With the current exploit (CVSS 9.8 pre-auth RCE bug) in full swing , I would like to block port 445 towards the internet as many recommend .
I would like to doublecheck if I am doing the right thing here :
Enable filter , deny list
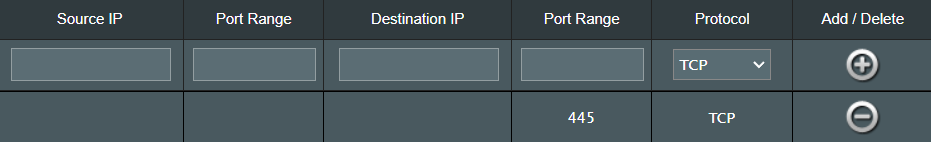
And then in which field(s) do I exactly enter port 445 ? The first port range or the second , or both ?
Protocol is TCP .
So what I have now is 2 rules , 1 with 445 in first port range column and 1 with 445 in the second port range column .
In source and destination IP , nothing needs to be filled in as far as I know , right ?
I would like to doublecheck if I am doing the right thing here :
Firewall - Network services filterEnable filter , deny list
And then in which field(s) do I exactly enter port 445 ? The first port range or the second , or both ?
| Source IP | Port Range | Destination IP | Port Range | Protocol | Add / Delete |
|---|
Protocol is TCP .
So what I have now is 2 rules , 1 with 445 in first port range column and 1 with 445 in the second port range column .
In source and destination IP , nothing needs to be filled in as far as I know , right ?