You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
IP Wan invalid for HTTPS certificate
- Thread starter Cometti
- Start date
-
- Tags
- certificate error ddns https
Jack Yaz
Part of the Furniture
You left the domain un-redacted in the certificate screenshot btw
Thx!! Can you remove your quote please?
RMerlin
Asuswrt-Merlin dev
Since most users have a dynamic WAN IP, the IP isn't used in the certificate, only the DDNS hostname. If you want to access through the WAN, use the DDNS hostname instead. Otherwise, a new certificate would have to be created every time your WAN IP changed (which might be daily for some users).
Since most users have a dynamic WAN IP, the IP isn't used in the certificate, only the DDNS hostname. If you want to access through the WAN, use the DDNS hostname instead. Otherwise, a new certificate would have to be created every time your WAN IP changed (which might be daily for some users).
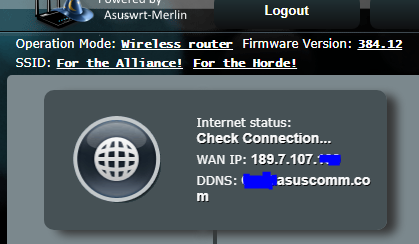
Thanks for the answer, but it's not me who chooses what will be generated in the certificate, it was the system itself that defined that IP
How do I change the creation of the certificate to not be issued to the IP?
RMerlin
Asuswrt-Merlin dev
Thanks for the answer, but it's not me who chooses what will be generated in the certificate, it was the system itself that defined that IP
How do I change the creation of the certificate to not be issued to the IP?
View attachment 18669
That's just the CN. Modern browsers mostly look at the content of the SAN field now, in the Extended x509 attributes:
That's where your DDNS hostname (the *.asuscomm.com one) is being added, so it will be considered as valid for the DDNS hostname.
RMerlin
Asuswrt-Merlin dev
Any suggestion to fix?!
It's invalid because it's self-signed, as the error message indicates. This is perfectly normal. The only way to get rid of the error message is to manage your own CA. You could go with Let's Encrypt, but it's very unreliable on a router because of the large number of users within the asuscomm.com domain, causing renewals to randomly fail/be throttled.
Just ignore it. It's perfectly secure, your browser is simply telling you it doesn't recognize who emitted that certificate.
It's invalid because it's self-signed, as the error message indicates. This is perfectly normal. The only way to get rid of the error message is to manage your own CA. You could go with Let's Encrypt, but it's very unreliable on a router because of the large number of users within the asuscomm.com domain, causing renewals to randomly fail/be throttled.
Just ignore it. It's perfectly secure, your browser is simply telling you it doesn't recognize who emitted that certificate.
Alright... Thx for the explanation!
XIII
Very Senior Member
I still like the idea of using Let's Encrypt.It's invalid because it's self-signed, as the error message indicates. This is perfectly normal. The only way to get rid of the error message is to manage your own CA. You could go with Let's Encrypt, but it's very unreliable on a router because of the large number of users within the asuscomm.com domain, causing renewals to randomly fail/be throttled.
What if one owns a domain and redirects router.domain.com to hostname.asuscomm.com, would that prevent throttling?
However, one still needs to enable web access from WAN to let either of those URLs actually open the router page? (So a No-Go?!)
Makaveli
Very Senior Member
You could go with Let's Encrypt, but it's very unreliable on a router because of the large number of users within the asuscomm.com domain, causing renewals to randomly fail/be throttled.
This is why I prefer to let Pixelserv generate the Cert.
RMerlin
Asuswrt-Merlin dev
What if one owns a domain and redirects router.domain.com to hostname.asuscomm.com, would that prevent throttling?
As long the acme client requests for your own domain, you'd be fine. You could then create a CNAME within your domain that will point to the asuscomm DDNS entry - that is how I have things setup myself (but with a different DDNS provider than Asus).
That will require you to configure things manually tho, as the router client would request using the DDNS domain.
RMerlin
Asuswrt-Merlin dev
This is why I prefer to let Pixelserv generate the Cert.
I use XCA to manage my own CA, that way I can have recognized certificates on every single device I have (including the 6-7 routers I routinely use for development purposes).
Jack Yaz
Part of the Furniture
I use Cloudflare's free DNS for my own domain (purchased), and use DDNS from the router to dns-o-matic to update the A record for it. Works quite nicely for my needs!As long the acme client requests for your own domain, you'd be fine. You could then create a CNAME within your domain that will point to the asuscomm DDNS entry - that is how I have things setup myself (but with a different DDNS provider than Asus).
That will require you to configure things manually tho, as the router client would request using the DDNS domain.
XIII
Very Senior Member
But what about this part?
Reason for asking: when I type https://hostname.asuscomm.com:8443 in my browser the web GUI does not open (https://192.168.1.1:8443 does), unless I enable remote web access from WAN (which I would like to prevent); even on my local network.
(I'm OK-ish with manually updating the certificate every 90 days, or finding a way to automate that)
However, one still needs to enable web access from WAN to let either of those URLs actually open the router page?
Reason for asking: when I type https://hostname.asuscomm.com:8443 in my browser the web GUI does not open (https://192.168.1.1:8443 does), unless I enable remote web access from WAN (which I would like to prevent); even on my local network.
(I'm OK-ish with manually updating the certificate every 90 days, or finding a way to automate that)
XIII
Very Senior Member
I don't think I need that (when "manually" getting the Let's Encrypt certificates)?I don't know the details of Asus's implementation for validation, libletsencrypt is closed source.
- A CNAME record in the DNS settings of my domain is set to redirect router.domain.com to hostname.asuscomm.com
- External traffic on port 80 of the router is forwarded to a Raspberry Pi (for certbot)
- On this Pi I run certbot ("standalone") to generate a certificate and key for router.domain.com
- I upload the generated certificate and key on the admin page of the router
However, I thought it was strongly discouraged to enable web access from WAN due to security concerns?
Do you guys really enable this, or do you use another way to get this to work? If so, how?
Jack Yaz
Part of the Furniture
I run LetsEncrypt in a Docker container and use DNS verification via the cloudflare plugin: https://hub.docker.com/r/linuxserver/letsencrypt/I don't think I need that (when "manually" getting the Let's Encrypt certificates)?
When I enable web access from WAN this setup actually works: a green lock when I surf to https://router.domain.com:8443; a secure connection verified by Let's Encrypt.
- A CNAME record in the DNS settings of my domain is set to redirect router.domain.com to hostname.asuscomm.com
- External traffic on port 80 of the router is forwarded to a Raspberry Pi (for certbot)
- On this Pi I run certbot ("standalone") to generate a certificate and key for router.domain.com
- I upload the generated certificate and key on the admin page of the router
However, I thought it was strongly discouraged to enable web access from WAN due to security concerns?
Do you guys really enable this, or do you use another way to get this to work? If so, how?
Similar threads
- Replies
- 7
- Views
- 608
- Replies
- 3
- Views
- 374
Similar threads
Similar threads
-
DDNS, AX86U-PRO, inadyn isn't called after wan IP change ?
- Started by JackJack
- Replies: 3
-
Assigned IP address to the WAN interface via VPN director: no internet connection - why?
- Started by OB1
- Replies: 1
-
Solved GT-AX11000 drops WAN connection / crashes every 6-36 hours
- Started by zombeeh8er
- Replies: 25
-
-
-
WAN IP and hostname verification not respecting interval
- Started by Deetlemore
- Replies: 2
-
IPv6 and Router Advertisement adding route to delegated /56 via WAN interface
- Started by MrC99
- Replies: 0
-
Would any of this make my browsing more secure? (WAN DNS settings)
- Started by Rob Q
- Replies: 20
-
Using Dual-WAN failover but using the passive with a rule
- Started by GShlomi
- Replies: 0
-
Latest threads
-
Use the VPN base on URL rather than IP address
- Started by Armandooooo
- Replies: 0
-
RT-AX88U Pro and RT-AX86U Pro vs Dual GT-AXE11000 Setup
- Started by Mxlt
- Replies: 2
-
-
-
Hyperotpic router replacement - will it solve my problem with connection dropping!
- Started by ACME NoLiFe
- Replies: 2
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!