madfusker
Regular Contributor
I have PIA running on my router with the client policy shown below. So only my router and desktop are excluded from going through my PIA VPN that is running on the router. I also have a laptop that by default routes through the VPN due to the /24 rule and is on 192.168.1.20. My problem is that when I remotely connect with my Android phone to my router via OpenVPN (FYI-it assigns 10.8.0.2 to my phone), I can only connect to the excluded machines on the WAN, and not my laptop that is inside the PIA VPN on the router.
Is there a way I can connect to all machines on my network when I VPN home so I can manage them regardless if they are on or off the VPN? and what rule would allow this?
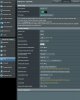
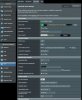
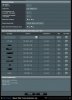
VPN client Policy Rules using PIA VPN (strict):
All LAN 192.168.1.0/24 0.0.0.0 VPN
Router 192.168.1.1 0.0.0.0 WAN
Desktop 192.168.1.10 0.0.0.0 WAN
I had this working well at one time, but somehow lost the setting that enabled it. :/
Is there a way I can connect to all machines on my network when I VPN home so I can manage them regardless if they are on or off the VPN? and what rule would allow this?
VPN client Policy Rules using PIA VPN (strict):
All LAN 192.168.1.0/24 0.0.0.0 VPN
Router 192.168.1.1 0.0.0.0 WAN
Desktop 192.168.1.10 0.0.0.0 WAN
I had this working well at one time, but somehow lost the setting that enabled it. :/
Last edited: