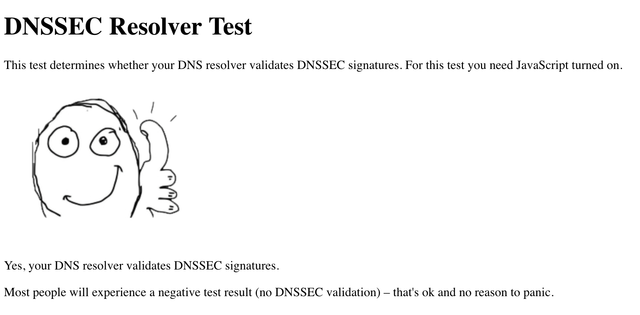
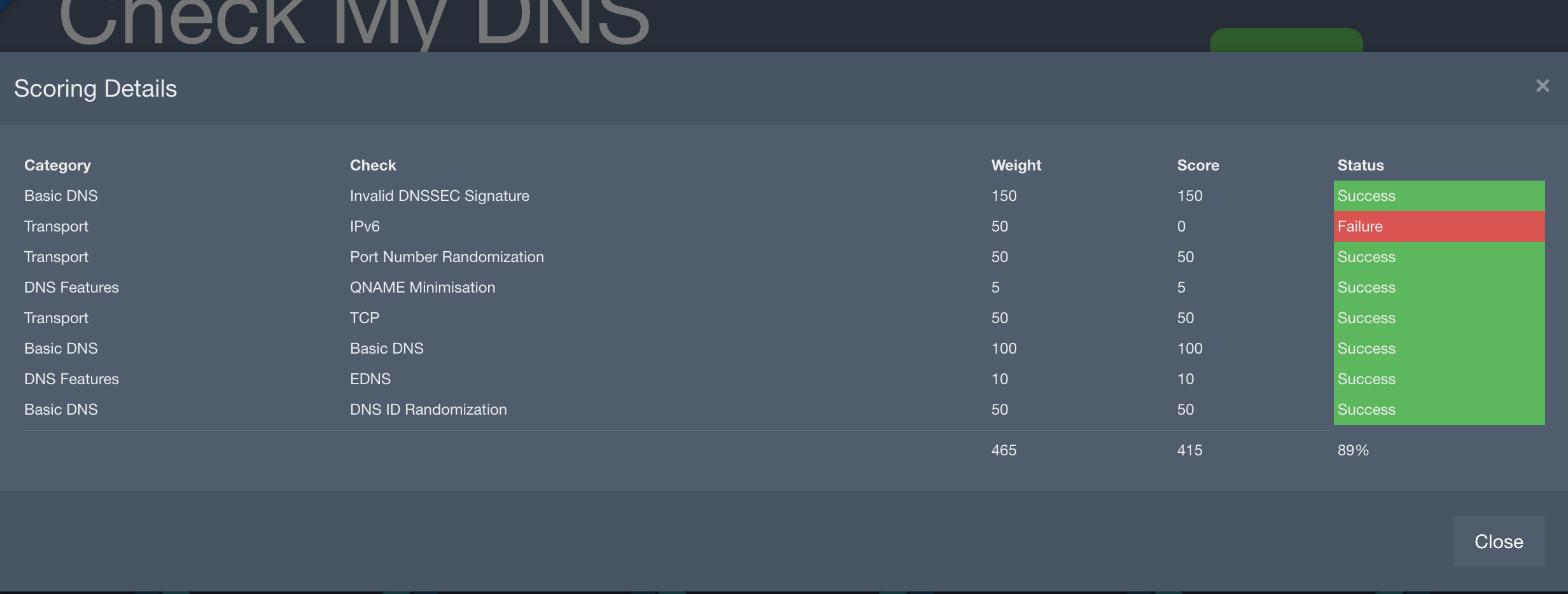
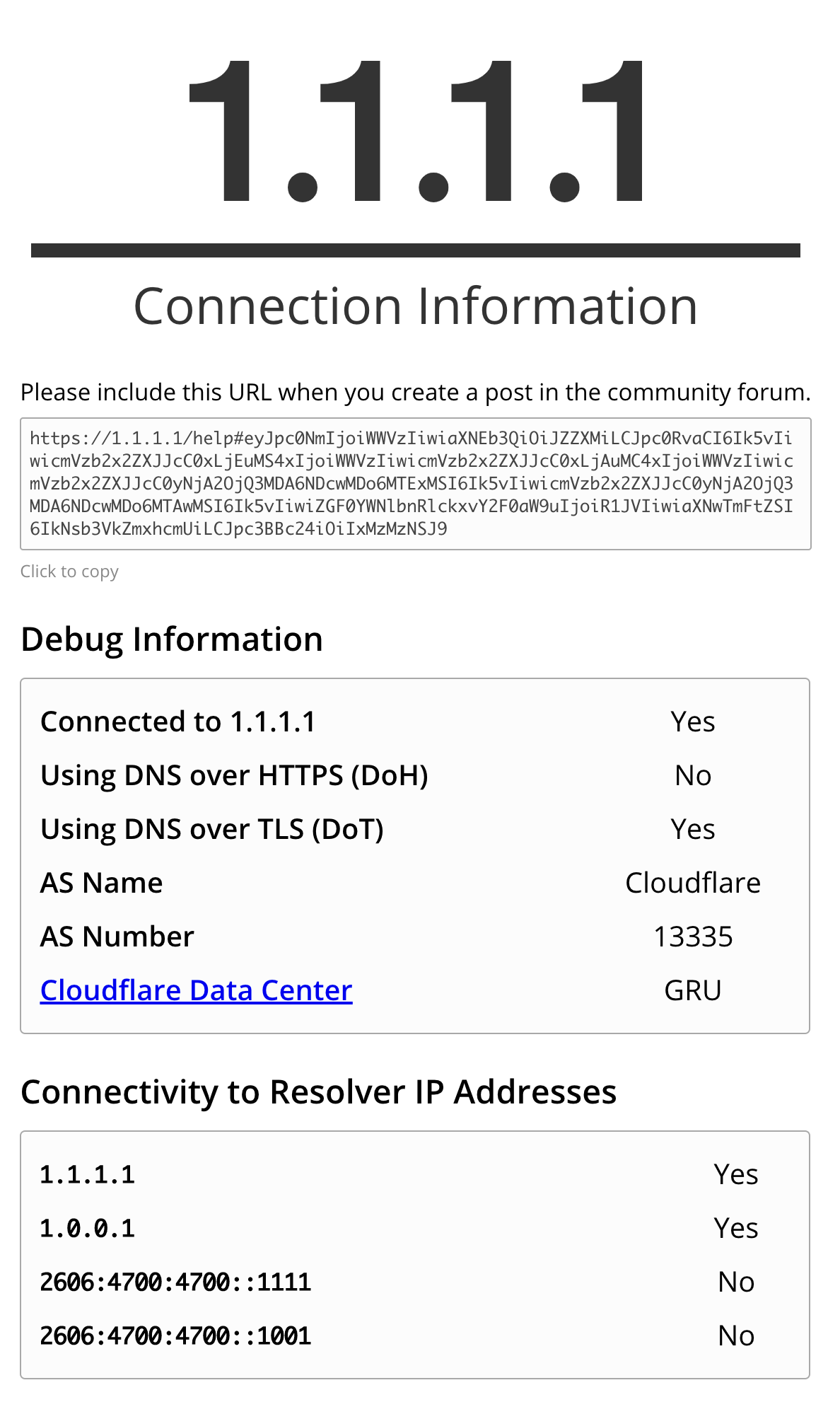
To make it clear to some people concerning EDNS (Geolocation=bad location routing) there is a "possible" way of impact.
But well , to come back to @Merlin Netflix, Youtube or streaming is a whole other story and off road.
why ? they also using bad routing blocking vpn and so on........ this for security and marketing.
To be total Off-road asus using vpn configuration for there routers that make it total useless.
Also implemented even what the cause, well all the fancy tools we also don't need it but some people like it.
To make my point it's all about decisions.
For people out there before choosing it there are tons of tools to test it even EDNS you can check.
For me it's a easy decision the data-center is 10 miles away from where I'm living so fast DNS responses.
Lot more secure and had no bad routing to be clear. no netfix nor youtube problems
Well I'm working a lot @t home... working with confidential documents where I'm signing for to keep it confidential.
Not always using my company VPN and so on... why because not always need it
The real threat is out there MITM or active eavesdropping is so EASY to perform and a serous problem if you now what it can do.
I you have DOT/DOH and perform a mitm can confirm that it wont work
In my country alone there are 10 million/1 year involved victims people,Business stealing there data and confidential material.
Cloudflare has make a decision for Privaty and security so no Edsn correct but your request will be sending to the closed location and cached from there.
More about EDNS cloudflare: is covering about 151 datecenters so impact will be small depending your location
Security comes always with decision need to be make and cut things indeed is it bad not always they do also a lot of stress tests to figure that out.
I'm glad there are people that are concern and more really need to
Glad to see people like
@Xentrk and
@john implemented DOT to make it possible Big thanks
Is it perfect DOH/DOT.....no but being aware of the treat and doing something about it that's what i like
Out there in the world there are still looking for solutions "studies"example ODNS
https://odns.cs.princeton.edu/