Router: RT-AC88U
Firmware: Was: 384.5 , Now: 384.6_beta1
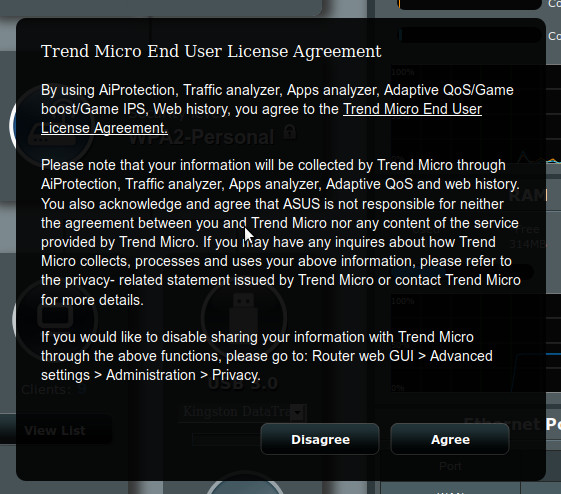
Upload and reboot went ok. But once logged in, I get this popup:
Also I now see a new tab in 'Administration' labelled 'Privacy':
I have been using 'Adaptive QOS' w/ the 'FreshJR_QOS' and 'FreshJR_QOS_fakeTC' scripts for a while now in 384.x firmware, but I've never had to 'Agree' to this EULA before in order to use QOS. And clicking 'Disagree' disables QOS. Is this expected behavior now, i.e., 'Agree' to Trend Micro's EULA, or Adaptive QOS will not work?
Other than this EULA issue, and the fact that QOS was not working, all was well for the next 12+ hours.
Then I rebooted.
Another issue, after just described boot up. Looking at the 'System Log-General log' I see a flood of the following which I was not seeing after the initial update to '384.6_beta1'.
Code:
...
Jul 19 13:01:44 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:46 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:47 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:52 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:53 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:53 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:53 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:53 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:54 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:55 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:55 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:56 kernel: TCP: time wait bucket table overflow
Jul 19 13:01:57 kernel: TCP: time wait bucket table overflow
...
Looked around the forums a bit, these messages seemed wireless related?
So ssh'd into the router restarted the wireless:
Since issuing that command, no more 'TCP: time wait bucket table overflow' messages.
IDK?
.