You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Can any tell me why this is not working?
- Thread starter AsusRouterUser
- Start date
ColinTaylor
Part of the Furniture
Post your screenshot again without the IP information blanked out. There is no reason to hide private IP addresses, it just makes problems more difficult to diagnose.
Look in the system log for error messages when you start the VPN client.
You appear to be using an old version of the firmware. Policy Rules was replaced by VPN Director some time ago.
Look in the system log for error messages when you start the VPN client.
You appear to be using an old version of the firmware. Policy Rules was replaced by VPN Director some time ago.
Last edited:
AsusRouterUser
Occasional Visitor
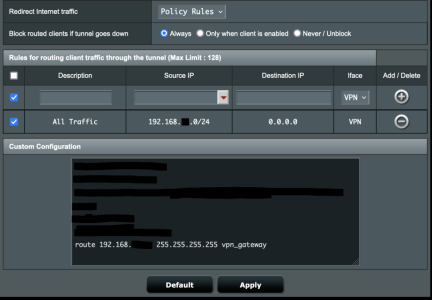
Sorry I am not where I can take another screenshot, however the missing parts are at the top the All Traffic is 192.168.50.0/24 and the part at the bottom is route 192.168.25.100 255.255.255.255 vpn_gateway and that is a local machine on the other side of the VPN, I can get to it no problem with All instead of Policy Rules, but with it set that way if the VPN goes down it uses my regular internet instead of just thinking there is NO internet like it does with Policy Rules (which is what I want). As for it being old firmware it is because it is an old router and that is the newest firmware I can get for it. I only use it for temp stuff most the time it is off.Post your screenshot again without the IP information blanked out. There is no reason to hide private IP addresses, it just makes problems more difficult to diagnose.
Look in the system log for error messages when you start the VPN client.
You appear to be using an old version of the firmware. Policy Rules was replaced by VPN Director some time ago.
ColinTaylor
Part of the Furniture
I've read this about 20 times and I still can't work out what "it" is having the problem.I can get to it no problem with All instead of Policy Rules, but with it set that way if the VPN goes down it uses my regular internet instead of just thinking there is NO internet like it does with Policy Rules (which is what I want).
Are you saying this problem only happens when you have the "route" command present in your custom configuration?
Is "it" the router? So you're saying that "Block routed clients if tunnel goes down" is not working when Policy Rules are not being used? This seems to be the opposite of what you said in post #1.
AsusRouterUser
Occasional Visitor
Sorry I was not clear the issue is I can't get to the routed device ie 192.168.25.100 when it is set to Policy Rules but I can get to it if, it is set to All, and I want to use Policy Rules, but I can't figure out why the "route 192.168.25.100 255.255.255.255 vpn_gateway" does not work when it is set to Policy Rules. Sorry and it is "Redirect Internet traffic".I've read this about 20 times and I still can't work out what "it" is having the problem.
Are you saying this problem only happens when you have the "route" command present in your custom configuration?
Is "it" the router? So you're saying that "Block routed clients if tunnel goes down" is not working when Policy Rules are not being used? This seems to be the opposite of what you said in post #1.
ColinTaylor
Part of the Furniture
Do you need the As far as I can see that would only be required if the device at 192.168.25.100 wanted to initiate a connection back to your router.
Sorry, ignore the second part. I got the client and server ends of the tunnel confused.
route 192.168.25.100 255.255.255.255 vpn_gateway line at all? Sorry, ignore the second part. I got the client and server ends of the tunnel confused.
Last edited:
AsusRouterUser
Occasional Visitor
Well if I take out "route 192.168.25.100 255.255.255.255 vpn_gateway" it does not connect on All or Policy Rules, but with it in I can get to it on All but not Policy Rules.Do you need theroute 192.168.25.100 255.255.255.255 vpn_gatewayline at all? As far as I can see that would only be required if the device at 192.168.25.100 wanted to initiate a connection back to your router.
ColinTaylor
Part of the Furniture
See the edit to my previous post.Well if I take out "route 192.168.25.100 255.255.255.255 vpn_gateway" it does not connect on All or Policy Rules, but with it in I can get to it on All but not Policy Rules.
Can you confirm that 192.168.25.0/24 is the network on the server side of the tunnel? Is there any unusual routing happening on the remote network?
AsusRouterUser
Occasional Visitor
Yes 192.168.25.0/24 is definitely the server side of the tunnel and no there is nothing unusual happening on it.See the edit to my previous post.
Can you confirm that 192.168.25.0/24 is the network on the server side of the tunnel? Is there any unusual routing happening on the remote network?
ColinTaylor
Part of the Furniture
Sorry, I'm out of ideas. I don't have any way of testing this and in any case the implementation of policy rules has changed over time.
You could try looking at the output of these commands and comparing them with and without policy rules.
You could try looking at the output of these commands and comparing them with and without policy rules.
Code:
ip rule
ip route show table main
ip route show table ovpnc1
Last edited:
AsusRouterUser
Occasional Visitor
Ok well thanks for trying to help anyway, I appreciate your time. these are the logs when Policy Rules is on...Sorry, I'm out of ideas. I don't have any way of testing this and in any case the implementation of policy rules has changed over time.
You could try looking at the output of these commands and comparing them with and without policy rules.
Code:ip rule ip route show table main ip route show table ovpnc1
Jul 21 13:39:53 openvpn[2460]: /usr/sbin/ip route add “remote ip”/32 via “my ip”
Jul 21 13:39:53 openvpn[2460]: /usr/sbin/ip route add 0.0.0.0/1 via 10.12.234.1
Jul 21 13:39:53 openvpn[2460]: /usr/sbin/ip route add 128.0.0.0/1 via 10.12.234.1
Jul 21 13:39:53 openvpn[2460]: /usr/sbin/ip route add 192.168.25.100/32 via 10.12.234.1
Jul 21 13:39:54 openvpn-routing: Configuring policy rules for client 1
Jul 21 13:39:54 openvpn-routing: Creating VPN routing table
Jul 21 13:39:54 openvpn-routing: Removing route for 0.0.0.0/1 to tun11 from VPN table
Jul 21 13:39:54 openvpn-routing: Removing route for 128.0.0.0/1 to tun11 from VPN table
Jul 21 13:39:54 openvpn-routing: Removing route for 0.0.0.0/1 to tun11 from table main
Jul 21 13:39:54 openvpn-routing: Removing route for 128.0.0.0/1 to tun11 from table main
Jul 21 13:39:54 openvpn-routing: Retained route for 192.168.25.100 to tun11 in table main
Jul 21 13:39:54 openvpn-routing: Removing rule 10101 from routing policy
Jul 21 13:39:54 openvpn-routing: Added 192.168.50.0/24 to 0.0.0.0 through VPN to routing policy
Jul 21 13:39:54 openvpn-routing: Tunnel re-established, restoring WAN access to clients
Jul 21 13:39:54 openvpn-routing: Setting default VPN route via 10.12.234.1
Jul 21 13:39:54 openvpn-routing: VPN WAN address is “remote ip”
Jul 21 13:39:54 openvpn-routing: Completed routing policy configuration for client 1
Jul 21 13:39:54 openvpn[2460]: Initialization Sequence Completed
AsusRouterUser
Occasional Visitor
Ok well here is the output of those commands...Sorry, I'm out of ideas. I don't have any way of testing this and in any case the implementation of policy rules has changed over time.
You could try looking at the output of these commands and comparing them with and without policy rules.
Code:ip rule ip route show table main ip route show table ovpnc1
This is with it set to All and here it WORKS...
# ip route show table main
x.x.x.x dev eth0 scope link
192.168.25.100 via 10.12.234.1 dev tun11
"SERVER IP" via x.x.x.x dev eth0
192.168.50.0/24 dev br0 proto kernel scope link src 192.168.50.1
10.12.234.0/24 dev tun11 proto kernel scope link src 10.12.234.2
x.x.x.x/24 dev eth0 proto kernel scope link src "MY IP"
127.0.0.0/8 dev lo scope link
0.0.0.0/1 via 10.12.234.1 dev tun11
128.0.0.0/1 via 10.12.234.1 dev tun11
default via x.x.x.x dev eth0
# ip route show table ovpnc1
x.x.x.x dev eth0 scope link
"SERVER IP" via x.x.x.x dev eth0
192.168.50.0/24 dev br0 proto kernel scope link src 192.168.50.1
x.x.x.x/24 dev eth0 proto kernel scope link src "MY IP"
127.0.0.0/8 dev lo scope link
This is with Policy Rules on and it NOT WORKING...
# ip rule
0: from all lookup local
10101: from 192.168.50.0/24 lookup ovpnc1
32766: from all lookup main
32767: from all lookup default
# ip route show table main
x.x.x.x dev eth0 scope link
192.168.25.100 via 10.12.234.1 dev tun11
"SERVER IP" via x.x.x.x dev eth0
192.168.50.0/24 dev br0 proto kernel scope link src 192.168.50.1
10.12.234.0/24 dev tun11 proto kernel scope link src 10.12.234.2
x.x.x.x/24 dev eth0 proto kernel scope link src "MY IP"
127.0.0.0/8 dev lo scope link
default via x.x.x.x dev eth0
# ip route show table ovpnc1
x.x.x.x dev eth0 scope link
"SERVER IP" via x.x.x.x dev eth0
192.168.50.0/24 dev br0 proto kernel scope link src 192.168.50.1
x.x.x.x/24 dev eth0 proto kernel scope link src "MY IP"
127.0.0.0/8 dev lo scope link
default via 10.12.234.1 dev tun11
The only real difference I see is when it works I see this...
128.0.0.0/1 via 10.12.234.1
But I don't understand this well enough to know what that means or how to fix it.
Similar threads
- Replies
- 0
- Views
- 349
- Replies
- 7
- Views
- 900
- Replies
- 1
- Views
- 814
Similar threads
Similar threads
-
-
Can someone read my syslog and tell me why I keep losing internet?
- Started by Micharlie
- Replies: 21
-
RESOLVED: Lost access to WebUI from LAN, SSH is working
- Started by GPSMapper
- Replies: 1
-
ASUS RT-AC68U not working after Merlin firmware update, did I brick it?
- Started by dbaser
- Replies: 15
-
The Asus + Merlin + NordVPN router never disconnects from the internet when NordVPN stops working for a moment.
- Started by DiOnlyThingINoIsThatIDont
- Replies: 4
-
-
[AX86U Pro] WIFI not working well after updating from stock to Merlin
- Started by Neo-ST
- Replies: 33
-
-
-
Latest threads
-
-
-
Can't get 2gbps to my unraid server
- Started by zekesdad
- Replies: 2
-
changed AC68U to AX86U Pro, same guest network setting but all devices gone?
- Started by Heronimos
- Replies: 4
-
Sign Up For SNBForums Daily Digest
Get an update of what's new every day delivered to your mailbox. Sign up here!