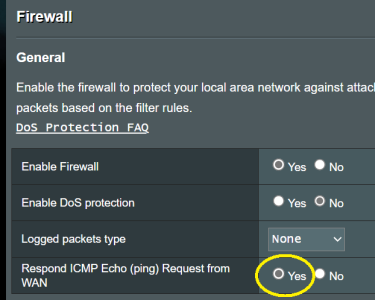
I enabled firewall and for outside i can't do traceroute if i disable firewall is back to resolve.
For what i search ICMP need to allow and respond ping but even enabled Respond ICMP Echo still i can't resolve traceroute issue.
- How i can enable traceroute with firewall enabled.
- How i can enable traceroute with/without Respond ICMP Echo enabled.
For what i search ICMP need to allow and respond ping but even enabled Respond ICMP Echo still i can't resolve traceroute issue.
- How i can enable traceroute with firewall enabled.
- How i can enable traceroute with/without Respond ICMP Echo enabled.