D
Deleted member 62525
Guest
With the new release implementing DNS over TLS how dns works with OpenVPN client has changed.
Using Stubby I was able to have OpenVPN client and DoT working perfectly. With OpenVPN client connected the router would use VPN DNS and if I got disconnected or VPN connection dropped DoT took over.
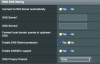
This config no longer works in the newest release 384.12. If both VPN and DoT is configured the VPN client uses DoT dns servers. I have VPN client dns set to strict as before using rt-86u.
Any suggestions guys? I have tried many things and the only config that works for me is to disable DoT. Then VPN client picks up proper dns.
Using Stubby I was able to have OpenVPN client and DoT working perfectly. With OpenVPN client connected the router would use VPN DNS and if I got disconnected or VPN connection dropped DoT took over.
This config no longer works in the newest release 384.12. If both VPN and DoT is configured the VPN client uses DoT dns servers. I have VPN client dns set to strict as before using rt-86u.
Any suggestions guys? I have tried many things and the only config that works for me is to disable DoT. Then VPN client picks up proper dns.