***********.asuscomm.com/fullchain.pem
Dec 6 11:36:00 rc_service: service 14384:notify_rc restart_letsencrypt
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Domains not changed.
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Skip, Next renewal time is: Thu Feb 4 10:35:22 UTC 2021
Dec 6 11:36:01 kernel: [Sun Dec 6 11:36:01 MEZ 2020]
Dec 6 11:36:01 kernel: Add '--force' to force to renew.