margentieri
Occasional Visitor
Hello all. So I just recently finished setting up both OpenVPN servers on my ac68u. The first is set up so that connected clients have access to my LAN (Push LAN to clients:Yes), and the second is set up so that connected clients do NOT have access to my LAN (Push LAN to clients: No).
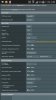
Unfortunately, it appears that clients connected to the second server, where "Push LAN to clients" is set to No, can STILL access my LAN. I have attached a screenshot showing my current settings for this server (and in case it matters, my first server's settings are identical, aside from port number and the above mentioned LAN option).
Am i simply misunderstanding the meaning of this option? Is there something else I have to do to prevent access to my LAN? Or is this a bug?
Thanks!
Unfortunately, it appears that clients connected to the second server, where "Push LAN to clients" is set to No, can STILL access my LAN. I have attached a screenshot showing my current settings for this server (and in case it matters, my first server's settings are identical, aside from port number and the above mentioned LAN option).
Am i simply misunderstanding the meaning of this option? Is there something else I have to do to prevent access to my LAN? Or is this a bug?
Thanks!