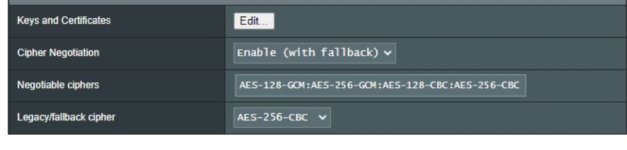
Feb 9 18:31:13 pppd[1440]: Connection terminated.
Feb 9 18:31:13 pppd[1440]: Modem hangup
Feb 9 18:31:13 wlceventd: wlceventd_proc_event(491): eth7: Deauth_ind 40:2F:86:05:43:2C, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 18:31:13 wlceventd: wlceventd_proc_event(491): eth7: Deauth_ind 68:72:C3:81:A3:C8, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 18:31:13 wlceventd: wlceventd_proc_event(491): eth6: Deauth_ind 8C:85:80:C9:FD

6, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 18:31:13 wlceventd: wlceventd_proc_event(491): eth6: Deauth_ind 8C:85:80:E7:F5:C4, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 18:31:13 wlceventd: wlceventd_proc_event(491): eth6: Deauth_ind 54:48:E6:71:4B:B3, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 18:31:14 wlceventd: wlceventd_proc_event(508): eth7: Disassoc 40:2F:86:05:43:2C, status: 0, reason: Disassociated because sending station is leaving (or has left) BSS (8), rssi:0
Feb 9 18:31:15 wlceventd: wlceventd_proc_event(508): eth6: Disassoc 8C:85:80

3:C9

F, status: 0, reason: Disassociated because sending station is leaving (or has left) BSS (8), rssi:0
Feb 9 18:31:16 wlceventd: wlceventd_proc_event(508): eth6: Disassoc 8C:85:80:E7:F5:C4, status: 0, reason: Disassociated because sending station is leaving (or has left) BSS (8), rssi:0
Feb 9 18:31:16 wlceventd: wlceventd_proc_event(508): eth6: Disassoc 8C:85:80:C9:FD

6, status: 0, reason: Disassociated because sending station is leaving (or has left) BSS (8), rssi:0
Feb 9 18:31:17 acsd: acs_candidate_score_busy(951): eth6: busy check failed for chanspec: 0x180a (8l)
Feb 9 18:31:17 acsd: acs_candidate_score_intf(1003): eth6: intf check failed for chanspec: 0x180a (8l)
Feb 9 18:31:17 acsd: acs_candidate_score_bgnoise(1320): eth6: bgnoise check failed for chanspec: 0x180a (8l)
Feb 9 18:31:17 acsd: acs_candidate_score_txop(1575): eth6: txop check failed for chanspec: 0x180a
Feb 9 18:31:17 acsd: acs_candidate_score_busy(951): eth6: busy check failed for chanspec: 0x180b (9l)
Feb 9 18:31:17 acsd: acs_candidate_score_intf(1003): eth6: intf check failed for chanspec: 0x180b (9l)
Feb 9 18:31:17 acsd: acs_candidate_score_bgnoise(1320): eth6: bgnoise check failed for chanspec: 0x180b (9l)
Feb 9 18:31:17 acsd: acs_candidate_score_txop(1575): eth6: txop check failed for chanspec: 0x180b
Feb 9 18:31:17 acsd: acs_set_chspec: 0x180a (8l) for reason APCS_CSTIMER
Feb 9 18:31:18 acsd: eth6: selected_chspec is 0x180a (8l)
Feb 9 18:31:18 acsd: eth6: Adjusted channel spec: 0x180a (8l)
Feb 9 18:31:18 acsd: eth6: selected channel spec: 0x180a (8l)
Feb 9 18:31:18 acsd: eth6: txop channel select: Performing CSA on chspec 0x180a
Feb 9 18:31:58 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:33:13 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:34:28 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:35:43 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:36:58 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:38:13 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:39:28 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:40:43 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:41:58 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:43:13 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:44:28 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:45:43 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:46:59 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:48:14 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:49:29 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:49:46 acsd: acs_candidate_score_busy(951): eth6: busy check failed for chanspec: 0x180a (8l)
Feb 9 18:49:46 acsd: acs_candidate_score_intf(1003): eth6: intf check failed for chanspec: 0x180a (8l)
Feb 9 18:49:46 acsd: acs_candidate_score_bgnoise(1320): eth6: bgnoise check failed for chanspec: 0x180a (8l)
Feb 9 18:49:46 acsd: acs_candidate_score_txop(1575): eth6: txop check failed for chanspec: 0x180a
Feb 9 18:49:46 acsd: acs_candidate_score_busy(951): eth6: busy check failed for chanspec: 0x180b (9l)
Feb 9 18:49:46 acsd: acs_candidate_score_intf(1003): eth6: intf check failed for chanspec: 0x180b (9l)
Feb 9 18:49:46 acsd: acs_candidate_score_bgnoise(1320): eth6: bgnoise check failed for chanspec: 0x180b (9l)
Feb 9 18:49:46 acsd: acs_candidate_score_txop(1575): eth6: txop check failed for chanspec: 0x180b
Feb 9 18:50:44 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:51:59 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:53:14 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:54:29 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:55:44 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:56:59 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:58:14 pppd[1440]: Timeout waiting for PADO packets
Feb 9 18:59:29 pppd[1440]: Timeout waiting for PADO packets
Feb 9 19:00:44 pppd[1440]: Timeout waiting for PADO packets
Feb 9 19:02:00 pppd[1440]: Timeout waiting for PADO packets
Feb 9 19:03:15 pppd[1440]: Timeout waiting for PADO packets
Feb 9 19:04:30 pppd[1440]: Timeout waiting for PADO packets
0:47 services: apply rules error(18891)
Feb 9 20:10:49 rc_service: httpds 1221:notify_rc restart_wan_if 0;restart_stubby
Feb 9 20:10:49 pppd[31707]: Unable to complete PPPoE Discovery
Feb 9 20:10:49 wsdd2[1849]: error: wsdd-mcast-v4: wsd_send_soap_msg: send
Feb 9 20:10:51 pppd[32125]: pppd 2.4.7 started by stolker, uid 0
Feb 9 20:11:02 services: apply rules error(18857)
Feb 9 20:11:02 zcip_client: configured 169.254.95.63
Feb 9 20:11:07 services: apply rules error(18891)
Feb 9 20:11:12 services: apply rules error(18891)
Feb 9 20:11:17 services: apply rules error(18891)
Feb 9 20:11:22 services: apply rules error(18891)
Feb 9 20:11:26 pppd[32125]: Timeout waiting for PADO packets
Feb 9 20:11:27 services: apply rules error(18891)
Feb 9 20:11:32 services: apply rules error(18891)
Feb 9 20:11:37 services: apply rules error(18891)
Feb 9 20:11:42 services: apply rules error(18891)
Feb 9 20:11:47 services: apply rules error(18891)
Feb 9 20:11:52 services: apply rules error(18891)
Feb 9 20:11:57 services: apply rules error(18891)
Feb 9 20:12:02 services: apply rules error(18891)
Feb 9 20:12:07 services: apply rules error(18891)
Feb 9 20:12:12 services: apply rules error(18891)
Feb 9 20:28:22 kernel: dhd_flow_rings_delete_for_peer: ifindex 0
Feb 9 20:28:22 kernel: dhd_prot_flow_ring_delete: Send Flow Delete Req RING ID 194 for peer 58:bf:25:2d:f2:38 prio 5 ifindex 0
Feb 9 20:28:22 kernel: dhd_prot_flow_ring_delete_response_process: Flow Delete Response status = 0
Feb 9 20:28:22 wlceventd: wlceventd_proc_event(491): eth6: Deauth_ind 58:BF:25:2D:F2:38, status: 0, reason: Deauthenticated because sending station is leaving (or has left) IBSS or ESS (3), rssi:0
Feb 9 20:28:22 kernel: dhd_flow_rings_delete_for_peer: ifindex 0
Feb 9 20:28:22 wlceventd: wlceventd_proc_event(491): eth6: Deauth_ind 58:BF:25:2D:F2:38, status: 0, reason: Previous authentication no longer valid (2), rssi:0
Feb 9 20:28:22 kernel: CONSOLE: 108279.167 iov:SCB_DEAUTH
Feb 9 20:28:22 kernel: CONSOLE: 108279.167 wl0.0: wlc_ampdu_flush_scb_tid flushing 0 packets for 58:bf:25:2d:f2:38 AID 22 tid 5
Feb 9 20:28:22 kernel: CONSOLE: 108279.169 iov:SCB_DEAUTH
Feb 9 20:28:22 kernel: CONSOLE: 108279.169 iov:SCB_DEAUTH
Feb 9 20:28:22 kernel: CONSOLE: 108279.191 iov:SCB_DEAUTH
Feb 9 20:28:22 kernel: CONSOLE: 108279.191 iov:SCB_DEAUTH
Feb 9 20:28:23 wlceventd: wlceventd_proc_event(527): eth6: Auth 58:BF:25:2D:F2:38, status: Successful (0), rssi:0
Feb 9 20:28:23 wlceventd: wlceventd_proc_event(556): eth6: Assoc 58:BF:25:2D:F2:38, status: Successful (0), rssi:0
Feb 9 20:28:23 kernel: CONSOLE: 108279.831 wlc_ap_authresp: status 0
Feb 9 20:28:23 kernel: CONSOLE: 108279.834 wlc_ap_process_assocreq_done status 0
Feb 9 20:28:23 kernel: CONSOLE: 108279.836 iov:SCB_DEAUTH
Feb 9 20:28:23 kernel: CONSOLE: 108279.837 tx

rep:802.1x
Feb 9 20:28:23 kernel: CONSOLE: 108279.839 wl0.0: wlc_send_bar: for 58:bf:25:2d:f2:38 seq 0x1 tid 5
Feb 9 20:28:24 services: apply rules error(18891)
Feb 9 20:28:24 kernel: CONSOLE: 108280.833 tx

rep:802.1x
Feb 9 20:28:25 kernel: CONSOLE: 108281.828 tx

rep:802.1x