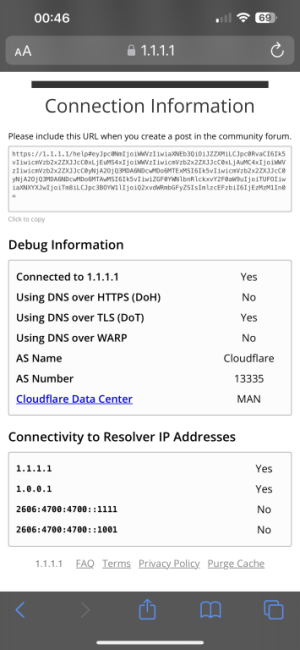
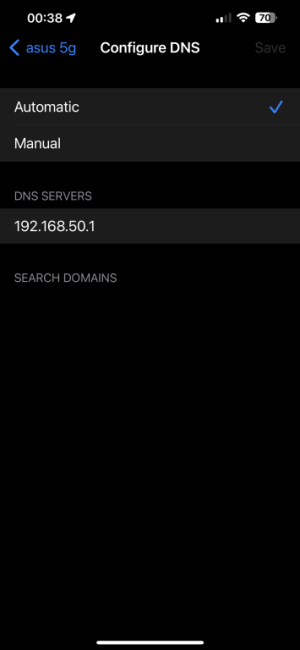
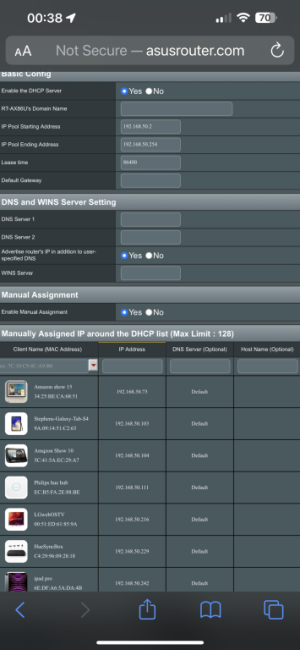
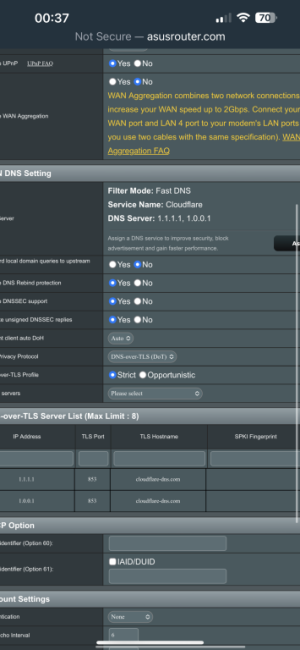
I'm setting up dns over tls but I don't think my devices are setup right,are these settings correct,I've enabled 1.1.1.1 in the wan with tls,in the lan dns 1 dns 2 I've left them blank,when I goto to cloudshare to test tls it says it working,the issue I've got is when I do a speed test on my nv shield it says my dns is 192.168.50.1 instead of 1.1.1.1,it the same on my iPhone dns setting is 192.168.50.1,shouldn't it say 1.1.1.1?
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Have I setup dns over tls correctly
- Thread starter hash70
- Start date
drinkingbird
Part of the Furniture
192.168.50.1 is your router, clients look up to the router, which then does a lookup to 1.1.1.1 via DOT. You can test if DOT is working using cloudflare's test.
That is the default behavior, if you want clients to see 1.1.1.1 directly you need to set "advertise router's DNS" to "no" and put 1.1.1.1 on the LAN settings. But you will lose DOT by doing that, unless you configure every client to use it.
Note however that using DoT is a bit over-hyped. There is also no need to do DNSSEC, just pick a DNS server that does that for you. I tried out DoT and found it slowed my queries down and disabled it. If my ISP wants to track what sites I'm looking up, don't really care, they can track the sites I visit anyway and everyone else (windows, google, various sites, etc) is already doing that also.
That is the default behavior, if you want clients to see 1.1.1.1 directly you need to set "advertise router's DNS" to "no" and put 1.1.1.1 on the LAN settings. But you will lose DOT by doing that, unless you configure every client to use it.
Note however that using DoT is a bit over-hyped. There is also no need to do DNSSEC, just pick a DNS server that does that for you. I tried out DoT and found it slowed my queries down and disabled it. If my ISP wants to track what sites I'm looking up, don't really care, they can track the sites I visit anyway and everyone else (windows, google, various sites, etc) is already doing that also.
Last edited:
Ah right,was jst confused why my devices were showing 192.168.50.1 as my dns instead of 1.1.1.1,cause I once set 1.1.1.1 in the dns 1&2 in the lan and all my devices showed 1.1.1.1 as the dns,I jst thought it wasn't working cause I tryed removing 1.1.1.1 in the wan and enabled adguard but my devices was still seeing adds
drinkingbird
Part of the Furniture
Ah right,was jst confused why my devices were showing 192.168.50.1 as my dns instead of 1.1.1.1,cause I once set 1.1.1.1 in the dns 1&2 in the lan and all my devices showed 1.1.1.1 as the dns,I jst thought it wasn't working cause I tryed removing 1.1.1.1 in the wan and enabled adguard but my devices was still seeing adds
Think of your router as a DNS proxy server. Your clients look up to the router, the router sends any non-cached entries upstream, and replies back using its internal IP.
If you want to use DoT then you must use the router proxy feature. If you want clients to see the DNS directly, disable the router proxy, and you also won't have DoT. DoT isn't a huge issue, I mean everyone is spying on your traffic and they can figure out what you're visiting in many other ways, but you can use it if you want. On my router it slowed things down quite a bit.
Generally it is better to have the router be the proxy, caching entries locally will be faster, and you can change DNS servers anytime and it is transparent to the client.
So the recommended setting is on LAN DHCP, leave both DNS blank and check off "advertise router's IP". All clients will receive 192.168.50.1 as their DNS.
On WAN set the DNS servers you want queries to go to (1.1.1.1, adguard, etc) and optionally enable DoT if those resolvers support it. DNSSEC isn't necessary with a recursive DNS server.
If you want to ensure a client never statically sets anything to bypass the router, go to DNSFilter/DNSDIrector and set it as "router" and enable it. That way all DNS traffic is intercepted by the router and uses the WAN DNS IPs, no matter what the client points to. The client never knows, they think the response is coming from the DNS they pointed to, but in reality it is coming from the router. Note this doesn't work with clients that use DoH (I believe firefox does this by default and Chrome/Edge have it as an option). You can enable the feature on the WAN page to block client auto DOH which helps prevent those browsers from doing that, but a savvy user can still force DoH.
Last edited:
I get it now,thx alot for taking the time to explain,appreciatedThink of your router as a DNS proxy server. Your clients look up to the router, the router sends any non-cached entries upstream, and replies back using its internal IP.
If you want to use DoT (like I said, if you're just looking up to recursive DNS, there really isn't any benefit) then you must use the router proxy feature. If you want clients to see the DNS directly, disable the router proxy, and you also won't have DoT.
Generally it is better to have the router be the proxy, caching entries locally will be faster, and you can change DNS servers anytime and it is transparent to the client.
So the recommended setting is on LAN DHCP, leave both DNS blank and check off "advertise router's IP". All clients will receive 192.168.50.1 as their DNS.
On WAN set the DNS servers you want queries to go to (1.1.1.1, adguard, etc).
If you want to ensure a client never statically sets anything to bypass the router, go to DNSFilter/DNSDIrector and set it as "router" and enable it. That way all DNS traffic is intercepted by the router and uses the WAN DNS IPs, no matter what the client points to. The client never knows, they think the response is coming from the DNS they pointed to, but in reality it is coming from the router. Note this doesn't work with clients that use DoH (I believe firefox does this by default and Chrome/Edge have it as an option). You can enable the feature on the WAN page to block client auto DOH which helps prevent those browsers from doing that, but a savvy user can still force DoH.
dave14305
Part of the Furniture
Just to clarify a very common misconception: the “Advertise router’s IP…” setting has no impact when DNS1 and DNS2 are empty. Only if either are filled in will the firmware consider the state of that checkbox.So the recommended setting is on LAN DHCP, leave both DNS blank and check off "advertise router's IP".
The net result is the same, but not because of the checkbox.
I too feel that DoT is slowing too much.Note however that using DoT is a bit over-hyped. There is also no need to do DNSSEC, just pick a DNS server that does that for you. I tried out DoT and found it slowed my queries down and disabled it. If my ISP wants to track what sites I'm looking up, don't really care, they can track the sites I visit anyway and everyone else (windows, google, various sites, etc) is already doing that also.
I am not very network savvy and am a bit confused on its workings.
Based on the above quote from the post, I want to precisely know the following
Can the ISP know what sites I am visiting if I use DoT or DoH ? My gut feeling is ISP will know unless I use VPN but am confused.they can track the sites I visit anyway
What is that ISP cannot see by using DoT or DoH? What does using DoT or DoH really achieve? On Security? On Privacy?
What does DNSSEC achieve?no need to do DNSSEC, just pick a DNS server that does that for you
I generally tend to use OpenDNS Familyshield servers at router level for protection from inappropriate sites and security.
Last edited:
What is a recursive DNS server?DNSSEC isn't necessary with a recursive DNS server.
drinkingbird
Part of the Furniture
What is a recursive DNS server?
Honestly you should just use standard DNS settings and not mess with the rest if you don't understand it.
drinkingbird
Part of the Furniture
Just to clarify a very common misconception: the “Advertise router’s IP…” setting has no impact when DNS1 and DNS2 are empty. Only if either are filled in will the firmware consider the state of that checkbox.
The net result is the same, but not because of the checkbox.
So the router advertises itself by default, either way, same result. I'm just suggesting they leave it at the defaults, which is both fields blank and router IP "yes", at least as far as I recall it is, since I haven't changed mine and that's what it is set to.
Tech9
Part of the Furniture
What does using DoT or DoH really achieve?
Encrypts the DNS traffic between you and the upstream DNS server preventing eventual MITM (man in the middle) altering of your DNS requests. Your ISP always sees where are you going because you request connections by IP address after the DNS requests are resolved. DoT/DoH may be slower depending on the upstream DNS server load. It doesn't affect your router much with <10 requests per second, but may affect a public DNS server with >1.000.000 requests per second. I believe this is happening to Quad9 servers around my area - the slowest around with DoT enabled and forwarding requests to other servers outside of the country with available server in my city. For that reason (and some others) I don't use nor recommend Quad9.
I generally tend to use OpenDNS Familyshield servers
OpenDNS offers OpenDNS Home free accounts with custom filtering categories. You may take a look - they work well and fast in many places.
I just need to figure out how to update the ISP provided IP address which changes on a regular basis, at least after a few days or weeks or when the router is rebooted.OpenDNS offers OpenDNS Home free accounts
I did not find any way to update that automatically on OpenDNS site using router. The custom filtering capabilities depend on correct IP being tied to my OpenDNS Free Account.
dave14305
Part of the Furniture
dnsomatic.com is supported by both the firmware and OpenDNS to manage IP changes in this scenario.I did not find any way to update that automatically on OpenDNS site using router
I will highly appreciate if you can provide precise instructions on how to use dnsomatic.com to update OpenDNS from stock firmware AIMesh Firmware Version 3.0.0.4.388_22525dnsomatic.com is supported by both the firmware
Tech9
Part of the Furniture
how to use dnsomatic.com to update OpenDNS from stock firmware
See here:

DDNS with DNSOMATIC ???
Hi, I am trying to setup my DDNS but it keeps failing. Reading the past posts there was a suggestion to use: "all.dnsomatic.com" for the host value but it still does not work. Anybody got this working please? Server: www.dnsomatic.com (selected from dropdown) Host: all.dnsomatic.com (also tried...
I have my router WAN connected to ISP provided modem router LAN. So my ASUS is in Double NAT environment and I am getting this message.See here:

DDNS with DNSOMATIC ???
Hi, I am trying to setup my DDNS but it keeps failing. Reading the past posts there was a suggestion to use: "all.dnsomatic.com" for the host value but it still does not work. Anybody got this working please? Server: www.dnsomatic.com (selected from dropdown) Host: all.dnsomatic.com (also tried...www.snbforums.com
The wireless router currently uses a private WAN IP address.
This router may be in the multiple-NAT environment and DDNS service cannot work in this environment.
I use stock ASUS firmware which was updated to 388 few weeks ago to AIMesh Firmware Version 3.0.0.4.388_22525.
Clark Griswald
Very Senior Member
You need to place your ISP modem in Bridge Mode, then your router will work properly.
drinkingbird
Part of the Furniture
I have my router WAN connected to ISP provided modem router LAN. So my ASUS is in Double NAT environment and I am getting this message.
The wireless router currently uses a private WAN IP address.
This router may be in the multiple-NAT environment and DDNS service cannot work in this environment.
I use stock ASUS firmware which was updated to 388 few weeks ago to AIMesh Firmware Version 3.0.0.4.388_22525.
If you're using the Asus router's built in DDNS you need to set the "method to retrieve IP" as "external". It will then look up your IP on a service like whatsmyip.com.
You'll need to put your Asus into DMZ of the ISP router, or forward your inbound ports on both routers. If they support bridge mode as the person above mentions, that makes it easier.
Tech9
Part of the Furniture
The wireless router currently uses a private WAN IP address.
This router may be in the multiple-NAT environment and DDNS service cannot work in this environment.
This is one of Asuswrt GUI bugs in current 388 firmware.
The history:
- early 386 had internal detection only with no options
- later 386 introduced user selectable internal + external detection
- current 388 has external detection by default and user selectable option was removed
It will work in 388, don't pay attention to the message.
You need to place your ISP modem in Bridge Mode, then your router will work properly.
Not needed. See above.
If you're using the Asus router's built in DDNS you need to set the "method to retrieve IP" as "external".
Doesn't exist anymore.
Similar threads
- Replies
- 3
- Views
- 706
- Replies
- 11
- Views
- 736
- Replies
- 20
- Views
- 1K
Similar threads
Similar threads
-
How to setup IPSec VPN client's DNS server? (RT-AX86U)
- Started by kamanwu
- Replies: 2
-
RT-AX88U Pro - How to access 4G bridged modem GUI in Dual WAN setup
- Started by Mando
- Replies: 2
-
RT-AX88U Pro and RT-AX86U Pro vs Dual GT-AXE11000 Setup
- Started by Mxlt
- Replies: 5
-
Setup help - ZenWiFi Pro XT12 meshed with a AX88U.
- Started by Kerry
- Replies: 3
-
Node Configuration Setup and wiring
- Started by sandiegoboy
- Replies: 2
-
Adding RT-AX86U pro or AX11000 pro to existing setup
- Started by Plahy
- Replies: 6
-
-
Can you recommend me a new aimesh node for my setup?
- Started by autopilot
- Replies: 1
-
New GT-AX6000 setup questions
- Started by Megahurtz
- Replies: 24
Latest threads
-
Can't get 2gbps to my unraid server
- Started by zekesdad
- Replies: 2
-
changed AC68U to AX86U Pro, same guest network setting but all devices gone?
- Started by Heronimos
- Replies: 2
-
-
-
GT-BE98 Force Guest Network To Use 5GHz-2 Radio
- Started by Wimbus
- Replies: 3
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!