EDITED: applies to 384.4.beta1
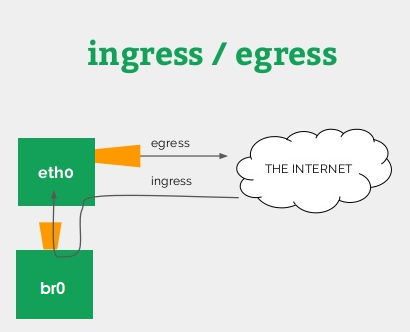
Looking closely at the output of the various tc -s ... commands when downloading/uploading files, I have discovered that the ingress (ffff:) qdisc on the eth0 interface behaves very strangely:
This mixing of ingress/egress traffic is very surprising. I use Linux traffic control on servers at work and do not witness similar behavior (unintuitive and contradicting all 'tc' documentation I have read).
On the other hand, it is also quite surprising to see eth0 - the WAN interface - also be the underlying interface for the vlan1@eth0, part or the br0 - LAN - bridge. This strange setup has to do with the underlying Broadcom Roboswitch; [EDITED] see comment #3 below for the detailed explanation.
I can not explain why ingress traffic is not filtered as per ad-hoc rules. No easy way to tell whether this strange behavior is a kernel/driver bug or results from the eth0/vlan1 mix.
[EDITED] On the other hand, that mix - along a bug in the 802.1Q qdisc filter rule - explains why downloaded/ingress traffic is eventually (wrongly) throttled as per upload settings, in the 1:40 qdisc/class:
WARNING: This works on the RT-AC88U's kernel 2.6.36.4brcmarm (firmware 384.x); it may NOT work on 3.x or more recent kernels (tc syntax for VLAN filtering MUST then use basic match (meta vlan ID) syntax, which requires updated - ematch-able - tc/iproute2 tool)
This fixes:
This does NOT fix:
Looking closely at the output of the various tc -s ... commands when downloading/uploading files, I have discovered that the ingress (ffff:) qdisc on the eth0 interface behaves very strangely:
- downloaded/ingress traffic DOES appear on the ingress (ffff:) qdisc (tc -s qdisc ls dev eth0)
- BUT does NOT seem to be taken in account by the matching filter (tc -s filter ls dev eth0 parent ffff:); [EDITED] see comment #13 for reason why
- and INSTEAD appears in the 1:40 ("low" priority) qdisc/class, which one would expect to handle only uploaded/egress "low" priority traffic (tc -s class ls dev eth0)
This mixing of ingress/egress traffic is very surprising. I use Linux traffic control on servers at work and do not witness similar behavior (unintuitive and contradicting all 'tc' documentation I have read).
On the other hand, it is also quite surprising to see eth0 - the WAN interface - also be the underlying interface for the vlan1@eth0, part or the br0 - LAN - bridge. This strange setup has to do with the underlying Broadcom Roboswitch; [EDITED] see comment #3 below for the detailed explanation.
I can not explain why ingress traffic is not filtered as per ad-hoc rules. No easy way to tell whether this strange behavior is a kernel/driver bug or results from the eth0/vlan1 mix.
[EDITED] On the other hand, that mix - along a bug in the 802.1Q qdisc filter rule - explains why downloaded/ingress traffic is eventually (wrongly) throttled as per upload settings, in the 1:40 qdisc/class:
- the 802.1Q filter rule - tc filter ... parent 1: prio 6 protocol 802.1q handle 6 fw flowid 1:60 - is intended to redirect LAN traffic to the ad-hoc 1:60 (1Gbits/s) qdisc/class
- in order for this rule to work, traffic must BOTH be VLAN(802.1Q)-tagged and (CONN)MARK-ed with value fw 6
- BUT looking at the QOSO (mangle) iptables chain, one can see that traffic will NOT be (CONN)MARK-ed with value fw 6 if it matches a previous classification; e.g. if one classifies HTTP (TCP 80) traffic to "medium" priority (fw 3), downloaded/ingress packets will NEVER be classified as fw 6, even when they egress as LAN traffic on vlan1@eth0
- in consequence, such 802.1Q packets match no other filter rules (they are not caught by protocol ip rules) and end up in the root HTB qdisc's default 1:40 sub-qdisc/class
# QOS
# ... fix erroneous LAN qdisc filter (-> match all VLAN ID 1 - LAN - traffic)
tc filter del dev eth0 parent 1: prio 1 2>/dev/null
tc filter add dev eth0 parent 1: prio 1 protocol 802.1q u32 match u16 0x0001 0x0FFF at -4 flowid 1:60
#OR (for ALL VLAN-tagged traffic): ... protocol 802.1q u32 match u32 0 0 flowid 1:60
tc filter del dev eth0 parent 1: prio 6 2>/dev/null
tc filter add dev eth0 parent 1: prio 6 protocol ip handle 6 fw flowid 1:60
# ... fix erroneous CONNMARK mask
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'connmark match ! 0x0/0xff00' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -m connmark ! --mark 0x0/0x7 -j RETURN
# ... fix hardcoded /24 netmask (e.g. for a 172.16.0.0/12 segment)
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'CONNMARK .* 172.16.0.0/24' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -d 172.16.0.0/12 -j CONNMARK --set-xmark 0x6/0x7
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'RETURN .* 172.16.0.0/24' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -d 172.16.0.0/12 -j RETURN
# ... fix erroneous LAN qdisc filter (-> match all VLAN ID 1 - LAN - traffic)
tc filter del dev eth0 parent 1: prio 1 2>/dev/null
tc filter add dev eth0 parent 1: prio 1 protocol 802.1q u32 match u16 0x0001 0x0FFF at -4 flowid 1:60
#OR (for ALL VLAN-tagged traffic): ... protocol 802.1q u32 match u32 0 0 flowid 1:60
tc filter del dev eth0 parent 1: prio 6 2>/dev/null
tc filter add dev eth0 parent 1: prio 6 protocol ip handle 6 fw flowid 1:60
# ... fix erroneous CONNMARK mask
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'connmark match ! 0x0/0xff00' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -m connmark ! --mark 0x0/0x7 -j RETURN
# ... fix hardcoded /24 netmask (e.g. for a 172.16.0.0/12 segment)
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'CONNMARK .* 172.16.0.0/24' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -d 172.16.0.0/12 -j CONNMARK --set-xmark 0x6/0x7
rnum="$(iptables --line-numbers -t mangle -nvL QOSO | grep 'RETURN .* 172.16.0.0/24' | cut -d' ' -f1)"
[ -n "${rnum}" ] && iptables -t mangle -R QOSO ${rnum} -d 172.16.0.0/12 -j RETURN
WARNING: This works on the RT-AC88U's kernel 2.6.36.4brcmarm (firmware 384.x); it may NOT work on 3.x or more recent kernels (tc syntax for VLAN filtering MUST then use basic match (meta vlan ID) syntax, which requires updated - ematch-able - tc/iproute2 tool)
This fixes:
- downloaded/ingress traffic no longer appears in the 1:40 ("low" priority) qdisc/class (throttled as per upload/egress bandwidth)
- INSTEAD, it appears in the 1:60 - LAN - qdisc/class (commissioned with a 1Gbit/s bandwidth)
- QOSO (mangle) chain properly RETURN when a connexion already has a (CONN)MARK
- other-than /24 LAN segments are properly (non-)QoS-ed (directed to the 1:60 - LAN - qdisc/class)
This does NOT fix:
- downloaded/ingress traffic throttling as per user-configured limits, since the ingress (ffff:) filter policies are apparently NOT used
Last edited: