384.12 Beta 2 is now available. Changes since beta 1:
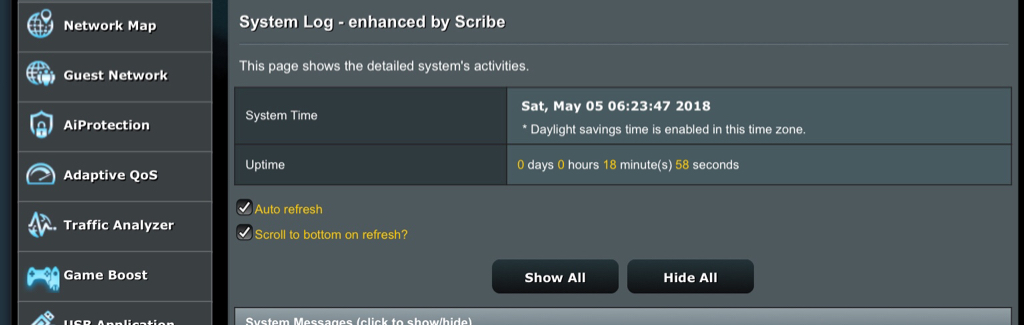
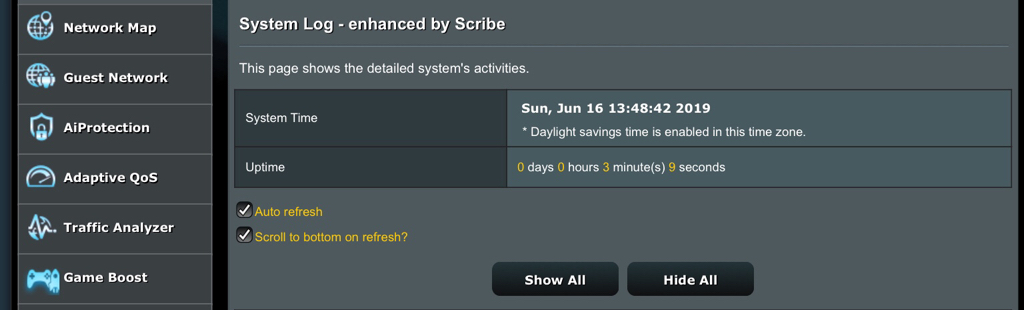
There's been a number of changes in how some services are started at boot time, mainly relative to NTP, and services that require a properly updated clock (DDNS and OpenVPN, due to their TLS needs). Please make sure that these services still start correctly The changes should reduce the number of times these services get restarted at boot, in addition to preventing lengthy stalls during the initial WAN connection (particularly for PPPoE users).
Also as a heads-up, the project website will soon be moved from my personal domain into its own dedicated domain (this will also include my email address for things related to this project). This beta already points the update checks to the new domain.
The project website content will remain the same, only the URL will change. I will wait a while before configuring an automated redirection, to give people some time to become aware that this is a planned change and not a hijack of some sort.
Code:
5e4d494650 Migrate to the new dedicated domain name; update to the new fwupdate file structure
aad0216a8f Updated documentation
a9fb116f5c rc: further tweaks to ntpd handling on wanup()
bae3069e0a curl: update to 7.65.1
3dcb7c8ebf rc: remove unnecessary linking with libbcmcrypto
7711e8c535 rc: only start ddns and Openvpn in wan_up() if ntpd is set, with a small max wait period, and start both of these on the first ntpd sync event
eac9723ad5 openssl11: Revert the DEVRANDOM_WAIT feature
f2972c5a21 openssl11: issue-8998: Ensure that the alert is generated and reaches the remote
fbe9230036 openssl11: The SHA256 is not a mandatory digest for DSA.
4e91815532 rc: firewall: define VUPNP and PUPNP chains in default nat_rules
4520e3fe38 webui: fix Network Analysis symlinks location for RT-AC5300
5e8f5f302d rc: re-add variable to start_ovpn_*() funtions that is required
9166dd215a rc: reduce max wait for ntp sync on wanup from 51 to 26 secs
a11bc194f0 rc: openvpn: remove waits for ntp sync in openvpn code since wanup already does it before starting OpenVPN instances.
a34c408f6e netool: enable netool for the RT-AC87U - missing in 588ab6ea97 (closes #316)
6688a6d2ab Bumped revision to beta 2There's been a number of changes in how some services are started at boot time, mainly relative to NTP, and services that require a properly updated clock (DDNS and OpenVPN, due to their TLS needs). Please make sure that these services still start correctly The changes should reduce the number of times these services get restarted at boot, in addition to preventing lengthy stalls during the initial WAN connection (particularly for PPPoE users).
Also as a heads-up, the project website will soon be moved from my personal domain into its own dedicated domain (this will also include my email address for things related to this project). This beta already points the update checks to the new domain.
The project website content will remain the same, only the URL will change. I will wait a while before configuring an automated redirection, to give people some time to become aware that this is a planned change and not a hijack of some sort.