orudie
Occasional Visitor
Stock Firmware Version:3.0.0.4.386_46061
Hello. on my RT-AX86U port forwarding does not work. I believe it started happening after recently enabling AiMesh.
The AiMesh node is ASUS RT-AC68U connected to ASUS RT-AX86U using LAN ethernet. AiProtection is disabled.
The main router RT-AX86U WAN port is connected to LAN 1 port of my ISP's modem/router which is configured in bridge mode.
RT-AX86U WAN configured with WAN type PPPoE and connected to ISP with username and password.
LAN configured with router's IP Address 10.1.1.1 and Subnet Mask 255.255.255.0
DDNS is enabled and configured with asuscomm.com and free SSL cert from letsencrypt.org.
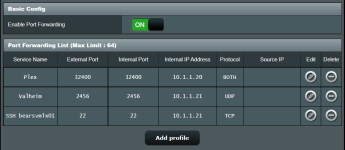
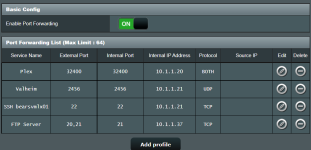
Attaching a screenshot with port forwarding rules and none of them are working.
Please suggest what I am doing incorrectly and which configuration I should check.
Hello. on my RT-AX86U port forwarding does not work. I believe it started happening after recently enabling AiMesh.
The AiMesh node is ASUS RT-AC68U connected to ASUS RT-AX86U using LAN ethernet. AiProtection is disabled.
The main router RT-AX86U WAN port is connected to LAN 1 port of my ISP's modem/router which is configured in bridge mode.
RT-AX86U WAN configured with WAN type PPPoE and connected to ISP with username and password.
LAN configured with router's IP Address 10.1.1.1 and Subnet Mask 255.255.255.0
DDNS is enabled and configured with asuscomm.com and free SSL cert from letsencrypt.org.
Attaching a screenshot with port forwarding rules and none of them are working.
Please suggest what I am doing incorrectly and which configuration I should check.
Attachments
Last edited: